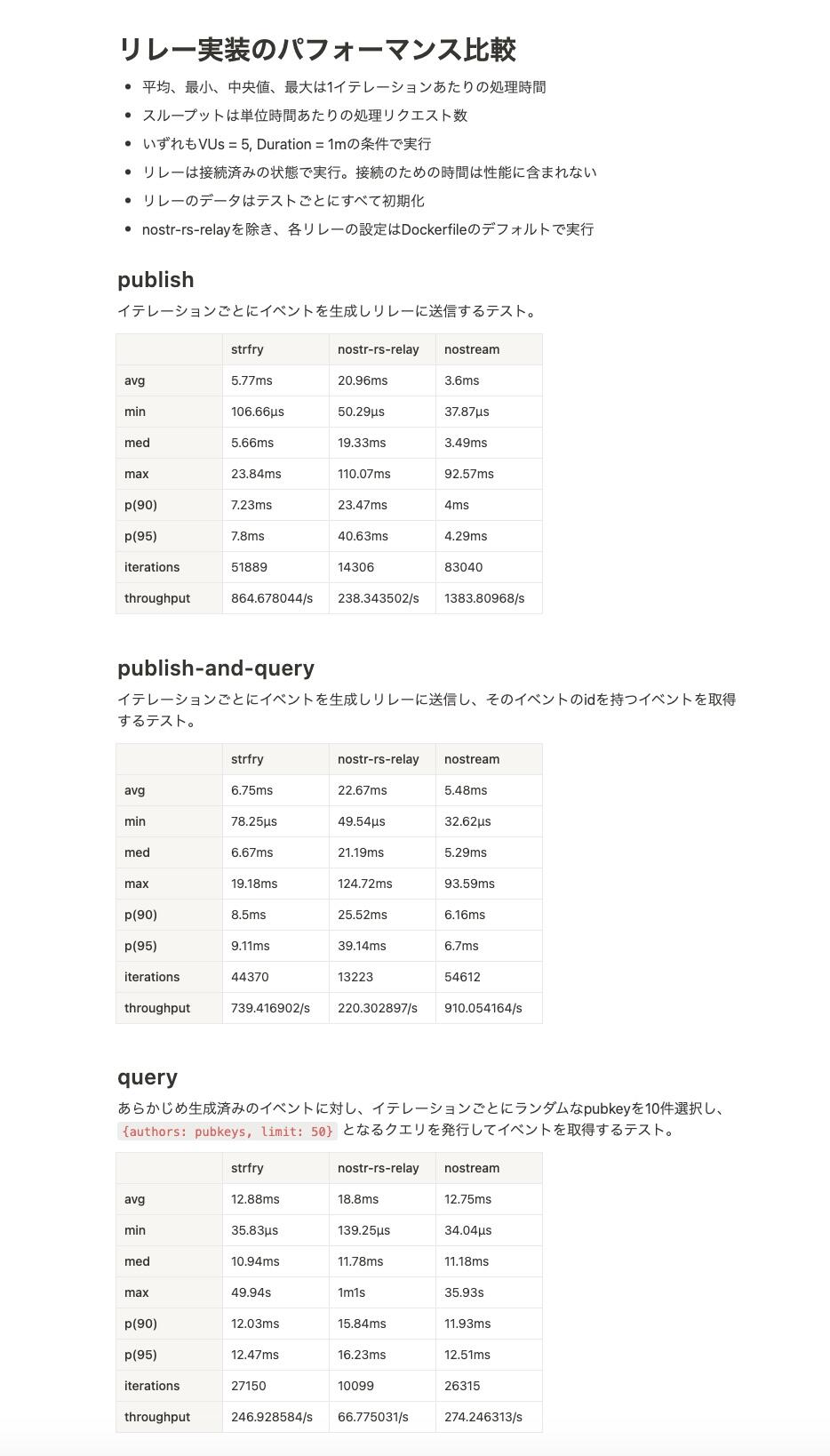
Ah, glad to hear that,
Indeed, especially since there are no real formal test between many relays as far as we know except for what you have done. 🙏
Maybe, if you don't mind, you can probably try to test rnostr https://github.com/rnostr/rnostr . Especially, since it is written in Rust and uses LMDB, its performance should be around strfry too.
Nice benchmark, kamakura-san. Hopefully, you will present this with detail reports on Hackaton Nostrasia Final Presentation.
Only a bit suggestion,
1. Maybe you also need to make sure clearing the I/O cache (/proc/sys/vm/drop_caches, etc) between every test loop to get a fresh state if you haven't done it (yet).
2. I'm assuming this test using 'default' settings for those relay, right? Maybe you can also have the benchmark with some 'optimized' settings if you have the time.
Use both, but prefer a bit on early return. Golang early return is my favorite.
Good luck kamakura-san 🙂
Btw, you can also probably try to submit this or your previous Nostr project to OpenSats, nostr:npub1937vv2nf06360qn9y8el6d8sevnndy7tuh5nzre4gj05xc32tnwqauhaj6 -san has already receive grant from them. Maybe other Japanese devs can also try to apply the grant.
History were written by the winner (maintainer). Any attempt of non comforming PR/issue will be closed. 🙂
Agree with Vitor, it's easy using "mute words" feature.
Example (common racial slur):
ni**a, ni**er
Amethyst made mute list private only. Probably compatible with Snort since Snort can read private mute list.
https://github.com/relayable-org/strfry-policies maintained by nostr:npub108pv4cg5ag52nq082kd5leu9ffrn2gdg6g4xdwatn73y36uzplmq9uyev6
Mirror of:
True, what is your practical tips to handle this (for now)? Especially since common affected software like Nginx and Caddy haven't fully solve this issue (yet) if i'm not mistaken.
I've heard that Nginx is currently preparing to issue a new patch that will be released to handle this CVE https://www.nginx.com/blog/http-2-rapid-reset-attack-impacting-f5-nginx-products/
Cc nostr:npub18kzz4lkdtc5n729kvfunxuz287uvu9f64ywhjz43ra482t2y5sks0mx5sz nostr:npub12262qa4uhw7u8gdwlgmntqtv7aye8vdcmvszkqwgs0zchel6mz7s6cgrkj
HTTP/2 Zero-Day Vulnerability Results in Record-Breaking DDoS Attacks
L: https://blog.cloudflare.com/zero-day-rapid-reset-http2-record-breaking-ddos-attack/
Cc nostr:npub1yxprsscnjw2e6myxz73mmzvnqw5kvzd5ffjya9ecjypc5l0gvgksh8qud4 nostr:npub1qqqqqqyz0la2jjl752yv8h7wgs3v098mh9nztd4nr6gynaef6uqqt0n47m
Curious to any nostr relay dev opinion. What do you think about this attack? Especially if it happened to Nostr relay.
Maybe nostr:npub1ltx67888tz7lqnxlrg06x234vjnq349tcfyp52r0lstclp548mcqnuz40t , he built zappdit.com
Vitorニキ、はよドラフト移動しろやって言ってるどうしよう
https://github.com/nostr-protocol/nips/issues/742#issuecomment-1740869049
Yes, I think you can probably start to write NIP PR (draft) kaiji-san
COBOL is smiling to this note/post 🙂
Update your browser and your libvpx dependency.
"Heap buffer overflow in vp8 encoding in libvpx in Google Chrome prior to 117.0.5938.132 and libvpx 1.13.1 allowed a remote attacker to potentially exploit heap corruption via a crafted HTML page. (Chromium security severity: High)"
"Specific handling of an attacker-controlled VP8 media stream could lead to a heap buffer overflow in the content process. Fixed in Firefox 118.0.1, Firefox ESR 115.3.1, Firefox Focus for Android 118.1, Firefox for Android 118.1"
https://www.tenable.com/cve/CVE-2023-5217
https://www.mozilla.org/en-US/security/advisories/mfsa2023-44/
Maybe, next time, i guess you will probably make a tool again to bridge medium, wordpress, etc. 👀
Yes, probably you can make it as separate independent service (plugin) instead of rules for strfry policy. Especially if the process takes more than one second to classify one event content. Let the event comes first, process them in queue, and delete it later if it was detected as high probably gibberish spam.
Yes, i think you and nostr:npub1qlkwmzmrhzpuak7c2g9akvcrh7wzkd7zc7fpefw9najwpau662nqealf5y can manage that easily for those problem 🙂
I think you can also add some gibberish (non sense random words or random string) detection. I have seen some model or space in huggingface. This can be helpful for detecting non sophisticated spammer bot which use random char or random non sense words.
Yes, hopefully he will be more active in nostr and fediverse (if he has any account) instead of other centralized social media.
Awesome nostr:npub1r0rs5q2gk0e3dk3nlc7gnu378ec6cnlenqp8a3cjhyzu6f8k5sgs4sq9ac, hopefully more nostr clients will be motivated to include this "must-have" feature even outside the bounty. Thank you for your great bounty initiative 🙂
Congratulations nostr:npub1ye5ptcxfyyxl5vjvdjar2ua3f0hynkjzpx552mu5snj3qmx5pzjscpknpr 🎉