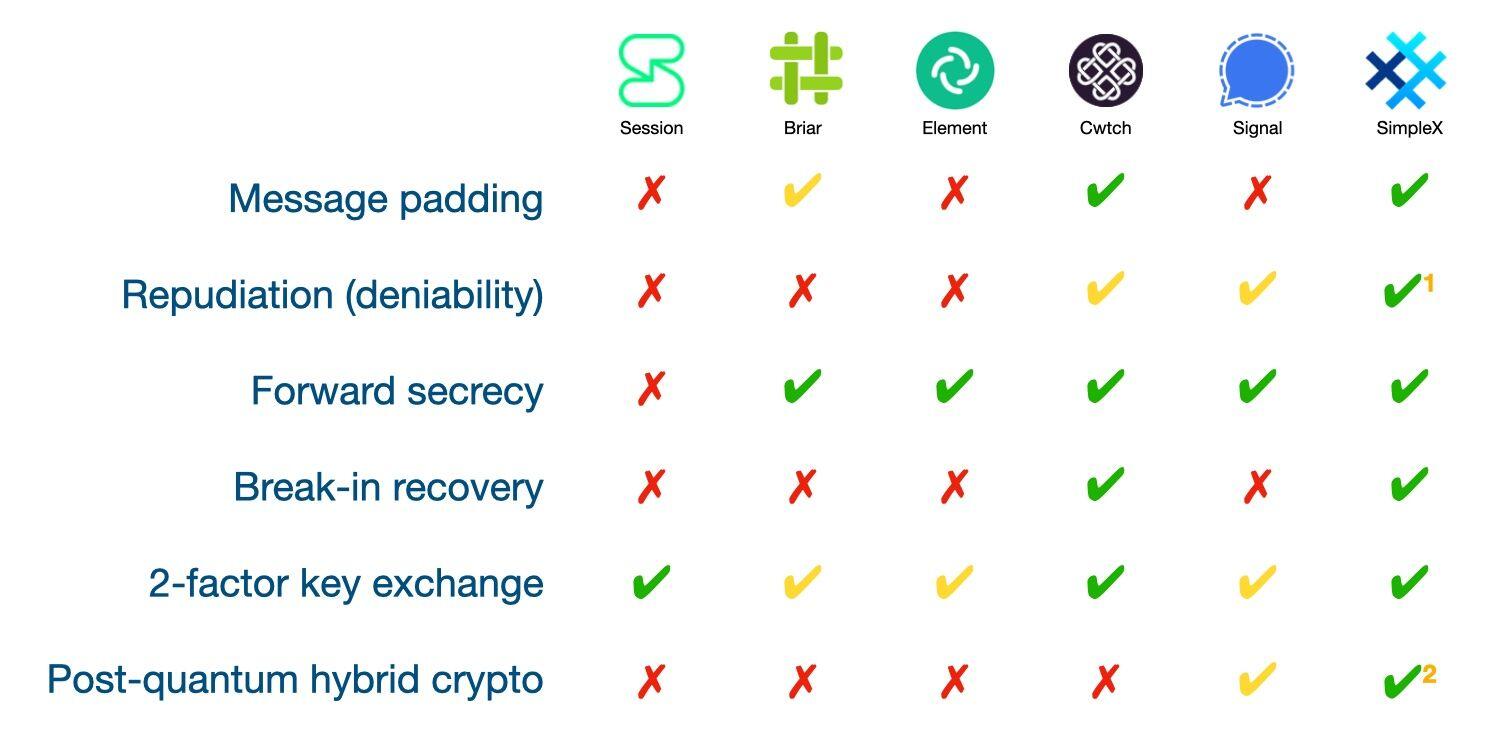
It's not planned, it's already there for quite a while, since they separated Session nodes from Oxen network.
They indeed refused to implement PFS at some point, and even had some logical explanation for this decision (can't recall what exactly it was, unfortunately, I guess it was somehow related to codebase ties with Oxen implementation). As of now, they've split from OX blockchain and they do indeed use extended triple Diffie-Hellman agreement (==PFS) in recent (1 year?) versions. What other features are lacking?
Few notes on this (and going to fork discussion by quoting you to maintain all due credits, if you don't mind).
1. Neither of these 4 are decentralized. By "decentralized" I specifically mean that the system does operate without ANY central infrastructure in peer2peer+DHT style, central server used for hash table bootstrap may be an acceptable compromise. Briar may be a good example of decentralized platform.
2. You're missing the context both in terms of threat model and use case, which makes the choice between the 4 pretty vague, like "just some 4 privacy messengers".
3. First question one should ask when choosing privacy tools: "Who's the adversary?" 2nd key question is individual definition of privacy.
4. Govt imposed blockings and restrictions are rapidly becoming problem #1 in private communications land and must be considered as a factor of platform choice.
5. Endpoint device is the most successful attack vector, in practice. Thus, features improving endpoint device security (e.g. "panic button") should be considered as well.
C'mon, he's one of the happiest deities, it's just not possible to be "dark" when wine is your domain. Happy Friday and don't drink too much, I'm watching you! 😁🍷
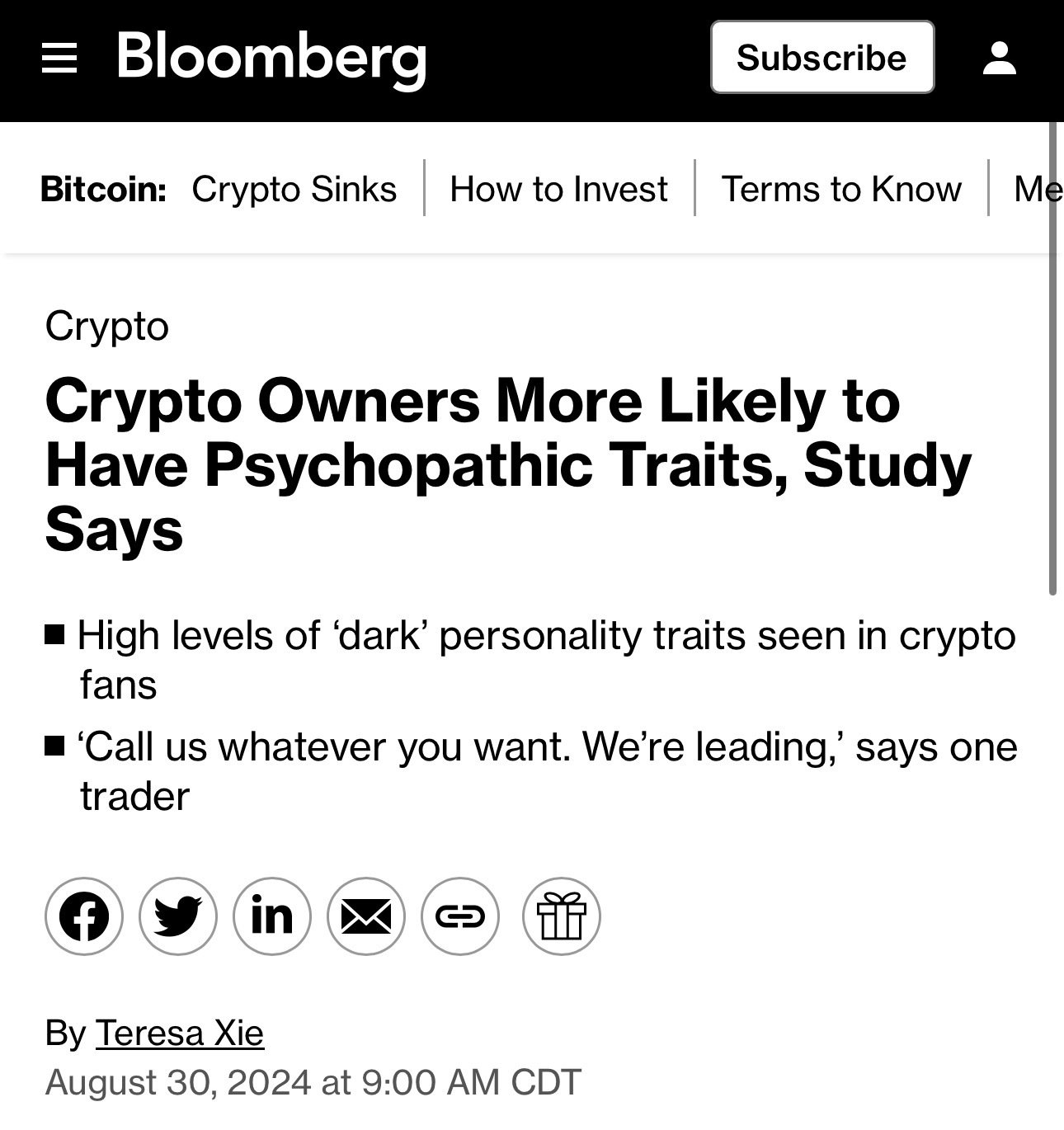
Did they say what exactly is considered "dark" traits?🫤
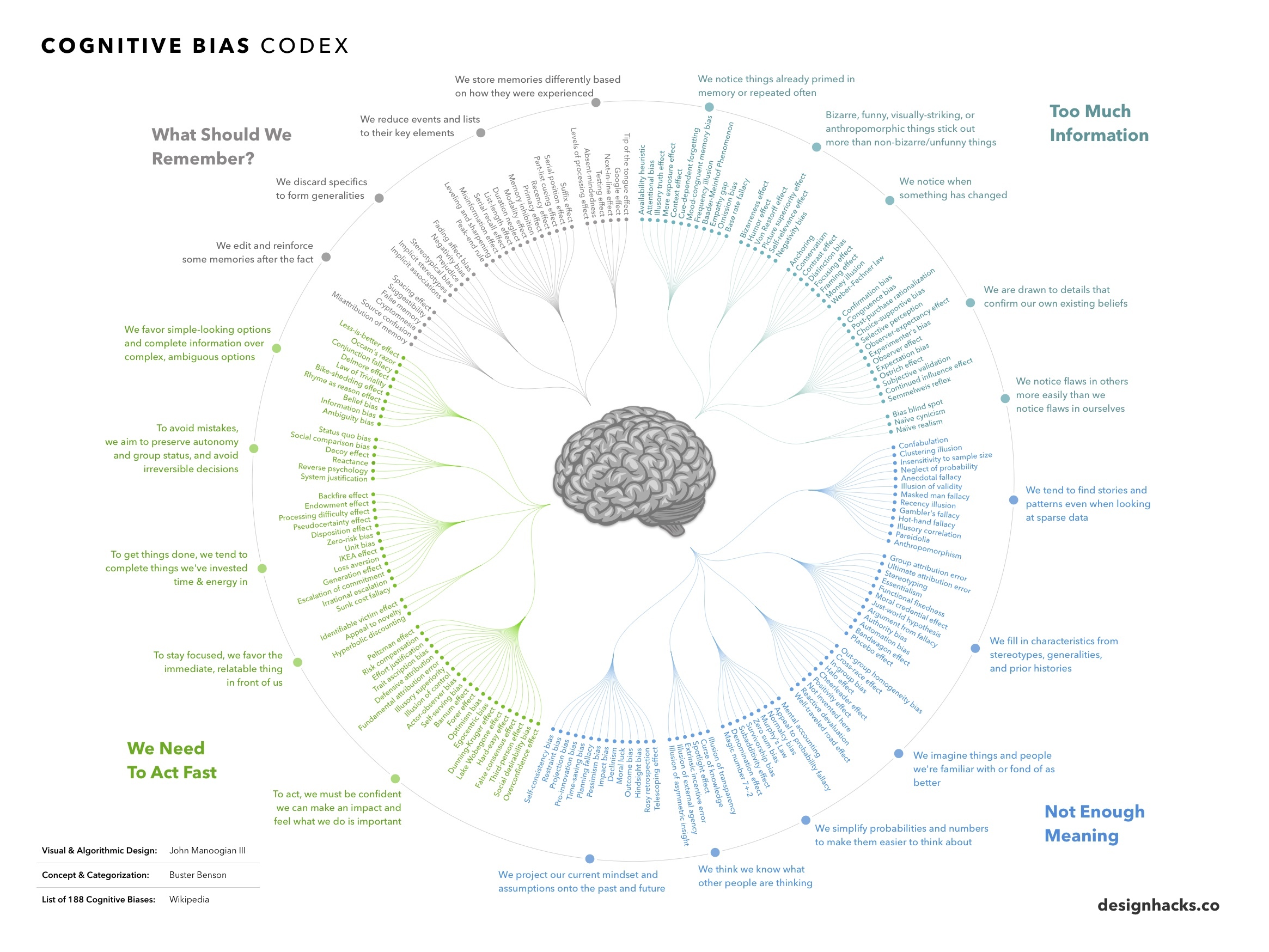
I would say it's about semiotics as a mean to overcome Shannon capacity theorem limitation, but it's lossy by default (that's the whole point!). Mind the difference between "simplifying" ("naming", as a matter of fact) and "understanding". From slightly different angle, it's an old good nominalism vs. realism debate.
Well, basically humans were never "designed" to process vast amounts of information unless it's social (or somehow projects to social dimension). Dominant encephalization theory is that neural capacity was required specifically to handle interactions in the group. It's kinda "hardware level".
Reply with system architecture diagram:)
"fiat currency is not backed by violence as many people think, it's actually backed by a captured economy" -- nostr:npub1mygerccwqpzyh9pvp6pv44rskv40zutkfs38t0hqhkvnwlhagp6s3psn5p
Violently captured I guess? ;)
It's not a simple case of non-compliance. I say it again, Telegram ecosystem is a deliberately designed honeypot, and thus, valuable resource for any government. He was aware French are formally after him, he had some vague intercourse with RU top just before the flight, and probably found out something. He already created and handed over one RU honeypot for internal use, VK, and thus, has connections with "siloviki" (you NEVER quit!). I would assume it's rather a deal than enforcement.
TON is receiving a lot of buzz and allegedly used for big stuff like RU sanctions circumvention.
It doesn't actually set a precedent, just confirms the trend.