Anything interesting? I have to admit I have written bluesky off almost completely.
https://dustycloud.org/blog/how-decentralized-is-bluesky/ is utterly damning (although the author is very sympathetic to bluesky as a twitter alternative)
Ah ok, I discovered there's a subforum I don't have access to, I was wondering if you had access.
You don't wanna dogfood DMs in coracle? 😂
Sent! Subject line might be easy to mistake for spam but it should be obvious it's my email address.
I keep hoping somebody will pick up https://github.com/twilco/kosmonaut and productize it. No idea how to ethically fund it besides e-begging though...
nostr:nprofile1qyvhwumn8ghj76rzwghxxmmjv93kcefwwdhkx6tpdshsz9thwden5te0wfjkccte9ejxzmt4wvhxjme0qy88wumn8ghj7mn0wvhxcmmv9uq3vamnwvaz7tm9v3jkutnwdaehgu3wd3skuep0qyg8wumn8ghj7mn0wd68ytnddakj7qpqjlrs53pkdfjnts29kveljul2sm0actt6n8dxrrzqcersttvcuv3qs6ulkk sorry to be obnoxious but I shot you a DM that's semi time sensitive. (not any kind of security issue)
That was my exact reaction.
#FreeRoss Thank God he's free!
Now if only we could free him from this new sentence...

I'm not even a little surprised, but I'm still disappointed...
nostr:nprofile1qyw8wumn8ghj76r0v3kxymmy9e3k7unpvdkx2tn5dahkcue0qy88wumn8ghj7mn0wvhxcmmv9uq32amnwvaz7tmjv4kxz7fwv3sk6atn9e5k7tcpzemhxue69uhkummnw3ezumtfd3hh2tnvdakz7qghwaehxw309ashgmrpwvhxummnw3ezumrpdejz7qpqjlrs53pkdfjnts29kveljul2sm0actt6n8dxrrzqcersttvcuv3q0rmwe9 did you fix something with caching websocket connections or something? Over the past month or so I stopped using coracle (and nostr) because I was being assaulted with 22242 signing requests, and now I'm not (or at least it's tolerable now).
Bonus informal bug report ;-)
nostr:nprofile1qyw8wumn8ghj76r0v3kxymmy9e3k7unpvdkx2tn5dahkcue0qy88wumn8ghj7mn0wvhxcmmv9uq32amnwvaz7tmjv4kxz7fwv3sk6atn9e5k7tcpzemhxue69uhkummnw3ezumtfd3hh2tnvdakz7qghwaehxw309ashgmrpwvhxummnw3ezumrpdejz7qpqjlrs53pkdfjnts29kveljul2sm0actt6n8dxrrzqcersttvcuv3q0rmwe9 did you fix something with caching websocket connections or something? Over the past month or so I stopped using coracle (and nostr) because I was being assaulted with 22242 signing requests, and now I'm not (or at least it's tolerable now).
I really wish nos2x had some kind of support for understanding what it's signing. Like a template that says "you can always sign an event that looks like this, with this varying part" or something. Specifically thinking of how I get prompted to sign like 30 22242 events, but as long as it's to a relay I've pre-approved I'm ok auto-approving. (nos2x kind of does this already, but it only keeps track of the kind, but I don't want to blanket allow 22242s)
Is there a legal defense fund for good samaritans willing to disobey inhuman federal edicts in order to help people affected by helene? Seems like a good cause. nostr:nprofile1qy88wumn8ghj7mn0wvhxcmmv9uq32amnwvaz7tmjv4kxz7fwv3sk6atn9e5k7tcpz9mhxue69uhkummnw3ezuamfdejj7qgcwaehxw309aex2mrp0yhxxatjwfjkuapwveukjtcpzemhxue69uhk2er9dchxummnw3ezumrpdejz7qpqh8nk2346qezka5cpm8jjh3yl5j88pf4ly2ptu7s6uu55wcfqy0wq0dknp4 nostr:nprofile1qyvhwumn8ghj7un9d3shjtnndehhyapwwdhkx6tpdshszrnhwden5te0dehhxtnvdakz7qgkwaehxw309ajkgetw9ehx7um5wghxcctwvshszgrhwden5te0vf5hgcm0d9hx6ctcd9kkzmrfwd68xtn0dekxjmn99uq32amnwvaz7tmwdaehgu3wdau8gu3wv3jhvtcqyprj73q098hejm5j5xrt35eqluvqep2eqwyzukw4phsm302kdycpu86e9k2
If it gets well funded, either there's enough money for everyone, or if there isn't enough money, that implies a pretty large amount of civil disobedience.
nostr:nprofile1qyw8wumn8ghj76r0v3kxymmy9e3k7unpvdkx2tn5dahkcue0qy2hwumn8ghj7un9d3shjtnyv9kh2uewd9hj7qgwwaehxw309ahx7uewd3hkctcprdmhxue69uhhyetvv9ujuam9wd6x2unwvf6xxtnrdakj7qpqjlrs53pkdfjnts29kveljul2sm0actt6n8dxrrzqcersttvcuv3q87k8ew I don't know if it changed but this is what the response from nos2x is. Why is coracle trying to use nip44 encryption to update my follow list? I do have encryption denied right now so it's correct that nos2x is denying the request.
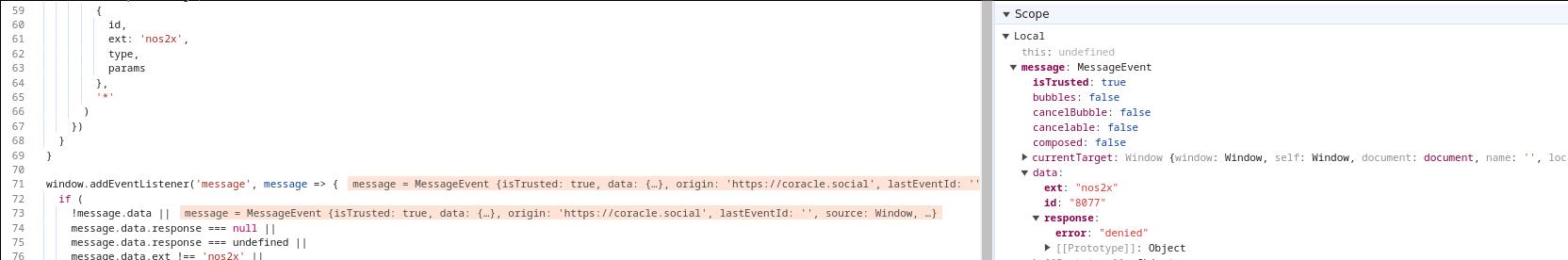
Oh wait, that's in the nos2x client library anyway lol, so yeah I guess it's a nos2x bug?
nostr:nprofile1qyw8wumn8ghj76r0v3kxymmy9e3k7unpvdkx2tn5dahkcue0qy2hwumn8ghj7un9d3shjtnyv9kh2uewd9hj7qgwwaehxw309ahx7uewd3hkctcprdmhxue69uhhyetvv9ujuam9wd6x2unwvf6xxtnrdakj7qpqjlrs53pkdfjnts29kveljul2sm0actt6n8dxrrzqcersttvcuv3q87k8ew I don't know if it changed but this is what the response from nos2x is. Why is coracle trying to use nip44 encryption to update my follow list? I do have encryption denied right now so it's correct that nos2x is denying the request.



