Schrödinger’s Coin Model
https://www.swanbitcoin.com/investing/schrodingers-coin-model/

Senator Cynthia Lummis proposed a U.S. Strategic Bitcoin Reserve as part of a draft bill, the “Bitcoin Act of 2024.” The plan includes acquiring up to 1 million BTC over five years, with funding partly sourced by revaluing Federal Reserve gold certificates to reflect their true market value. This strategy aims to integrate Bitcoin as a strategic asset, hedging against inflation and reducing federal debt over time. The proposal emphasizes long-term Bitcoin storage with limits on asset liquidation to maintain financial stability.
#siamstr #btc #bitcoin #nostr
#siamstr #btc #bitcoin #nostr

Friedrich Hayek, in The Denationalization of Money (1976), advocated for the removal of government control over money issuance, which he believed led to inflation and economic instability. He envisioned a system where private entities could issue competing currencies, with market forces determining the most trusted and stable options.
Hayek’s views align closely with decentralized money like Bitcoin. He supported the idea that money should not be monopolized by governments and trusted market competition to regulate quality. Bitcoin embodies these principles through its finite supply, transparency, and resistance to manipulation, offering individuals financial sovereignty and choice outside traditional systems.
#austrian #siamstr #btc #bitcoin #nostr

Bitcoin differs from other coins that copy its code mainly in two areas:
1. Proof of Work (PoW): Bitcoin uses a PoW consensus mechanism, which is energy-intensive but offers strong security. Other coins may use alternative mechanisms like Proof of Stake (PoS), which can be more energy-efficient but less secure.
2. Network Effect: Bitcoin benefits from the largest user base, market cap, and liquidity, making it more valuable and secure. Other coins, even if they share similar technical features, struggle to achieve the same level of adoption and support.
#siamstr #btc #bitcoin #nostr

Psychohistory in Isaac Asimov’s Foundation series is a science that predicts the behavior of large populations, but not individuals. The key idea is that while individual actions are random and shaped by numerous unpredictable factors, the behavior of large groups follows statistical patterns, making it predictable. This is why psychohistory is only effective on a mass scale—individual decisions are too chaotic and influenced by personal free will to be forecast with accuracy.
The secrecy of the Seldon Plan is also crucial. If individuals knew the specifics of the plan, they could act to subvert it, altering its course and undermining the predictive nature of psychohistory. Therefore, key parts of the plan must remain hidden to prevent human intervention, ensuring the future unfolds as predicted. This secrecy is enforced by the Second Foundation, a group responsible for guiding the plan’s progression without revealing it to others .
#seldon #btc #bitcoin #siamstr #nostr #psychohistory
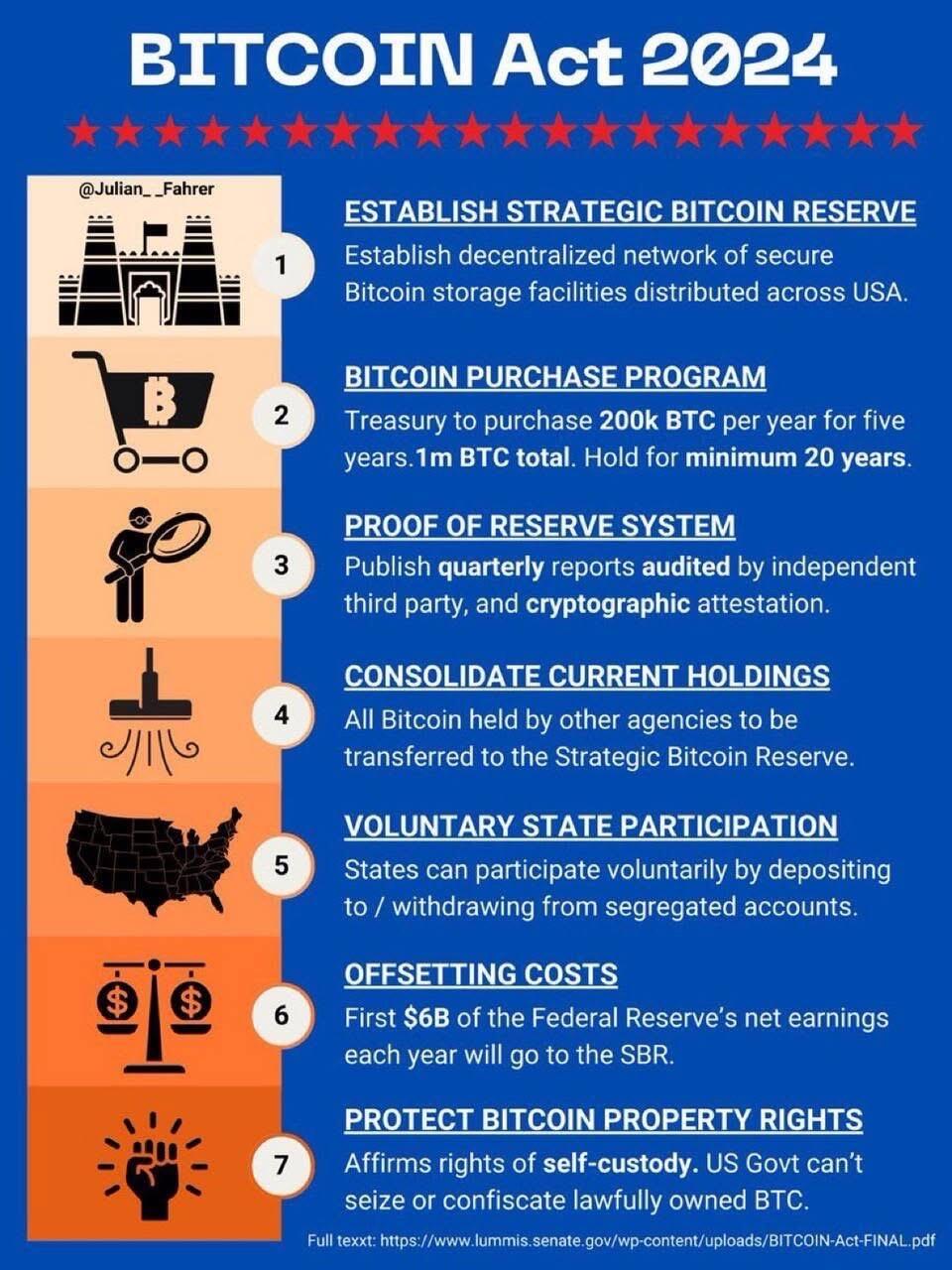
BITCOIN Act 2024

Why Isaac Asimov’s Foundation is Worth Reading for Bitcoiners
1. Decentralization and Resilience
• The series highlights distributing knowledge and resources to withstand societal collapse, similar to Bitcoin’s decentralized network resisting control.
2. Long-Term Vision
• Hari Seldon’s “Psychohistory” involves planning for future stability, paralleling Bitcoin’s long-term impact on financial systems.
3. Challenging Central Authority
• The fall of a centralized empire and rise of independent systems mirrors Bitcoin’s challenge to traditional financial institutions.
4. Philosophical Insight
• Explores themes like technology’s role in societal change, aligning with Bitcoin’s mission to reshape global economics.
#siamstr #btc #bitcoin #nostr

Bitcoin can be considered “hard money” from an Austrian economics perspective due to its properties as a unit of account, medium of exchange, and store of value:
1. Unit of Account: Bitcoin’s fixed supply (21 million units) ensures scarcity, a core characteristic of hard money. It is divisible (up to 8 decimal places), allowing precise transactions, and could eventually be used to price goods and services in the future.
2. Medium of Exchange: Bitcoin allows for decentralized, peer-to-peer transactions without intermediaries. While its volatility limits its widespread use today, solutions like the Lightning Network aim to improve its scalability and speed, enhancing its role as a medium of exchange.
3. Store of Value: Bitcoin’s capped supply and decentralized nature make it resistant to inflation and central bank control, aligning with the Austrian ideal of sound money. It’s durable, portable, and secure, making it an attractive store of value over time.
From the Austrian economics viewpoint, Bitcoin fits within a framework of individual sovereignty and market-driven value, challenging fiat systems that rely on inflation and central control. While its full adoption as a currency depends on overcoming challenges like volatility, its properties make it an ideal candidate for “hard money.”
#btc #bitcoin #nostr #siamstr

Bitcoin mining currently accounts for about 0.5% to 1% of global electricity consumption, although this number can fluctuate depending on the price of Bitcoin and the energy usage efficiency of mining operations. A significant portion of this energy is now sourced from renewable sources, with over 54% of Bitcoin mining operations using sustainable energy .
This shift towards renewable energy is partly due to Bitcoin mining’s ability to leverage surplus energy from regions with excess renewable generation, such as hydroelectric power, which otherwise might go to waste .
While Bitcoin mining’s total energy consumption remains a topic of debate, its role in promoting renewable energy and reducing wasted energy is increasingly recognized as a positive contribution to sustainability efforts.
#siamstr #nostr #btc #bitcoin

The probability of randomly guessing a correct Bitcoin private key is extremely low due to the vast number of possible combinations. A Bitcoin private key is 256 bits long, which means it has around 10^77 possible combinations. To put this into perspective:
• If you could perform 1 trillion guesses per second (1 terahash per second), which is much faster than most current computers, it would still take around 10^66 years to randomly find the correct private key. This is far longer than the age of the universe itself, which is about 13.8 billion years (approximately 10^10 years).
This makes it practically impossible to guess a Bitcoin private key by brute force, confirming the robustness of Bitcoin’s cryptographic security .
#siamstr #btc #bitcoin #nostr

Bitcoin mining can repurpose surplus energy that would otherwise go to waste, turning it into economic value. Here’s how:
1. Stranded Energy: Remote renewable energy sources like hydro, wind, or solar often produce excess energy during off-peak times. Bitcoin miners can use this surplus onsite, making these projects more viable.
2. Flared Gas: In oil extraction, unused natural gas is flared, wasting energy and emitting CO₂. Bitcoin mining can convert this gas into electricity, reducing waste and emissions.
3. Renewable Energy Stabilization: Miners act as “energy sinks,” using excess power from intermittent sources like solar and wind, stabilizing supply-demand mismatches.
4. Grid Balancing: During low-demand periods, excess energy is often curtailed. Bitcoin mining uses this energy, improving grid efficiency.
5. Economic Incentives: Mining creates demand for unused energy, making renewable projects more profitable and encouraging innovation.
By leveraging surplus energy, Bitcoin mining reduces waste, stabilizes grids, and supports renewable energy growth.
#siamstr #btc #bitcoin #nostr

An important concept in the world of Bitcoin called the “Byzantine Generals Problem.” This problem is about ensuring trust and reliability in a system where some participants might be dishonest. Imagine a group of military generals planning an attack on a city. If one of the generals is a traitor and sends false information, the entire operation could fail. So, how can the generals be sure the information they receive is true?
The solution to this problem lies in cryptography—a technology used to protect information. In Bitcoin, cryptography ensures that once data is recorded, it cannot be changed without being detected. Bitcoin uses a special mathematical function called SHA-256 to create a unique “hash” of every block of data, such as transaction records. If someone tries to alter the data, the hash changes drastically, making it immediately obvious that the information has been tampered with.
This system has kept Bitcoin secure and unchanged since it was created in 2009.
#siamstr #nostr #btc #bitcoin
SHA-256 (Secure Hash Algorithm 256-bit) is a cryptographic hash function widely used in Bitcoin. It plays a key role in Bitcoin’s security, mining, and transaction verification. Here’s a breakdown of how it works:
What is SHA-256?
• Hash Function: It transforms an input of any length into a fixed 256-bit (32-byte) output, called a hash.
• Deterministic: The same input always produces the same output.
• One-way: It’s practically impossible to reverse the output back to the input.
• Collision-resistant: No two different inputs should produce the same hash.
• Efficient: It’s fast to compute the hash for any given input.
#siamstr #btc #bitcoin #nostr

How Bitcoin Uses SHA-256
Bitcoin uses SHA-256 in the following ways:
1. Mining (Proof-of-Work):
• Bitcoin miners solve a computational puzzle to add a new block to the blockchain.
• The puzzle involves finding a nonce (random number) such that the hash of the block header is less than a target value (determined by the network difficulty).
• The process:
1. The miner takes the block header (metadata about the block, including the previous block hash, timestamp, and nonce).
2. Runs it through SHA-256 twice (double-SHA-256).
3. Adjusts the nonce and repeats until the hash meets the target condition.
Example:
• Input: Block Header + Nonce
• Output: 00000000000000000abcd... (starts with many zeros, meeting difficulty)
2. Transaction Verification:
• Transactions are hashed using SHA-256 to ensure integrity.
• A transaction’s hash acts as its unique identifier (transaction ID).
• Merkle Trees are used to organize and verify transactions efficiently:
• Each transaction hash is hashed again to form a tree.
• The root of this tree (Merkle Root) is included in the block header.
3. Address Generation:
• Bitcoin addresses are derived using SHA-256 and RIPEMD-160:
• First, the public key is hashed using SHA-256.
• Then, the output is hashed again using RIPEMD-160.
#siamstr #nostr #btc #bitcoin

Why SHA-256 Is Secure
• Pre-image Resistance: It’s nearly impossible to find an input from its hash.
• Second Pre-image Resistance: It’s infeasible to find two inputs producing the same hash.
• Avalanche Effect: A small change in input drastically changes the hash output.
• High Computational Cost: Brute-forcing SHA-256 requires astronomical amounts of computation.
SHA-256 in Action
Let’s say the input is Hello, Bitcoin!.
1. Apply SHA-256:
**Input: Hello, Bitcoin!
Output: 18af8192c1c09bd51a5cc4b6074c3e8c6d52f29523d20ae993f8e7c1e26e5e0f
2. Changing even one letter results in a completely different hash:
**Input: hello, Bitcoin!
Output: b53e563b8cd3fb7b0136623f2c6b3af1b30bc5018029bdabc3f125d96c3e63db
By leveraging SHA-256, Bitcoin ensures that the blockchain remains tamper-proof and secure, providing the foundation for trust in the network.
#siamstr #btc #bitcoin #nostr

To prove that a given output (such as a hash) is the result of a Proof of Work (PoW) from a particular input, nodes use a process that involves non-reversibility and verifiable computation without needing access to the original input. Here’s how it works:
The Process:
1. Hash Function and Input: In Proof of Work (PoW) systems like Bitcoin, a miner’s goal is to find an output (hash) that meets certain criteria, such as starting with a specific number of leading zeros. This is achieved by modifying an input (e.g., a block of transaction data) with a “nonce” — a random value that the miner can adjust.
2. Mining: The miner repeatedly hashes the input data with different nonces until they find one that produces a hash that satisfies the desired condition (e.g., the number of leading zeros in the hash).
3. Proof of Work: The output hash that satisfies the condition is the proof. This hash is presented along with the nonce that was used to generate it. The miner does not need to send the entire input data to prove the work; they only need to provide:
• The resulting hash (the proof).
• The nonce that was used.
• The input data (which is usually the block of transactions, the previous block hash, and a timestamp).
4. Verification: Other nodes can then:
• Take the provided input data.
• Combine it with the nonce.
• Hash the data again using SHA-256.
• Check if the resulting hash meets the criteria (e.g., has the required number of leading zeros).
If the hash is valid (i.e., it matches the criteria), the node has verified that the work was done correctly. The process is computationally expensive and cannot be faked because it’s impossible to predict the correct nonce without actually doing the work.
Example:
1. Miner wants to find a valid hash for a block of transactions.
2. The miner adjusts the nonce until they find a hash like this:
0000000000000000000a1a92d35bfc4f0d24369dbe6ff603fce42d4b315d72ad
3. The miner sends the block header (input data) and the nonce to the network, proving the work was done.
4. Nodes receiving the block can:
• Take the block header and nonce.
• Hash the data to check if the result matches the miner’s hash.
• Verify the hash starts with the required number of leading zeros (meeting the target difficulty).
Since SHA-256 is a one-way function and there’s no shortcut for finding the correct nonce, the nodes are assured that the hash came from the correct input and that the miner did the necessary work to find it.
Thus, while the node does not know the original input directly (beyond the hash and nonce), the proof is valid because the miner’s work is computationally verifiable by re-running the hashing process.
#siamstr #btc #bitcoin #nostr

A limited money supply, like gold or Bitcoin, can be used globally due to its divisibility, deflationary nature, and universal trust in scarcity. Limited money can be divided into smaller units (e.g., Bitcoin’s 100 million Satoshis per coin), allowing it to facilitate transactions of any size.
As global demand grows, the value of each unit increases, enabling the same supply to support more economic activity. Digital systems enhance this process, making transactions efficient and scalable. Historically, gold served as a global currency despite its limited supply by being trusted and divisible, with paper money backed by gold reserves.
Challenges like hoarding and liquidity needs are addressed through lending systems, fractional ownership, and local credit or currencies for short-term use, while the limited supply remains the stable base for global trade. Ultimately, the key is trust in scarcity, divisibility, and technological efficiency to manage transactions globally.
#siamstr #btc #bitcoin #nostr

Austrian economists reject the use of advanced mathematics in economics primarily because they believe that economics is a social science, not a physical science. According to them, human action and decision-making are too complex, subjective, and context-dependent to be accurately modeled using mathematical equations. Here’s an explanation of their reasoning and how they justify their views:
Reasons for Rejecting Mathematics in Economics
1. Subjectivity of Human Action:
Austrian economics is based on praxeology, the study of human action. It assumes that humans act purposefully to achieve goals, guided by subjective values and preferences. Since these preferences vary between individuals and over time, they argue that human behavior cannot be reduced to objective, mathematical formulas.
2. Complexity of Social Phenomena:
Austrian economists argue that economic systems are far too complex to be captured by mathematical models. They believe that such models oversimplify reality, ignoring important qualitative aspects of human decision-making.
3. Knowledge is Dispersed and Local:
Economists like Friedrich Hayek emphasize the decentralized nature of knowledge in society. They argue that no central planner (or mathematical model) can fully capture the knowledge dispersed among millions of individuals.
4. False Precision:
Mathematical models give an illusion of precision and certainty, which Austrian economists consider dangerous. They argue that such models often rely on unrealistic assumptions, like perfect information or equilibrium, that do not reflect real-world conditions.
5. Non-repeatability of Historical Events:
Economics deals with unique, historical events rather than repeatable experiments. Austrians argue that mathematical models, which are better suited for controlled experiments, cannot account for the historical and contextual nature of economic phenomena.
#siamstr #btc #bitcoin #nostr

How Austrians Prove and Explain Their Beliefs
1. Deductive Reasoning:
Austrian economists rely on deductive logic rather than empirical testing. They start with axiomatic truths, such as Ludwig von Mises’ action axiom (“Humans act purposefully”), and derive conclusions from these premises. This method is called praxeology.
2. Historical and Case Studies:
Instead of mathematical models, Austrians use historical analysis and real-world examples to illustrate economic principles. For example, they examine past episodes of inflation or economic intervention to argue against central banking and government interference.
3. Critique of Mainstream Models:
Austrian economists highlight the failures of mathematical economics, such as the inability of mainstream models to predict financial crises. They argue that such failures demonstrate the limitations of relying on equations to understand dynamic, human-driven systems.
4. Focus on Qualitative Insights:
They emphasize verbal logic and narrative to explain economic phenomena. For instance, the Austrian theory of the business cycle explains how artificial credit expansion leads to malinvestment and eventual economic downturns, using logical cause-and-effect reasoning.
5. Epistemological Arguments:
Austrian economists often argue from a philosophical standpoint, questioning the very foundations of mathematical modeling. For instance, they contend that since humans have free will, their actions cannot be modeled deterministically, unlike physical phenomena.
#siamstr #bitcoin #btc #nostr
