My older article about #malware #analysis #tools, part 1.
Screenshots are two years old, but these 5 free tools are still suitable especially for analysis of native executable files (PE for OS #Windows, or ELF for OS #Linux)
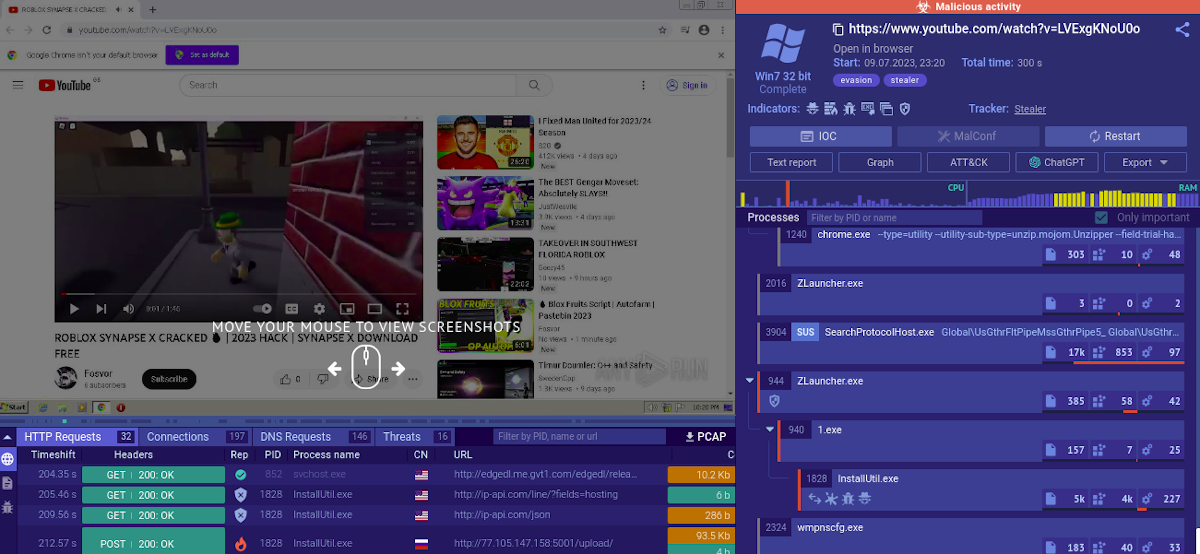
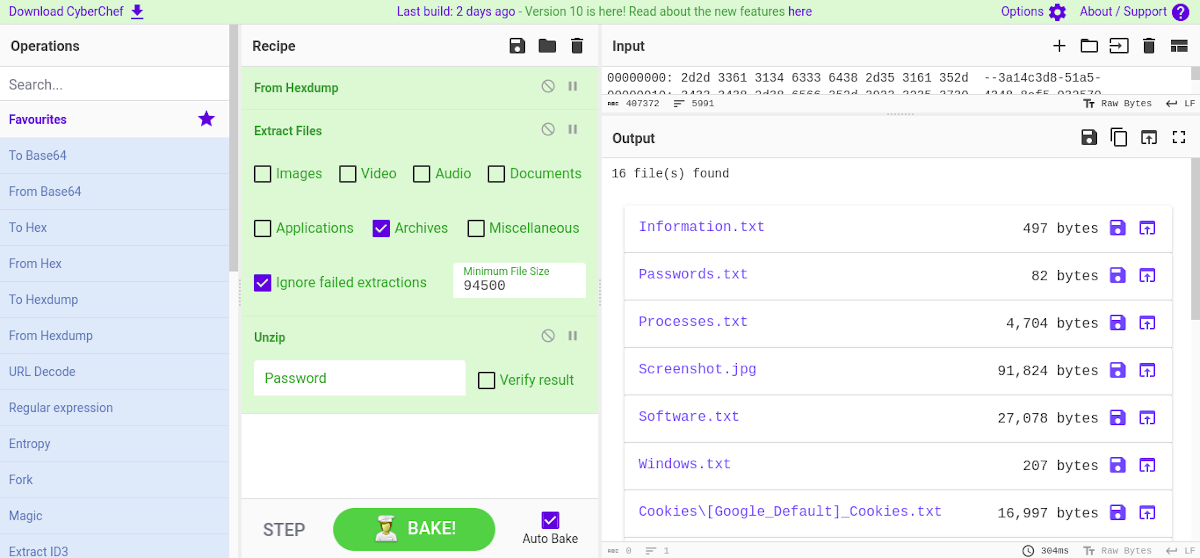
Sample analysis of #infostealer #malware pretending to be a hack for #roblox anticheat.
This week I delivered one lecture about cyber attacks and three 45-minutes malware analysis workshops with #anyrun and #cyberchef for high school students in #Roznava, #Slovakia.
#Education #CyberSecurity #blueteam #dfir #sandbox
[SK post] https://www.securitydungeon.sk/blog/2024-oarv-den-bezpecnosti/
TLDR: if you use Fortinet SSL VPN you have to disconnect your remote users. Immediately 🤦♂️
Critical #vulnerability in #Fortinet #FortiOS SSL #VPN.
Remote code execution without authentication.
Potentially already exploited in the wild.
Patches for supported versions are available, and they also recommend workaround: disable SSL VPN. Not just a webmode, but the entire SSL VPN.
It means that companies with Fortigate firewalls have to disconnect their remote workers from VPN if they cannot patch immediately or if they do not use IPsec VPN instead of SSL VPN.
So easy.

It goes #viral despite the lack of serious resources and information in the original article by Swiss news site.
While there are still lot of articles and posts about the 3 million #toothbrush #DDoS, several #security companies already stated somethnig like this. Until now I still have not seen any evidence of bothet with 3M toothbrushes and their DDoS attack - botnet of this kind and size will be observed very soon.
#Fortinet already said that the toothbrushes botnet was the hypothetical scenario during the interview.

Ref:
Yes, very good question. Everywhere is something “smart”, but too often it is very stupid to own and use those things. Single purpose things should stay single purpose, we do not need to turn them into smart devices just because it is cool (no, it isn’t, it is just marketing). #Privacy matters
Currently it is not clear if this is real or not (important info is missing in the original source).
However, this illustrates that lot of internet-connected things around us could be potential threat. Even the things we do not realize immediately such as washing machines, toothbrushes, refrigerators, etc. Of course, there are lot of examples of things already participated in DDoS attacks and/or infected with malware: soho routers, smart tv, printers, lightbulbs and other smarthome stuff.
#IoT often means Internet of Threats… so many “smart” toothbrushes infected with #malware 🪥 🦠 ☠️
#ddos #cybersecurity
nostr:note1c9cccnhcy5aaf8y5wfsxc9qvpn2j4zekzwpvnls9fmghxyulz2tq263zzk
#SSH keys with #Yubikey are very convenient and secure way to login. And you can have as many SSH keys as you want (*) protected with a single Yubikey or other #FIDO2 authenticator.
(*) I mean standard (non-resident) ed25519-sk and ecdsa-sk public/private keys.
There is also option to generate the resident key, where the credential id file is stored in Yubikey and not on your computer. But this is kind of equivalent of storing file with your credential id file on USB flashdrive and keep it together with Yubikey. The resident keys can be extracted from Yubikey.
And yes, I write credential id file instead of private key, because the generated file with private key is not the true private key. Instead, it is kind of seed/key handle and the true secret is stored in Yubikey and cannot be extracted.
* Non-resident keys are ideal for systems where #privacy is important if the YubiKey is lost or stolen.
* Resident keys are ideal for ease of access where the FIDO2 PIN is known.
More info: https://developers.yubico.com/SSH/Securing_SSH_with_FIDO2.html
#cryptography #authentication #fido2 #webauthn #2FA #MFA
Alby extension is available for firefox and it also supports chromium-like browsers, too. I was able to try it without google login in one of the more privacy-oriented browser for my experiments. However, I still have not tested the setup on android mobile, so good to know that it is not straightforward process.
SK/CZ: Ak sú na Bitcoin on-chain tx vysoké poplatky, čo robiť, ak ste poslali transakciu s malým poplatkom? Aké sú poplatky? A aké sú alternatívy pre ľudí, čo nechcú platiť vysoké poplatky?
Napísal som článok pre Bitcoin Alza
CZ: https://www.alza.cz/bitcoin-v-prostredi-vysokych-poplatku-tipy-a-triky
SK: https://www.alza.sk/bitcoin-v-prostredi-vysokych-poplatkov-tipy-a-triky
Pekný článok, vysvetlené poplatky aj možnosti, ako ich znížiť na minimum a ako bonus ku tomu mať aj rýchlejšie platby 👍
snáď sa to skrz Alzu dostane aj ku trocha širšej verejnosti
This clearly demonstrates the meaning of real ownership of our accounts and the difference bewteen #Nostr and #Mastodon.
Do you have a private key for your account? Are you the only one who owns the key? Then the account is yours. Otherwise it can belongs to someone else - this is the case of Mastodon and other social media accounts.
If you have only the username/password, then the service provider is the person who can publish content on behalf of you, or do whatever they want with your account. They are also responsible for protecting your identity. But do they their best for protecting you? Can you trust them?
Similarities with custodial and non-custodial #wallets are not accidental.
#privacy #socialmedia #ownership #crypto #keys
Critical #vulnerability in #Mastodon. Attackers can impersonate and take over any remote account. Users cannot do anything, this issue mast be solved by admins of Mastodon instances. And they should update their instances as soon as possible, on 2024-02-15 more details about vulnerability will be published.
However, this announcement means that attackers will focus their research to origin validation in Mastodon. So, we can expect exploitation attempts soon. And in two weeks, provided with details from updated announcement, it will be very easy to come up with an exploit, as announcement said.
https://github.com/mastodon/mastodon/security/advisories/GHSA-3fjr-858r-92rw
Yeah, Wazuh is great tool, it provides good visibility into your infrastructure. #Velociraptor is another example, but more useful for incident response and threat hunting in larger networks.
In top of that, network monitoring with IDS such as #suricata + ET Open signatures is useful addition especially for detect threats and anomalies originating from devices without wazuh installed. Analyzing traffic from IoT, guest laptops and smartphones and identification of all devices connected to the network is often very educative exercise.
Last week, I wanted to try Alby and begin my journey on Nostr, but there was one big obstacle: invite code :-(
I also tried another methods offered in your browser extension, but none of them worked for me without my own node. (Any of my lightning wallet is not supported)
In the meantime I have found another way how to create nostr account and connect it with another wallet for zaps. But today I have received the invitation to Alby, so I will give you another try :-)
Thank you. Actually, malware analysis can be very funny and often it is kind of #puzzle solving game. Great hobby for those who like mysteries and #technology. I learned lot of things just by trying to understand the binaries, assemblies, decompiled code and scripts
Any.Run now supports #Ubuntu operating system for behavioral analysis of #Linux samples.
#AnyRun is very useful #malware analysis #sandbox, you can interact with the virtual machine through your browser. It provides good visibility of processes, file and network events. Sandbox utilizes various signatures and rules for detection of suspicious activity. It can extract configs of several malware families.
Thanks to built-in #ChatGPT support it produces human-readable malware analysis report of windows samples suitable for less experienced analysts.
https://any.run/cybersecurity-blog/linux-in-anyrun/



Syslog vulnerability was introduced after Ubuntu 22.04, it affects Ubuntu 23.04 and newer.
Less severe qsort vulnerability is also in Ubuntu 22.04, and it is already patched.
IMHO shorter blog with experiences from installation and initial setup and then daily/weekly updates here of what works and what doesn’t work will be more attractive. It could also motivate some folks to try #postmarketos, too :-)


