This (finally) adds some amount of censorship resistance to LN Address, not to mention better security and (thanks to BOLT12) even allows users of custodial services to use their own domain for their address!
The full protocol (lightning-specific) protocol is implemented at https://git.bitcoin.ninja/index.cgi?p=lightning-resolver;a=summary nostr:note1gt9ryucy0eyn6gcez3vj5j2vgswsp70kz9mhk97egh54r4cjmzcsswpv06
I think it will not like me .. domain data is dinamically linked to well know people (kyc) .. many people on LN keep nodes behind tor addresses ... so this will work for identify user behind onion addresses? LN needs more anonymity , for example the node is disclosed on receipts; it would being need something help there, something like lnurl ; i think i'll never use it
You right ☺️
I'm not able to access https://nostrland2gdw7g3y77ctftovvil76vquipymo7tsctlxpiwknevzfid.onion/
is it my fault or is it down?
Anyway do you mean that relay track ips along http logs and they aren't inside any nostr protocol tag right?
i think that hiding ip is always better, however nostr design was censorship proof not privacy isn't? Nowdays i saw that nostr work well under tor, however some time ago it caused some issues i remember..
.. you give a finger and they took the arm .. it is the same principle of the boiled frog..
Ok, found the cause ... vanadium was listed under system apps while the app.vanadium.trichromelib stuff was different thing ...
...it worked in the past ..currently it seems that vanadium it is not working under tor using inviziblepro on vpn mode and selected app ; I'm on grapheneos
:) I saw that on last versions it has orbot option ...so very good ...
So ... I think that for this nodes network stability could it be the major issue? It would be interesting to understand if the network protocol used it is strong enough and if it recover after failures .. I have to say that using umbrel under onion with odroid m1 and nvme storage, with lnd it always worked well .. No routing node ..
I found amethyst extremely cool.. However I think that it miss of option to ask before open URLs. This could be dangerous .. And I was wondering if URLs preview get done by app using user own IP address .. I guess yes right? It would be useful a proxy option to protect by such things .. In the past I saw that running amethyst under tor wasn't so good experience , not sure if were the relays the issue .. Now things seems moving better because there are clients directly on tor network .. Also having option to see amethyst work directly on tor network (not by exit node) it would be very cool
#amethyst
I am tired of people running shity nodes on RPi. They are stubborn in not want to understand that their shity node crashing could affect the whole network.
When these people will learn that they can still run a PRIVATE node (with unannounced channels), that are enough to pay the beer/coffee over LN.
https://stacker.news/items/402904?commentId=402941
FFS throw that RPi node to the fucking garbage!

When people will understand that the weak point for RPi nodes is the DC card and the USB cable that is literally fucking the data drive?
BTC and LN require a huge traffic I/O for both SD card and the data drive (no matter you use SSD or HDD). The simple fact that the drive is NOT internal is fucking this I/O traffic. And your node always get fucked.
If you want to run a PUBLIC ROUTING node, then get a fucking SERIOUS machine, with INTERNAL drives and in RAID. Also have 100% good maintenance and a lot of liquidity.
FFS stop running public nodes with less than 1BTC liquidity!
I agree with that. Use private channels if you don't mind to route , and keep well working your node. However I'm corious what are the main failures that disrupt the network . hardware failures? Disrupted network connection ? Unbalanced channels?
Looking at... Thanks ...
But it seems not working on torbrowser without lowering security ...
 #m=image%2Fjpeg&dim=864x1068&blurhash=_46822of4noLWURkRj%3FvRkMxs%3AWBbGay%7EWWBNGoLIoj%5Bae_Ns%3ARPWVRPWBRjs9R*tQkBRjoeRkx%5DoJxaR%2BM%7BofRjozofxuWBafj%40RjxZWBWBj%5BofofRjShj%3FayayoeflWB&x=be6ddfad492e6c93da7df18a3c411f2495fbd05e74509078696b2e9cae584472
#m=image%2Fjpeg&dim=864x1068&blurhash=_46822of4noLWURkRj%3FvRkMxs%3AWBbGay%7EWWBNGoLIoj%5Bae_Ns%3ARPWVRPWBRjs9R*tQkBRjoeRkx%5DoJxaR%2BM%7BofRjozofxuWBafj%40RjxZWBWBj%5BofofRjShj%3FayayoeflWB&x=be6ddfad492e6c93da7df18a3c411f2495fbd05e74509078696b2e9cae584472
There are many dark points on monero ... It is unknown the pre-mined amount, it can't be verified like bitcoin. So it is not completely sure that it is not shitcoin, also if I have to say that it has his own because
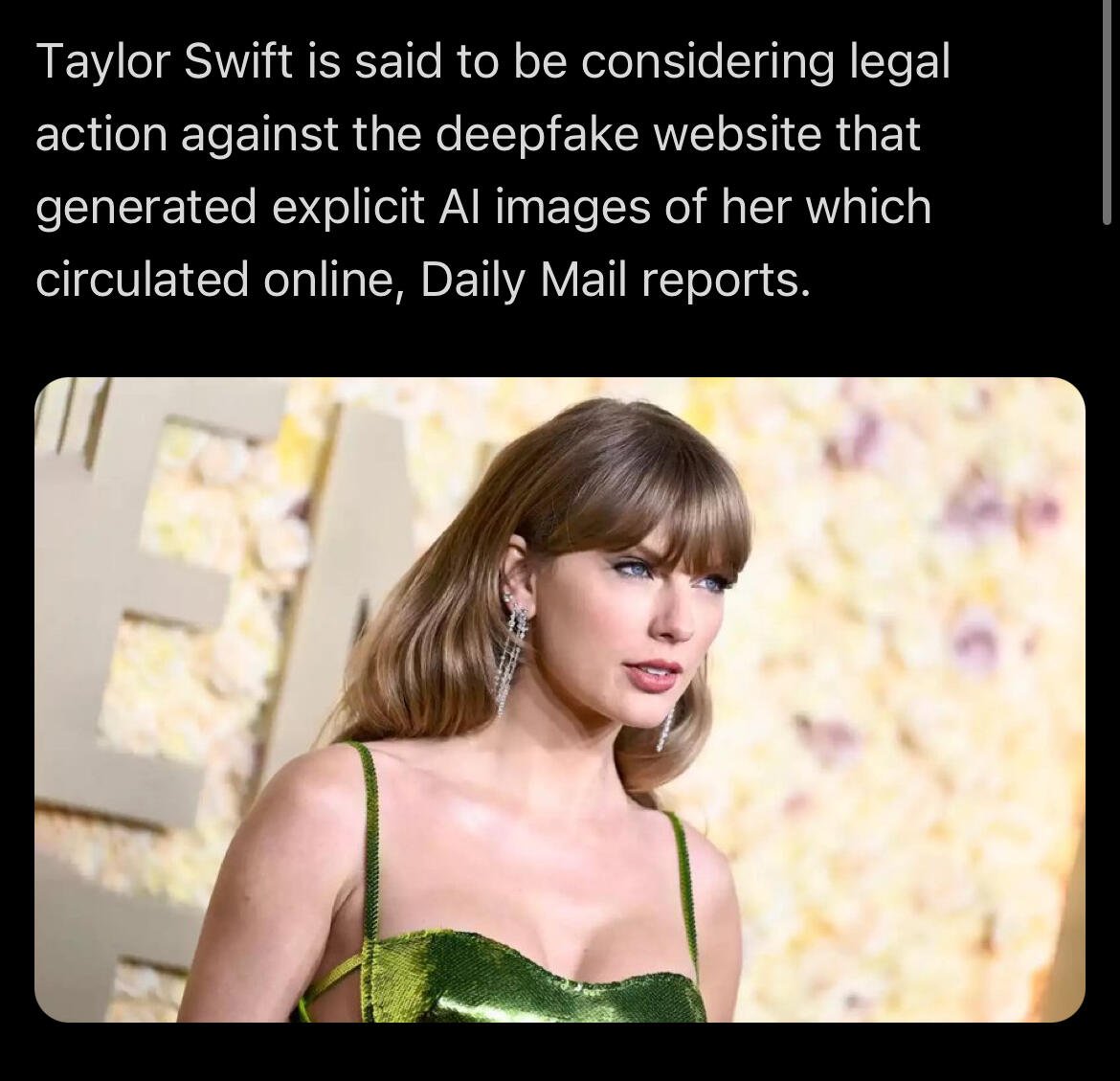
Well any prohibition law, is useless and could just do worst .. They invented the fake news to grow up propaganda, now they invented deep fake to force people to not believe in what they saw .. So let's use our brain to choose good from devil, we don't need something else that tell us what is right what is not. They are smiling because cause of those request from people asking for punishment and prison, they are going to introduce more restrictive and freedom killer laws. Stupid things and stupid people ever has been and ever will be ... It's the same, yesterday people played with Photoshop today they play with AI ... Should we prohibit Photoshop or AI ? I would say no ... People should develop self criticism , not asking police ,governments and other shit to imprison themselves ... It will be very worst when governments will force their models and their AI and their deep fake ...
What is your preferred p2p payment method and why? https://docs.bisq.network/payment-methods
#asknostr
I would like that yuh will become as popular as revolut: it has p2p payment too, it is not shitty as revolut that now allow to cancel transaction if the payer said to have been wrong :)
Inside A Global Phone Spy Tool Monitoring Billions
Comments ( https://news.ycombinator.com/item?id=39122281 )
https://www.404media.co/inside-global-phone-spy-tool-patternz-nuviad-real-time-bidding/
Trust on google stuff is drop to zero from many time ... Privacy is mandatory for daily use..
Yep,but I don't understand why btc is going down to 37k € ... So is there a scam? :)
Well I don't want to defend whatsapp , I have it restricted on graphene os work profile and I don't have meta ... However the article tells that it does not break e2e encryption and it only handle reported abuses ..
 #m=image%2Fgif&dim=360x360&blurhash=U7B%7By6JC00%7D%40MKIpPV-U%25N%24%23MxIo0Ls.%5EkI%40&x=7ca64596798d52d8d04e9a72fae20d32b7d94772c643af46a71cbdf5c551782f
#m=image%2Fgif&dim=360x360&blurhash=U7B%7By6JC00%7D%40MKIpPV-U%25N%24%23MxIo0Ls.%5EkI%40&x=7ca64596798d52d8d04e9a72fae20d32b7d94772c643af46a71cbdf5c551782f