Lit em if you got em. #420 #weed
https://video.nostr.build/47e367320887be8aaf2b0278d16a342da70c5f325fe802dece4256a41a8e0686.mp4
It’s four twenty somewhere https://video.nostr.build/aefd26b681d2ce49458439c3c1448efe3f08bd27b1690e41541d266571ee6406.mp4
I just got back home and haven’t eaten dinner yet but I’ll play some hands if y’all are down.
Cc nostr:npub10npj3gydmv40m70ehemmal6vsdyfl7tewgvz043g54p0x23y0s8qzztl5h
Bitcoin not crypto
Nostr not primal
I don’t think Danny or Peter ever called their sponsor Block Fi a ponzi even after they imploded.
The double standards and hypocrisy must stop.
With a Ponzi scheme they don’t buy assets with the money they raise they buy yatchs and planes and the monies are not reinvested into the company.
You don’t have to invest and no one is telling you to. But calling BTCTCs a ponzi is not true.
Danny doesn’t like Bitcoin Treasury companies. Danny and his guests have labeled them ponzi adjacent.
I’ll tell you what’s a ponzi, What Bitcoin Did’s fucking sponsors
Danny your reputation is cooked.
You can’t tell me nothing.
The guy who was shilling Blockfi which was an obvious scam is now calling companies that acquire Bitcoin by selling equity a ponzi?!?
What a fucking shmuck 
In 2015, an eccentric millionaire placed bitcoins in weak addresses.
For years, the prize has been contested by bots, GPUs, and in the future, it is expected to be the first target of quantum attacks.
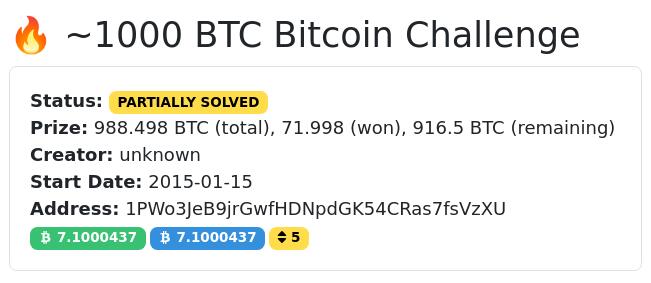
The individual's goal was to monitor the advancement of computational power capable of breaking Bitcoin keys.
These keys have up to 256 bits of entropy, which can be understood as the difficulty of discovering them. They are simply large numbers, on the order of 2²⁵⁶.
He then created 160 addresses, each with fewer bits of difficulty, from 1 to 160, and placed a few satoshis in each one, doubling the amount in the next.
The total prize reached nearly 1,000 BTC. There are still 916 BTC left to be claimed.
https://mempool.space/tx/08389f34c98c606322740c0be6a7125d9860bb8d5cb182c02f98461e5fa6cd15
The first few dozen addresses were quickly looted. There are bots monitoring the blockchain and stealing UTXOs that have some vulnerability — such as low entropy in the generation of the private key.
https://mempool.space/tx/0eb5b5c103e68eb0931430e7786cf1b6962f9eed5a2cb5271d4dd1699b77e86f
It was only at the end of 2015 that one of the owners of these bots noticed that the source of the bitcoins all came from a single transaction. He decided to share the discovery on the Bitcointalk forum, and that’s when more people began competing for the remaining prizes.
https://bitcointalk.org/index.php?topic=1306983.0
In 2019, the creator exposed the public keys of some addresses (those with indexes ending in 0 or 5). This is done simply by moving the coins—the key appears in the transaction. With it, other methods can be used, making it easier to crack.
https://mempool.space/tx/17e4e323cfbc68d7f0071cad09364e8193eedf8fefbcbd8a21b4b65717a4b3d3
One of these methods is a very old algorithm from 1978:
Pollard's Kangaroo Algorithm — a clever trick used to find private keys when part of the keyspace is known. Imagine two kangaroos jumping across a number line, one tame and one wild, eventually landing on the same spot. It’s a classic in cryptography, and now it's being used to chase Bitcoin prizes.
Since then, several programs and even participant "pools" have emerged, all trying to crack the next address. "kowala24731" secured an investment in the hundreds of thousands of dollars to rent GPUs and managed to break addresses #67 and #68 in early April.
Yesterday, someone, probably a beginner, cracked address #69 but didn’t secure the spending properly and exposed the public key.
In a few seconds, some bots cracked the key and replaced the transaction, battling for the balance. The last one paid a total fee of 1.2M sats.
https://mempool.space/tx/a52c5046f3097a8c2bd3b9889df2fb47b104d47a16cc679d3357feec003db753
The time to crack these addresses — discovering the private key from the public key — is quite short. A GPU can do it in less than a minute.
That’s why those who crack the keys can't publish it to the network; they must send it directly to a miner to include it in a block (like Mara).
Among the addresses with exposed public keys, the record was 130 bits of entropy, set by "RetiredCoder," who also cracked other keys.
These addresses are likely serving as "canaries in the coal mine" for the attacks Bitcoin may face. As long as there are still hundreds of BTCs sitting in them, yours should be safe.
Wonder if this is why there are big name firms (forgot which one) sending notices in the OP_RETURN to addresses demanding they prove that they own the address by moving UTXOs. nostr:npub1e3mx09yq53gyh9368qyuhfstgk8t7p5vvfcnvgwa4994y7rqg37s20qvr5 nostr:npub1yx6pjypd4r7qh2gysjhvjd9l2km6hnm4amdnjyjw3467fy05rf0qfp7kza
Butter or is that short for peanut 🥜 butter?!
She never does because they run away and she barks and then gets yelled at and has to go inside
Squirrel 🐿️ 
nostr:npub10npj3gydmv40m70ehemmal6vsdyfl7tewgvz043g54p0x23y0s8qzztl5h is the Friday Night Poker Master
Yeah we are playing rn nostr:note1mredq9q5vdvv2cwyyl0zv3reakrxqjx7jctaxlyuepjth5meq0sss2g4as










