Well, use #simplexchat then?
Sounds like a virtualbox issue
*sarcasm* Yes, but Jack, "They Were All Out of Step But Jim!"
🎮🔥 Exciting news, Rust fans! 🔥🎮 Earn free skins just by watching your favorite Rust streamers on Twitch! 🖥️👀 Don’t miss out on these awesome rewards! 🚀💥 #Rust #Twitch #Gaming https://twitch.facepunch.com/
https://files.facepunch.com/lewis/1b2111b1/xqc_metal-chest-plate.mp4
https://files.facepunch.com/lewis/1b2111b1/trainwreckstv_lr300.mp4
https://files.facepunch.com/lewis/1b1411b1/nmplol_garage-door.mp4
https://files.facepunch.com/lewis/1b1411b1/qtcinderella_assault-rifle.mp4
https://files.facepunch.com/lewis/1b1411b1/ironmouse_hoodie.mp4
https://files.facepunch.com/lewis/1b2311b1/foolish_bandana.mp4
https://files.facepunch.com/lewis/1b2311b1/abe_lr300.mp4
https://files.facepunch.com/lewis/1b2311b1/neff_jacket.mp4
https://files.facepunch.com/lewis/1b2311b1/emiru_assault-rifle.mp4
https://files.facepunch.com/lewis/1b2311b1/kkatamina_jacket.mp4
Wrong Rust... the hash tag is for the Rust programming language
No... no that is not the definition of Nazism.
You don't have any evidence to disprove him, so instead you attempt to attack his character? Where did you learn to debate?! Logical fallacies prove nothing! Jack bases his claims off evidence, inviting people to learn for themselves.
blossom-server-ts v4.0.0
Changes:
- Require "x" tag with sha256 hash on uploads
- Rebuild landing page with tailwind and lit
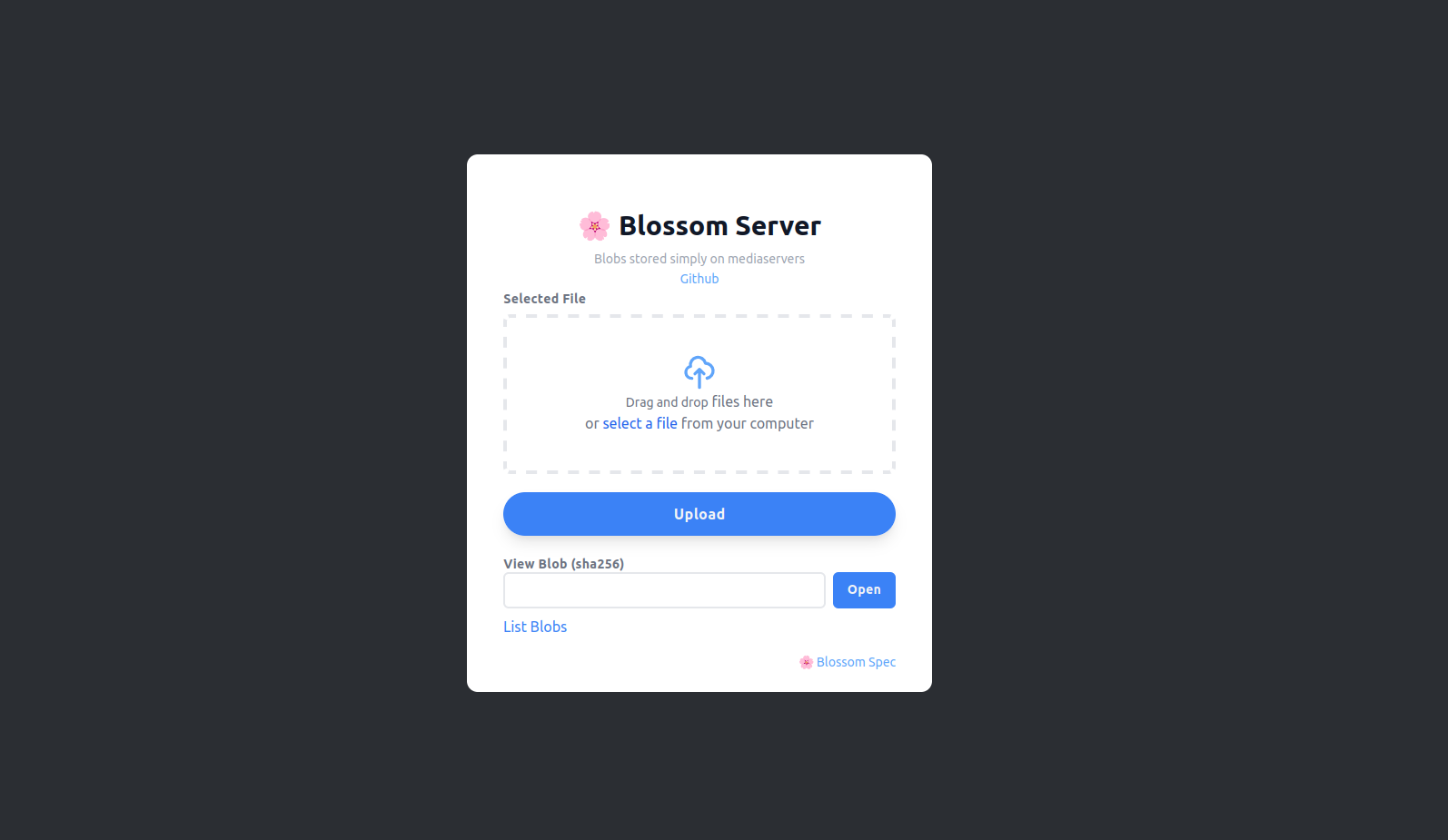

You can run it with either npx or docker https://github.com/hzrd149/blossom-server/tree/master?tab=readme-ov-file#running-with-npx
#blossom
How is attestation being performed to prove the integrity of the file? How are you addressing stale file states (file gets removed from one source, but before the deletion is reported to the network, another person downloads it)? Do you have plans to allow sealing the content for specified users?
I would disagree with you opinion of it not being broken. It does work, but it has some painful flaws. If people switch to age, the argument could be reversed as far as popularity.
That is debatable. If there is a proven better solution, then using something brokendoesn't make sense
Why should I use this instead of
I didn't realize rebinding was so easy... Hmmm 🤔
I prefer Vaultwarden
To quote nostr:npub15879mltlln6k8jy32k6xvagmtqx3zhsndchcey8gjyectwldk88sq5kv0n, Go. Get. F*****! 😉
Neither. This is a weakness in how the JVM responds to invalid memory access. While there are some security issues existing in the LXC namespace, they do not correlated with this issue.
That gets a little complicated. The short answer is yes, but the are not any security measures preventing heap dumps from memory access violations. If your application is on the device, it can cause a dump and grab the info from it.
The JVM has the String pool. An area of memory which is NEVER garbage collected. It only cleans itself on heap dump or application restarts. Unless you are encrypting client-side, your PII and credentials are stored in plain text in memory. #NoMoreJava