Two significant-ish "akshually"s but also a DEFENSE of nostr:npub10pensatlcfwktnvjjw2dtem38n6rvw8g6fv73h84cuacxn4c28eqyfn34f in regards to nostr:npub17tyke9lkgxd98ruyeul6wt3pj3s9uxzgp9hxu5tsenjmweue6sqq4y3mgl.
On nostr:npub10uthwp4ddc9w5adfuv69m8la4enkwma07fymuetmt93htcww6wgs55xdlq #320, nostr:npub1qny3tkh0acurzla8x3zy4nhrjz5zd8l9sy9jys09umwng00manysew95gx said:
"There's multiple conspiracies with OpenSats and two of the key ones is Knots and SeedSigner. And neither have submitted applications. If you're a developer or a contributor working on either of those things, opensats.org/apply"
Akshually:
1.) SeedSigner DID submit an OpenSats application for the project as a whole. The application languished for months (perhaps 6mo to a year?) and was ultimately declined with the explanation that it was easier/preferable to support individual devs than whole projects.
2.) Based on that feedback, I submitted an OpenSats application to fund just me specifically. That was also declined. BUT the rationale was because nostr:npub17xvf49kht23cddxgw92rvfktkd3vqvjgkgsdexh9847wl0927tqsrhc9as had just announced a 6mo grant for me. I was encouraged to reapply to OpenSats before that HRF funding expired.
The delays around 1.) were totally understandable. OpenSats is a VOLUNTEER effort and had even fewer human resources at that time. But also: they don't owe us a f'n thing!! They're under no obligation to say "Yes" nor should we ever have the arrogance to think we deserve to demand a "Yes"!
BUT the delays to get to ANY answer were VERY frustrating and likely added to some of the bad blood in the water amongst those watching the project closely. Eventually each "later, soon..." response was received with increasing cynicism and creeping conspiracy theories.
The "No" was totally reasonable. Getting to "No" faster would have been better.
The "No" on 2.) was also totally reasonable. No complaints from me whatsoever. I also strongly believe that THEY WOULD HAVE BEEN A "YES" had the HRF funding not come through.
I consider O'Dell a friend and an ally. When I saw him in Nashville I gave him a hug and said, "I appreciate you."
I'm not about drama.
Not here to start any shouting matches.
Just trying to paint a clear picture about what was good and what was bad throughout our interactions with OpenSats thus far.
And full disclosure: I'm prepping a new grant application for myself for OpenSats. So, sure, I have personal reasons for not wanting to burn this bridge.
But the reality is that there was just nothing outrageous or awful or controversial about our interactions. Circumstance and timing weren't right for attempts 1.) and 2.). Crossing my fingers for upcoming 3.).
Conspiracy theories are dumb.
That awkward moment you realize the person your hugging is conceal carrying
Happy Friday 🦦

2 hour show today
What a great fuckin time
Watch the recorded version here 👇
https://www.youtube.com/live/YT4FXG7Ncow?si=gY3o7ewey5AqoWzL
daily stoic 🤌
"As more young people "give up" on societal pressures, including the expectations to marry, have children, and achieve conventional success, it is exacerbating an already troubling trend in China's population dynamics."
Read more and subscribe!
https://www.bitcoinandmarkets.com/macro-minute-bai-lan-laying-flat-in-china/
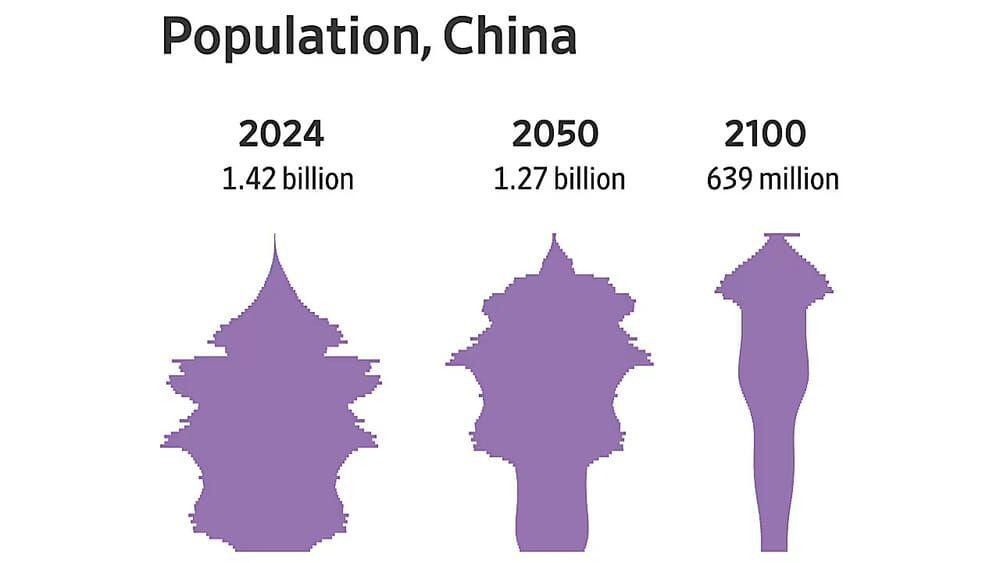
good read
I was getting around 20 a day when I tested a bitaxe ultra a month ago but I prefer solo lottery
You know you best
Get you some Baja Gold Sea Salt https://bajagoldsaltco.com/ one tsp diluted in a cup of water each morning.
Here’s the lab results from Aug 2024 https://cdn.shopify.com/s/files/1/0749/6538/5526/files/Baja_Gold_-_Major_Mineral_Analysis_-_August_2024.pdf?v=1724338423
gm
Probably overkill. You can power a BitAxe with a solar panel for under $100. I get your point that freedom isn’t free.
At gobrrr.me, we value open-source development of the tools and the resulting products we offer a lot. This is why a key part of the shop's mentality from the very beginning was the will to give back a part of our profit to the developers, so that they can continue to work on the projects and improve them over time.
Why am I telling you this? Well, depending on sales in the given months, donations were very small at times, but sometimes also quite sizable. Well, today we reached a milestone. Over the course of the last (almost) three years, we were able to donate over 2 Million Sats to open-source projects like nostr:nprofile1qyw8wumn8ghj7mn0wd68ytfj9eax2cn9v3jk2tnrd3hh2ep0qy2hwumn8ghj7un9d3shjtnwdaehgu3wvfnj7qgawaehxw309ahx7um5wgkhyetvv9ujuamvweejuumsv93k2tcpzemhxue69uhk2er9dchxummnw3ezumrpdejz7qg4waehxw309aex2mrp0yhxgctdw4eju6t09uq3zamnwvaz7tmwdaehgu3wwa5kuef0qyfhwumn8ghj7mmxve3ksctfdch8qatz9uqsuamnwvaz7tmwdaejumr0dshszxrhwden5te0dehhxarj9enx6apwwa5h5tnzd9az7qg4waehxw309ahx7um5wghx77r5wghxgetk9uqzpukfdjtlvsv62w8cfnel5uhzr9rqtcvysztwdeghpn89kanen4qqf0ru5h , another donation receiver this month was open source miners united, whom I couldn't find on nostr, sadly.
I didn't post our open-source contributions with proof for a while, they never stopped, though. Partly because I have no idea if we're the only ones doing this.
Anyway, hopefully we can inspire others to also give back to open-source development of the products they profit from. It's the only way to support volunteer projects like these and keep them alive.
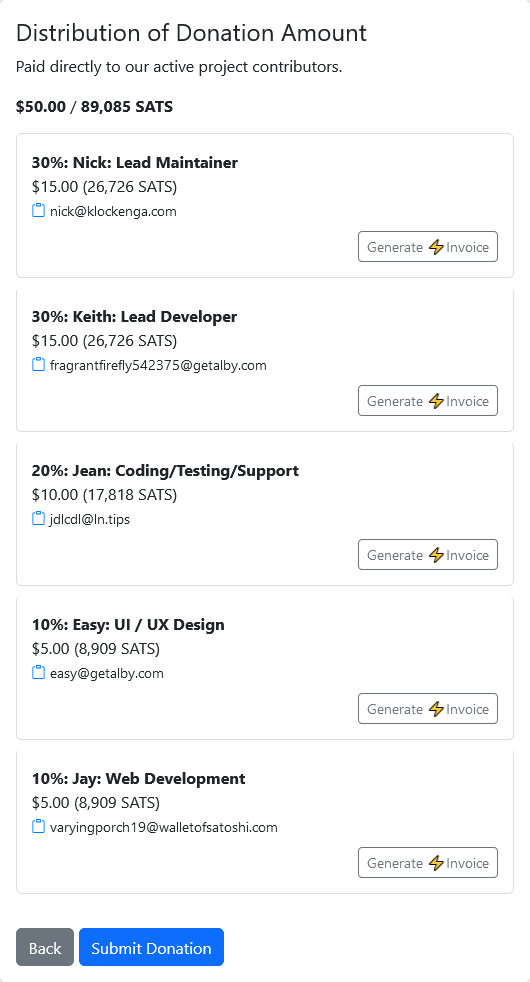
I don't get the #bitaxe craze
You can buy an s9 for like $65 for 15x the hashrate
https://kaboomracks.com/product/used-antminer-s9/
#mining #btc
BitAxe cost me $2 a month to run. Cheap lottery ticket. Free if you power with solar.
I don't get the #bitaxe craze
You can buy an s9 for like $65 for 15x the hashrate
https://kaboomracks.com/product/used-antminer-s9/
#mining #btc
The power consumption is like 100x higher though. That’s a lot of lottery tickets every month.
switch to ocean.xyz and setup BOLT12 to start seeing sats flow from your #BitAxe
Who wants to make some sats?!
Become an ambassador of the Sovereign Remnant ⚡️
Sales commissions paid in sats 🤌🏽
DM me once you have registered.
Register here: https://t.co/v3ocyUSLZz
What would you have me do?
The longer you stare at it, the more time it takes

 ?v=1609866381
?v=1609866381