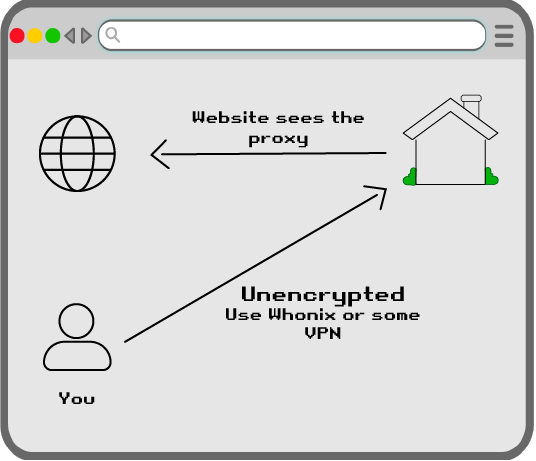
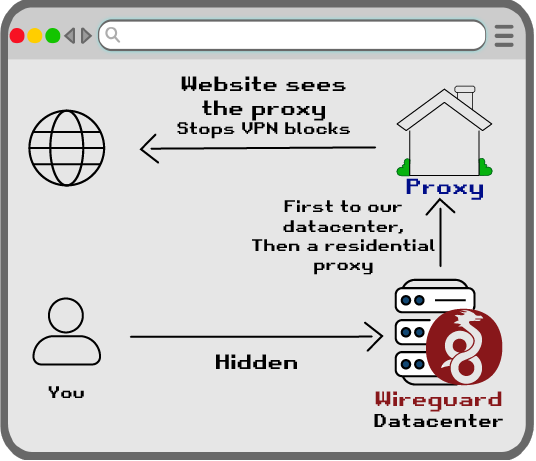
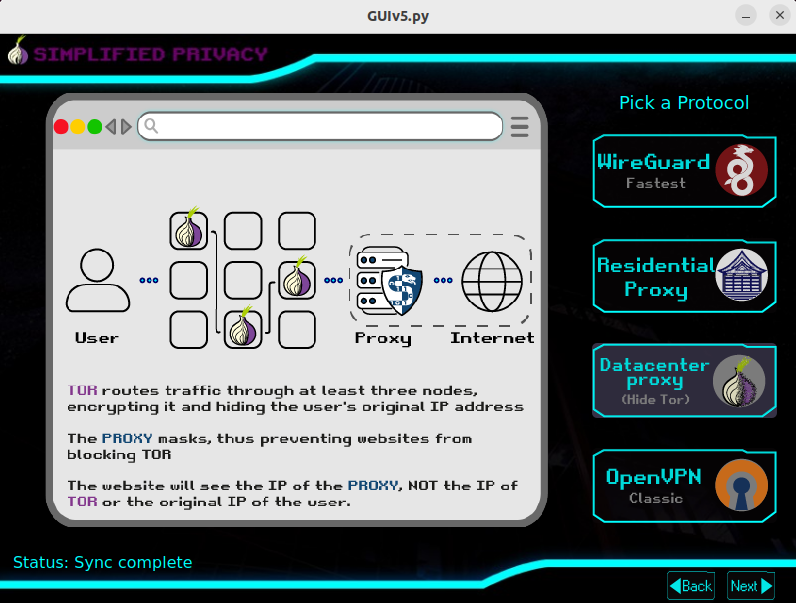
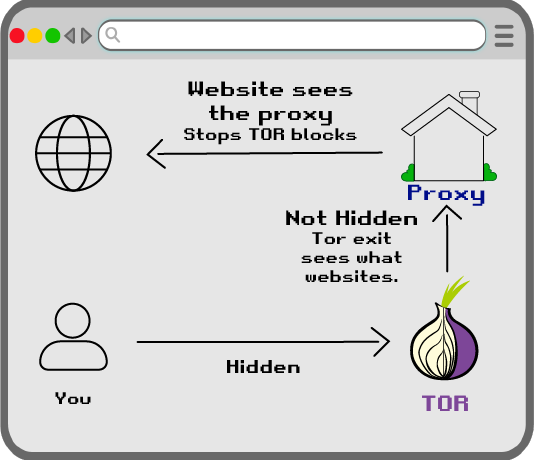
That is compared to ATH from what I can see, when 1 BTC was around 6M Doge. I'm not a trader so don't have precise charts.
Poor methodology. If you switch to eg. 1 Doge as base. Back in 2020 you could get 6M Doge for 1 BTC. Currently around 500k. So you method would call that -91.7% on BTC measured in Doge?
Sounds similar to retroshare?
Censored? Centralized? Closed to alternative clients? Blocking VPN? Ads?
The Bitcoin Fog case showed they can get "evidence" from basically hallucinations
I do not think it worthwhile to spend time trying to get the state to behave. Better spend it getting out of the walled gardens.
I use this kind of news to try to convince more people to install GrapheneOS, Linux etc. And if they use a cloud, do their own encryption on top.
I'm somewhat worried about compromised hardware though. No FOSS alternative there.
You can probably use https://www.trocador.app/en/ if you want to pay with xmr… I have no idea what a lighting decoder is or what it does.
I went to trocador, they also ask to provide a "Bitcoin (Lightning) address", not an invoice. I would guess that the part of the " invoice" that starts with LNBC1 is such an address, but I was not willing to bet 100000 SATs on it.
You can probably use https://www.trocador.app/en/ if you want to pay with xmr… I have no idea what a lighting decoder is or what it does.
It is this
I wanted to try that, but needed to pay a lighting invoice. The exchange services I found need a lightning address, not an invoice. Are there any services to pay ln invoice with xmr?
I put the invoice from Zeus into the lightning decoder linked intheis thread, it said "Not a proper lightning payment request"
It has this format:
bitcoin:BC1...?lightning=LNBC1...&amount=0.001
Will sending to either of those addresses pay the invoice?
I wasn't will to experiment with so many sats
Take a look at the DarkFI app alpha realease 😎
I can only show you the door. You're the one that has to walk through it 😎🥸
https://dark.fi/insights/darkfi-app-alpha-release.html
#privacy
#anonimity
#Monero
#nostr
#bitcoin
#agorism
Wanted to try it out. But AppVerifier gave me this code for the apk
darkfi.darkfi_app
89:49:33:C3:C2:B0:F4:76:A8:75:50:89:7A:BF:66:3E:DF:00:62:E3:08:50:A7:35:50:7E:A9:3F:73:E1:EE:DC
The release page says
Android: 4bb58f194544304b2ab97d25b830c88970cbad671c9d5794c96310b67ecbf6bc
Isn't those supposed to be identical?
I assume all these x accounts gets hacked because credentials are centralized and they get reset due to the service employees being scammed or bribed. Private keys only you have access to should lead to less compromised accounts.
Gold is not an American asset...
Fuck em. Do you own thing. Compliance is death.
Even a badge that says I'm an OG Legend?
When ice melts it uses energy, making the surrounding colder. By adding salt the freezing point is lowered, so it melts quicker. So it gets colder.
nostr:nprofile1qy2hwumn8ghj7un9d3shjtnddaehgu3wwp6kyqpqtxm993vcqstl0aratjhnl2hxqr8q2vc5shfk59qmedwhexxv2qpq4ghz70 nostr:nprofile1qy2hwumn8ghj7un9d3shjtnddaehgu3wwp6kyqpqpv5ug6gxy7fet6rltce6hkxksw599v3rnwut0wdc8c5v09k6qraqdynrtg
Why does everyone keep paying health insurance premiums when they know full well the health insurance never pays out?
I was wondering that too, not knowing American insurance system. But the article said 1 in 7 claims are denied. Guess the 6 of 7 are approved.
I didn't find on boarding hard. Main problem has been people getting new device or resetting. Then they expect to just put their name in and be reconnected with contacts. Database backup is not on their radar at all.