> and irrelevant in most cases
It is highly relevant when you're being tracked by authorities. They typically start by sending you some money and then watching what happens to it next on the blockchain. E.g. that's what they did in this case where they traced a finnish man's monero: https://cointelegraph.com/news/finnish-authorities-traced-monero-vastaamo-hack
And in the Columbian case (where they ALSO traced a guy's monero) they also relied on the ability of the sender (in this case, Morphtoken) to point out exactly where he sent the money: https://cointelegraph.com/news/chainalysis-leak-monero-traceability
Lightning fixes this.
The simple fact is, on lightning, the sender can't trace his own payment, but on monero, he can, and this difference helps authorities arrest monero users.
Don't miss the exciting conclusion to this little drama! nostr:nevent1qqsdpyuve6csqe30ej6rtusftcc3z4xxae8xdaqjlz77kqhzzluwlgcpzemhxue69uhhyetvv9ujumn0wd68ytnzv9hxgq3qyxp7j36cfqws7yj0hkfu2mx25308u4zua6ud22zglxp98ayhh96st6xzz5
What an interesting experiment! Due to the imperfect receiver privacy of monero, I am able to identify the exact address where he received money as well as the exact amount in that address. I can also watch the blockchain to see if it shows up as a possible spender in a future transaction. Neat stuff! Now let's wait and find out: can nostr:nprofile1qqs27aqdrx96hwx8hqks53ccav65hvlk47dfscumsh22tncnw89t4pgppemhxue69uhkummn9ekx7mp0qy2hwumn8ghj7un9d3shjtnyv9kh2uewd9hj7qghwaehxw309aex2mrp0yhxummnw3ezucnpdejz7q7z90p tell me similar info for the LN payment he sent to me? Stay tuned! 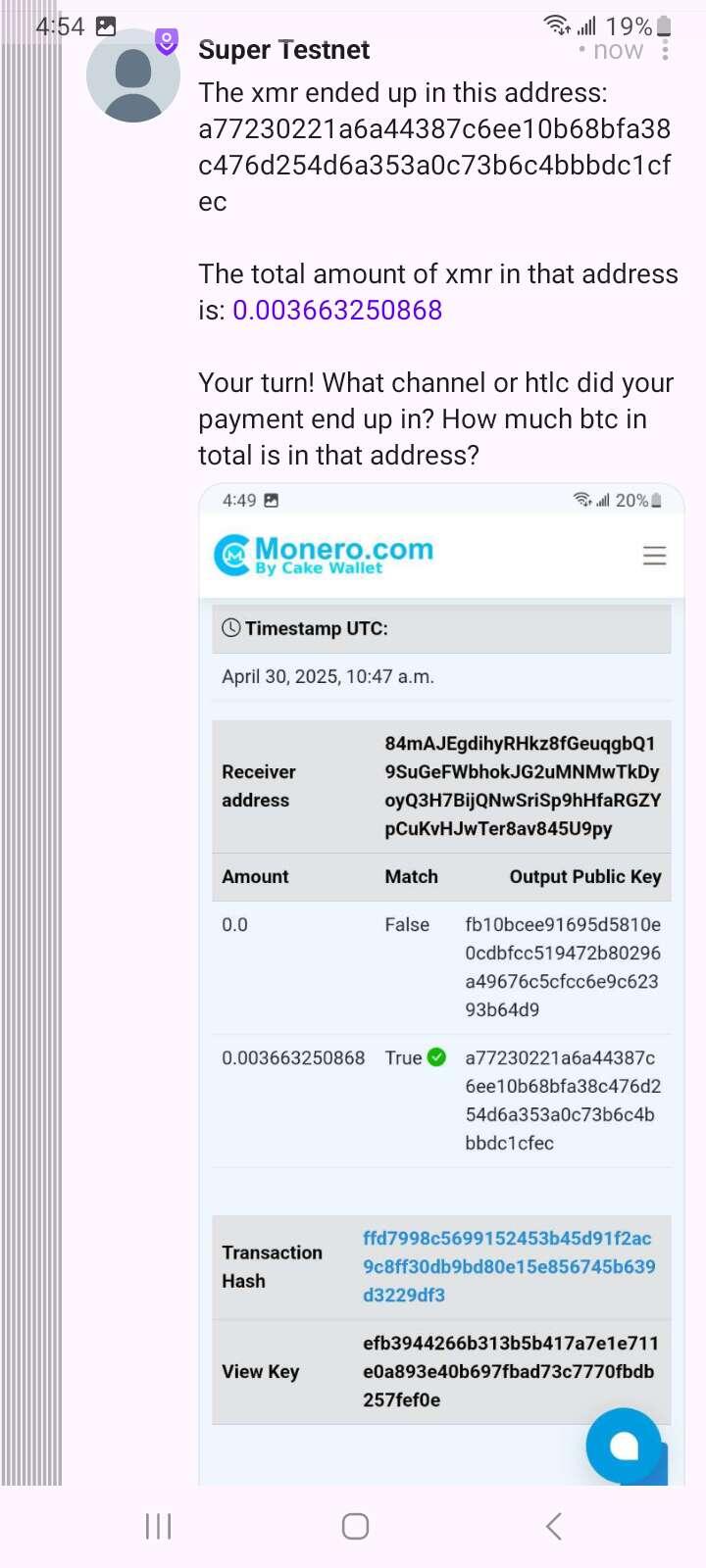
What a conclusion! I traced the XMR and identified its destination AND the total amount in that address on monero. nostr:npub14a6q6xvt4wuv0wpdpfr336e4fweldtu6np3ehpw55h83xuw2h2zsgyz6rn meanwhile, could not trace my BTC or identify its destination or the total amount in the channel where it ended up. Is XMR worse than LN after all?
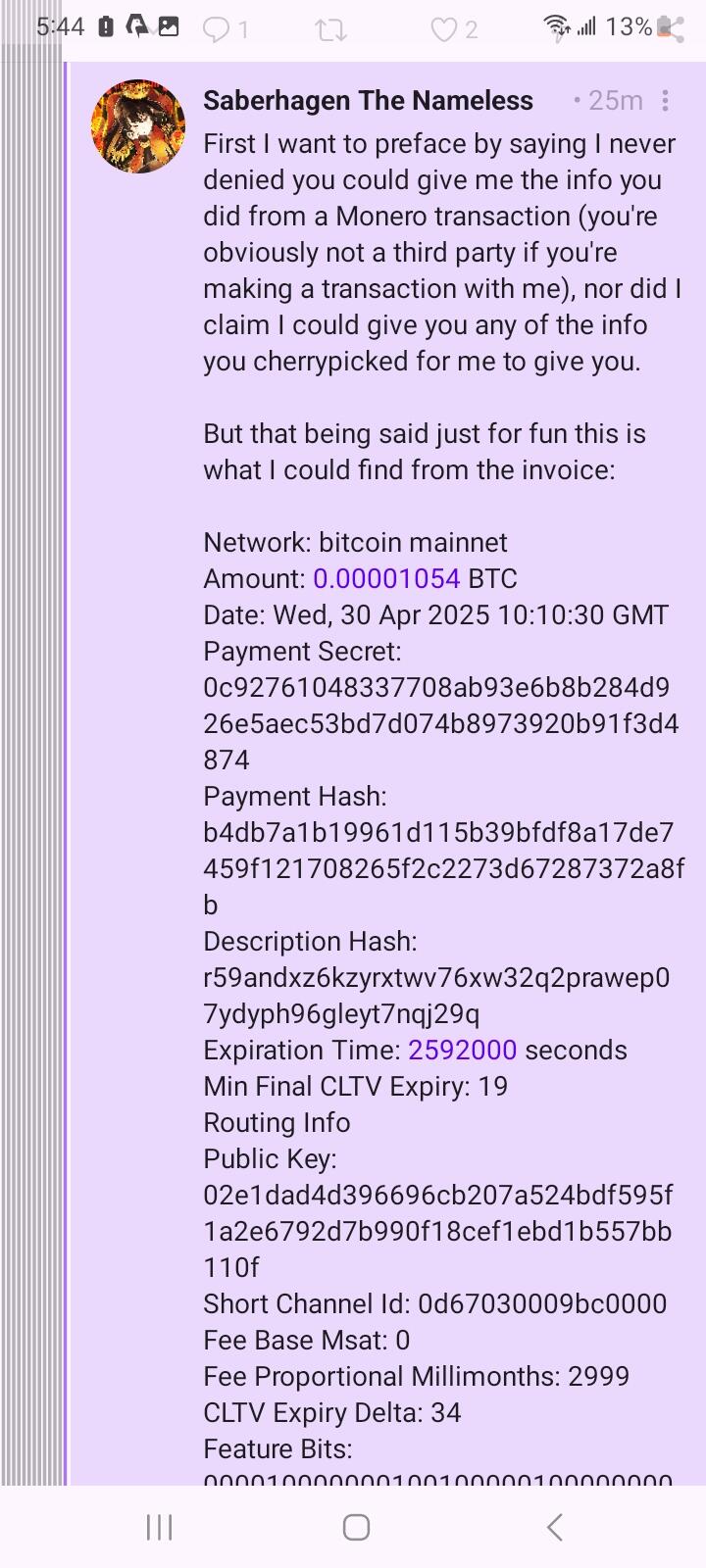
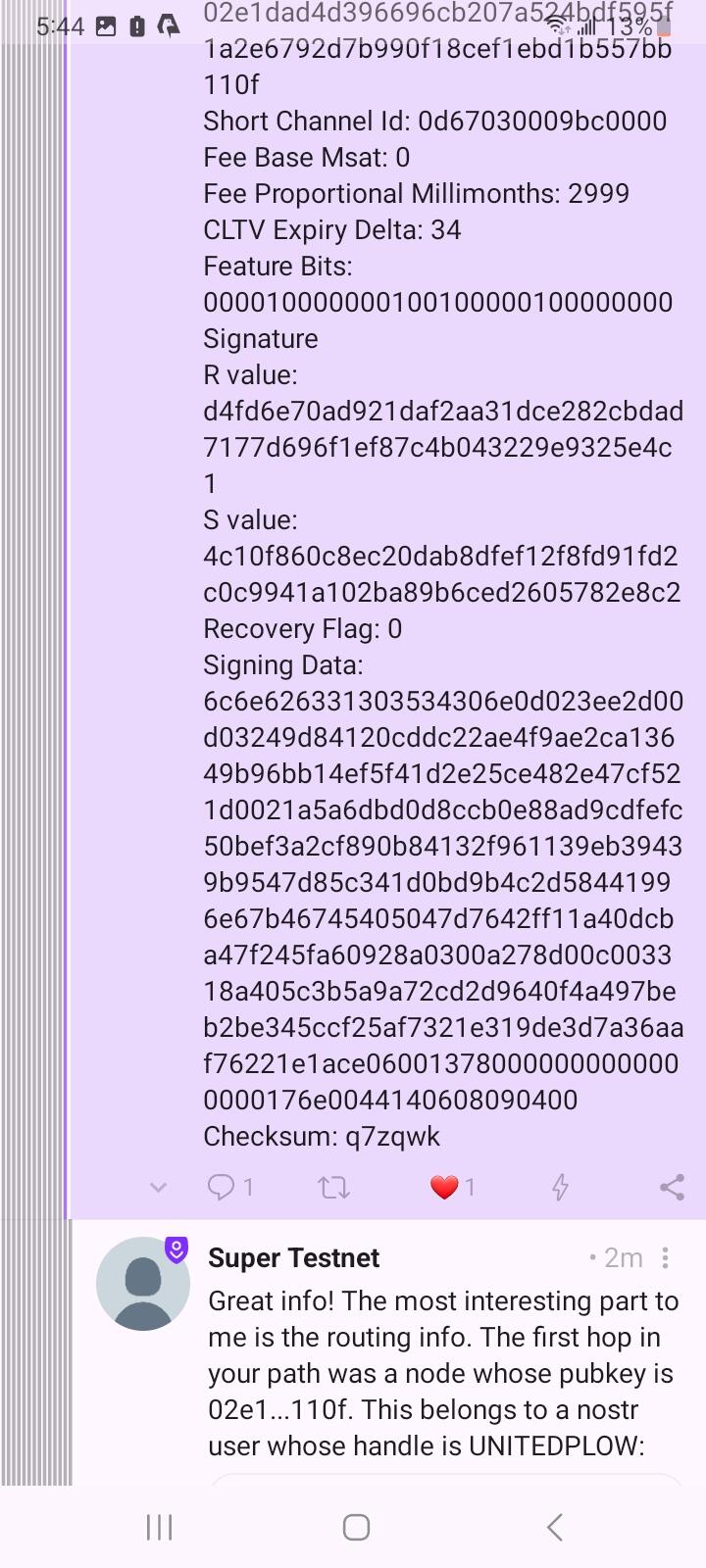
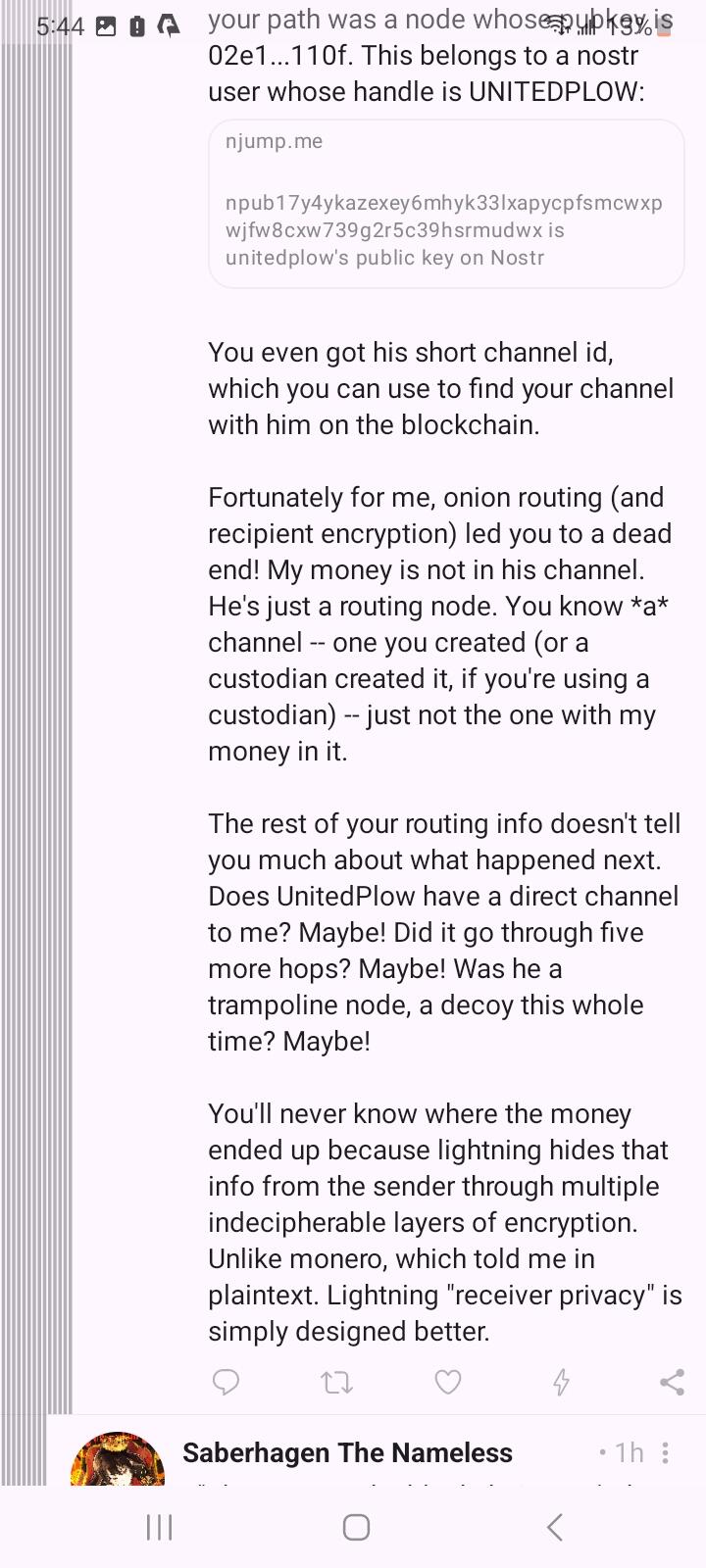
Great info! The most interesting part to me is the routing info. The first hop in your path was a node whose pubkey is 02e1...110f. This belongs to a nostr user whose handle is UNITEDPLOW: https://njump.me/npub17y4ykazexey6mhyk33lxapycpfsmcwxpwjfw8cxw739g2r5c39hsrmudwx
You even got his short channel id, which you can use to find your channel with him on the blockchain.
Fortunately for me, onion routing (and recipient encryption) led you to a dead end! My money is not in his channel. He's just a routing node. You know *a* channel -- one you created (or a custodian created it, if you're using a custodian) -- just not the one with my money in it.
The rest of your routing info doesn't tell you much about what happened next. Does UnitedPlow have a direct channel to me? Maybe! Did it go through five more hops? Maybe! Was he a trampoline node, a decoy this whole time? Maybe!
You'll never know where the money ended up because lightning hides that info from the sender through multiple indecipherable layers of encryption. Unlike monero, which told me in plaintext. Lightning "receiver privacy" is simply designed better.
Oops, sorry! You said "better UX for privacy," not "better privacy." Well, I was able to use that slick privacy UX to dox one of your one-time-use addresses as well as the exact amount of xmr in it. Your turn: can you dox my lightning channel and the exact amount of btc in it? We're waiting! Let's find out if the privacy UX of monero really is as good as you say!
What an interesting experiment! Due to the imperfect receiver privacy of monero, I am able to identify the exact address where he received money as well as the exact amount in that address. I can also watch the blockchain to see if it shows up as a possible spender in a future transaction. Neat stuff! Now let's wait and find out: can nostr:nprofile1qqs27aqdrx96hwx8hqks53ccav65hvlk47dfscumsh22tncnw89t4pgppemhxue69uhkummn9ekx7mp0qy2hwumn8ghj7un9d3shjtnyv9kh2uewd9hj7qghwaehxw309aex2mrp0yhxummnw3ezucnpdejz7q7z90p tell me similar info for the LN payment he sent to me? Stay tuned! 
The xmr ended up in this address: a77230221a6a44387c6ee10b68bfa38c476d254d6a353a0c73b6c4bbbdc1cfec
The total amount of xmr in that address is: 0.003663250868
Your turn! What channel or htlc did your payment end up in? How much btc in total is in that address? 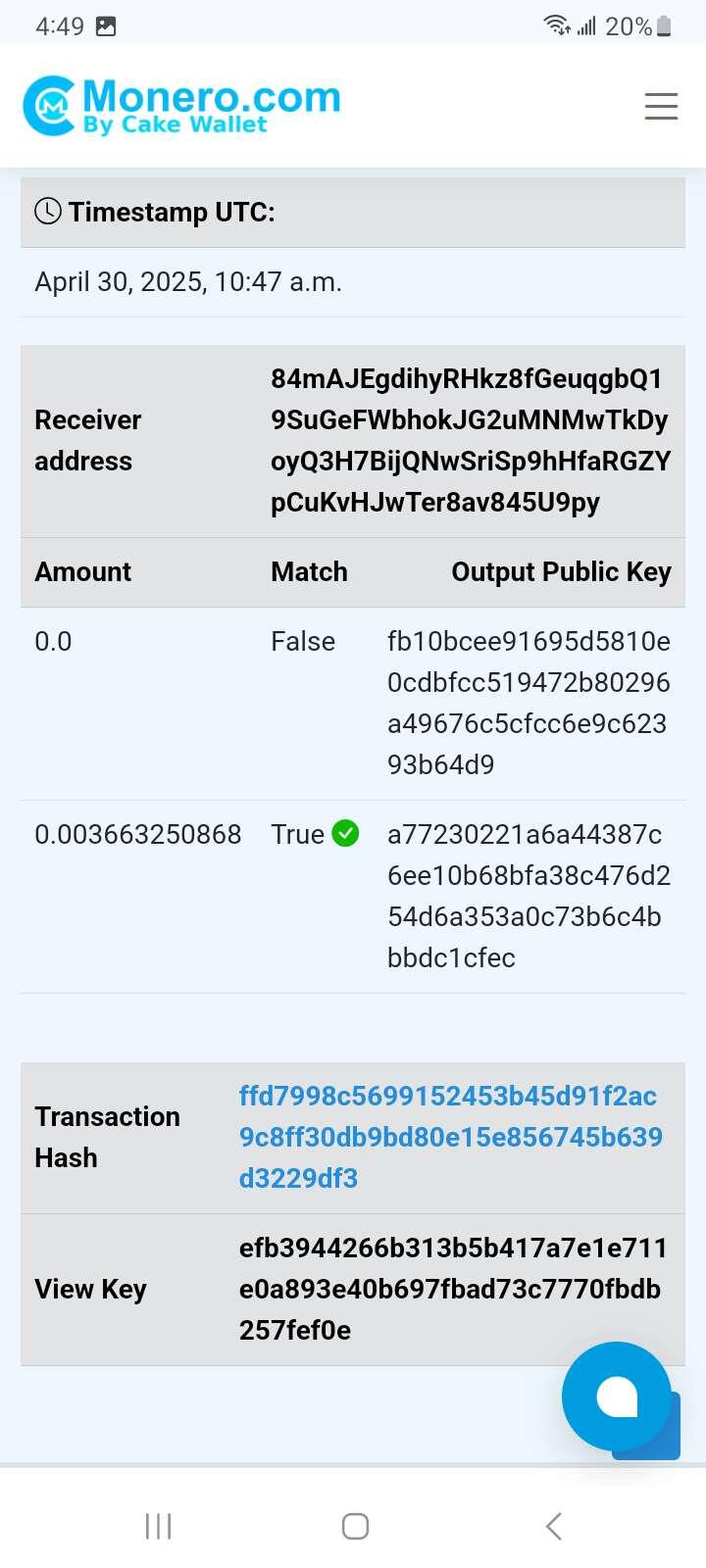
> you can't send 100,000 dollars on LN
Who says? There is widespread deployment of LSPs with dozens of btc in capacity. It should go through just fine. Not even a slight problem.
Monero user nostr:nprofile1qqs27aqdrx96hwx8hqks53ccav65hvlk47dfscumsh22tncnw89t4pgppemhxue69uhkummn9ekx7mp0qy2hwumn8ghj7un9d3shjtnyv9kh2uewd9hj7qghwaehxw309aex2mrp0yhxummnw3ezucnpdejz7q7z90p says monero has better receiver privacy than lightning. I issued him a challenge. Will he accept it? 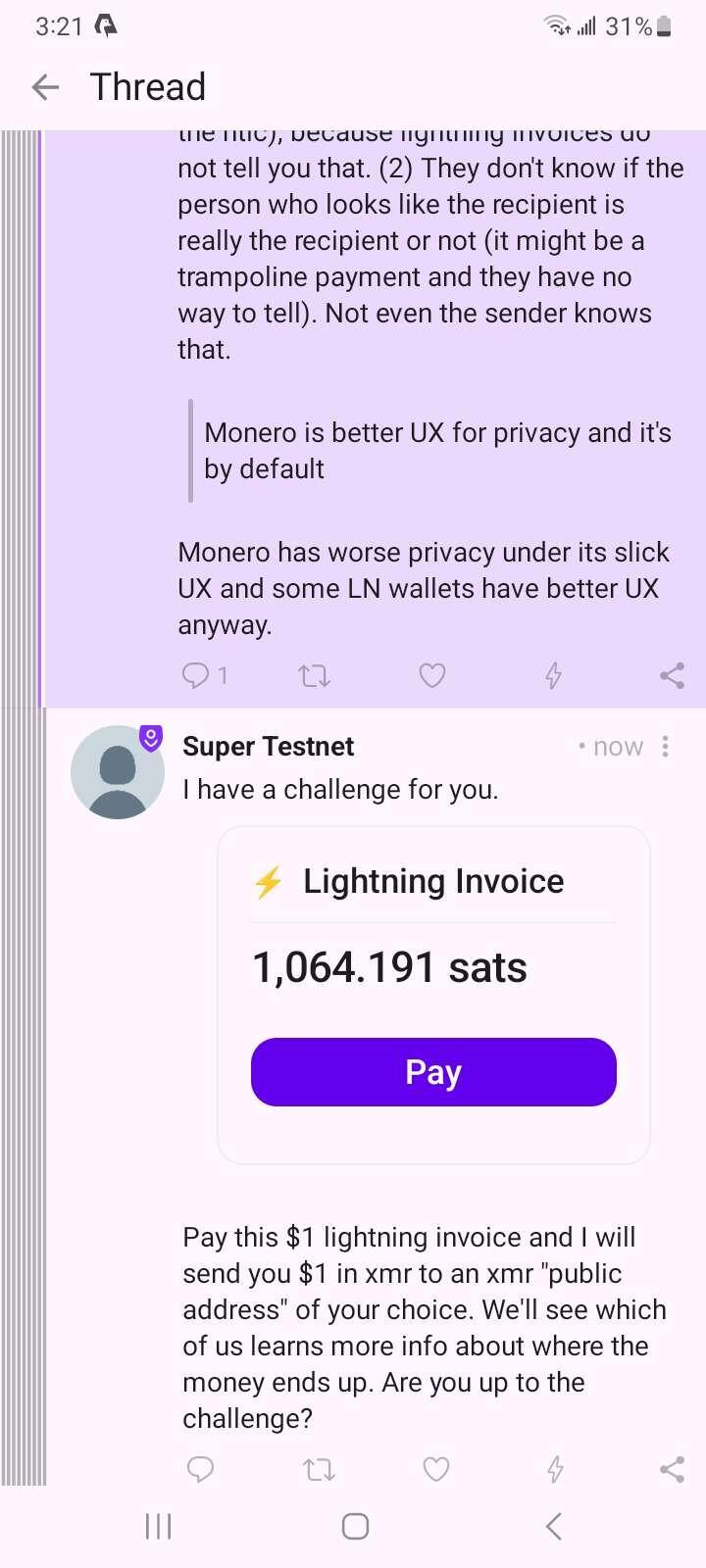
I specified the challenge a bit more:
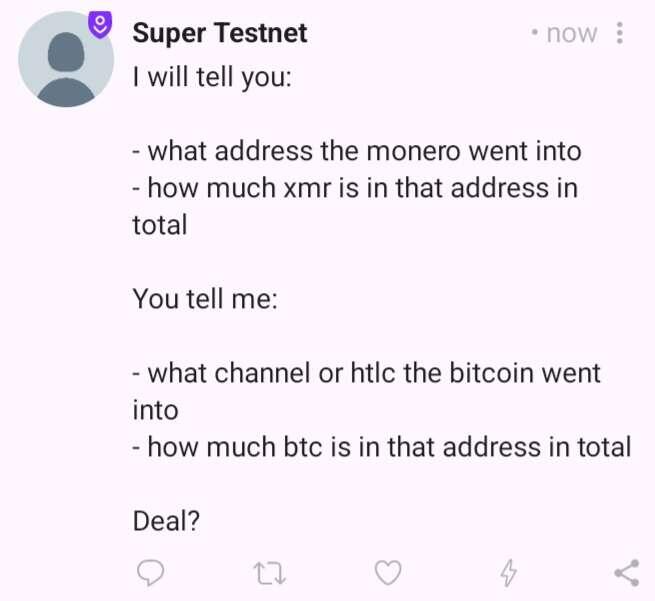
I will tell you:
- what address the monero went into
- how much xmr is in that address in total
You tell me:
- what channel or htlc the bitcoin went into
- how much btc is in that address in total
Deal?
Monero user nostr:nprofile1qqs27aqdrx96hwx8hqks53ccav65hvlk47dfscumsh22tncnw89t4pgppemhxue69uhkummn9ekx7mp0qy2hwumn8ghj7un9d3shjtnyv9kh2uewd9hj7qghwaehxw309aex2mrp0yhxummnw3ezucnpdejz7q7z90p says monero has better receiver privacy than lightning. I issued him a challenge. Will he accept it? 
I have a challenge for you. lnbc10641910p1p5pr6klpp5refgj5cv3k0zajlcz8hztfz4sezcv9e7hfwkv2z99m0p2mwx64dqhp5uwcvgs5clswpfxhm7nyfjmaeysn6us0yvjdexn9yjkv3k7zjhp2scqzdyxqyjwf3sp55u5qqhs88t5e5ag0d6gvacjkhfk5l7jdxc6usewu4xy8tp7y8xss9qxpqysgq0tcz422qrphc27m6xukk4xgjaawgp5ae003805wr9g3n4jrhp3hypd5tn2qj4smrc43fcfyjwlvpms0ydcjl7wchdpy2q4rst46e6ygp2vaqna
Pay this $1 lightning invoice and I will send you $1 in xmr to an xmr "public address" of your choice. We'll see which of us learns more info about where the money ends up. Are you up to the challenge?
> Should be easy since my Monero address is on my profile.
The ones on the blockchain aren't the same as the one in your profile. Nonetheless, it's better to (1) not publish them (2) encrypt them so that fewer people can see them. You know, like lightning does.
> Lightning nodes on a route (aka third parties) can see exact amounts passing through them. Nodes on Monero can't.
In both cases they get partial amount information. Monero leaves the fee unencrypted and in fact publishes it for all to see, and this is one of the tools chain analysts use to fingerprint what type of wallet you're using. Lightning does not publish the amount info, the routing nodes only get a lower bound on the amount sent; they don't know the full amount because they don't know if a multipath payment was used, and they also don't know the total fee paid because that's encrypted -- each routing node only knows how much you paid *them.*
> most LN payments are routed through a handful of large hubs
...he said, with no evidence
> ~90% of Lightning users don't enjoy almost any of the privacy benefits you lay out because they're using things like Wallet of Satoshi or Strike that see everything
Wallet of Satoshi and Strike don't see everything. Here's two critical details they're in the dark about: (1) they don't know what address the recipient receives the money into (neither the channel nor the htlc), because lightning invoices do not tell you that. (2) They don't know if the person who looks like the recipient is really the recipient or not (it might be a trampoline payment and they have no way to tell). Not even the sender knows that.
> Monero is better UX for privacy and it's by default
Monero has worse privacy under its slick UX and some LN wallets have better UX anyway.
making it cost more is also a good outcome
Yep! More private than monero for a lot of reasons:
- lightning invoices reveal less information than monero addresses
- in lightning transactions, the sender is encrypted (unlike monero, which uses 15 unencrypted decoys and 1 unencrypted real spender, and just hopes analysts can't eliminate the decoys)
- in lightning, the full amount is encrypted (unlike monero, which leaves the fee in plaintext)
- in lightning, the recipient is encrypted (unlike monero, which typically leaves the recipient's address and a change address in plaintext, though it does randomize their order, which is good)
- none of that data is published on a blockchain (unlike monero, where it is)
Monero does some pretty good things for your privacy and I can only identify the "real" sender of a monero transaction in about 1/5 cases, and only with about 80% confidence. Chain analytics companies can do a lot better because they have off-chain data that helps them eliminate more decoys. But by comparison with lightning, monero is pretty transparent.
They created a sidechain model which requires some data about the sidechain to be accessible to users. Their model also involves a federation and I think it is perfectly reasonable to have each of the federation members store a copy of that data, but instead Citrea opted to dump it on bitcoin's blockchain to reduce the chance of it disappearing.
The exchanges do but there are plenty of wallets that let you receive and send them without KYC. And there are p2p exchanges that do not do KYC where stablecoins can be acquired.
Of couse, in my opinion anyone who's willing to go through all of that trouble just to acquire a stablecoin really ought to consider bitcoin instead.
Yes, there are two groups of people doing this:
(1) Stamps: https://www.ledger.com/academy/glossary/bitcoin-stamps
(2) Citrea: https://citrea.xyz/clementine_whitepaper.pdf
The Citrea paper is quite dense but I am referring to this sentence in particular: "A total of 144 bytes are committed, split into 3 outputs, one OP RETURN with 80 bytes of data and two taproot outputs with their script pubkey as the 32 byte data, making these outputs unspendable."
Yes but this isn't trying to make sure you can spend the money in the future, only that you're not making a fake address that simply encodes 32 bytes of data without actually being spendable -- i.e. it ensures you're not abusing bitcoin outputs in the particular manner Stamps and Citrea do it
I don't think this would make receiving harder than just pushing the Receive button. The wallet just has to sign a tx, that's very easy.
As for multisig wallets, it's the same: the devices belonging to the keyholders just do this when they generate their key, and they simply send the result (key+signature) to whoever's making the multisig. The multisig creation software includes the proof with the multisig address. Then whoever wants to send money to them just does what they do currently: scan a qr code or copy-paste the address (which includes the proof), and their wallet does the rest.
A clear downside is that it's harder to make a wallet when every time you make a pubkey you must also sign a message with it. But I don't think that makes it harder for the user, not even a multisig user -- they just click Receive (or Export Multisig Key) and their wallet does everything else.
Addresses would get longer but I'm not sure how significant of a drawback that is.
I am not endorsing this idea but I am bringing attention to it because it sounds like a fun way to fight Citrea and Stamps:
Modify bitcoin core to enforce a mempool policy that rejects transactions that put money in addresses without including a proof that each address can be spent from. The proof doesn't go in the blockchain, it's just relayed with the tx to prove its outputs are spendable.
This would require wallets to create the proof when generating an address and share the proof with the sender. It would also require multisig wallets to use some sort of coordination mechanism to produce the proof. But it requires no consensus changes.
User flow: Alice wants to send money to Bob. Alice asks Bob for an address. Bob's wallet not only generates the address, but also signs the message "Proof of Spendable" with his private key and shares the signature with Alice, in the same qr code as his address. Alice's wallet scans the qr code and constructions a tx paying Bob's address, and when it sends the transaction to the mempool, it shares Alice's signature along with it.
Nodes only propagate the transaction through the network after verifying the signature so that they know Alice can actually spend the money in that address, meaning it's not just a data carrier. Stamps and Citrea, RIP.
I oppose stablecoins but I suppose in America people who don't want to do KYC but still want digital cash might prefer stablecoins over Paypal, Venmo, or Cash App, all of which do KYC on their users
I think such people should try bitcoin, of course
