Explain it to me in the least amount of words
Our VPN lets you stay private, even when the website wants to prevent you from doing so.
~~~~
Explain it to me like an Elevator Pitch
On the client,
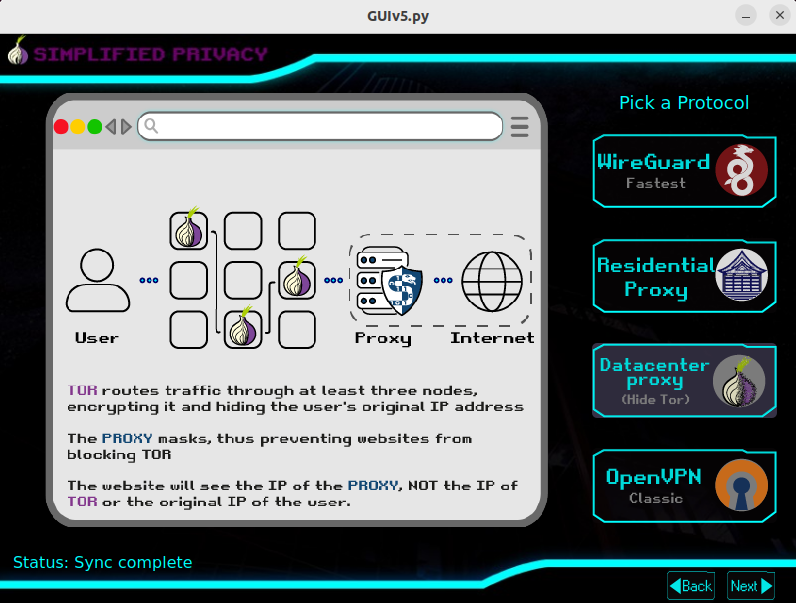
Simplified Privacy lets you manage different undetectable browser fingerprint identities
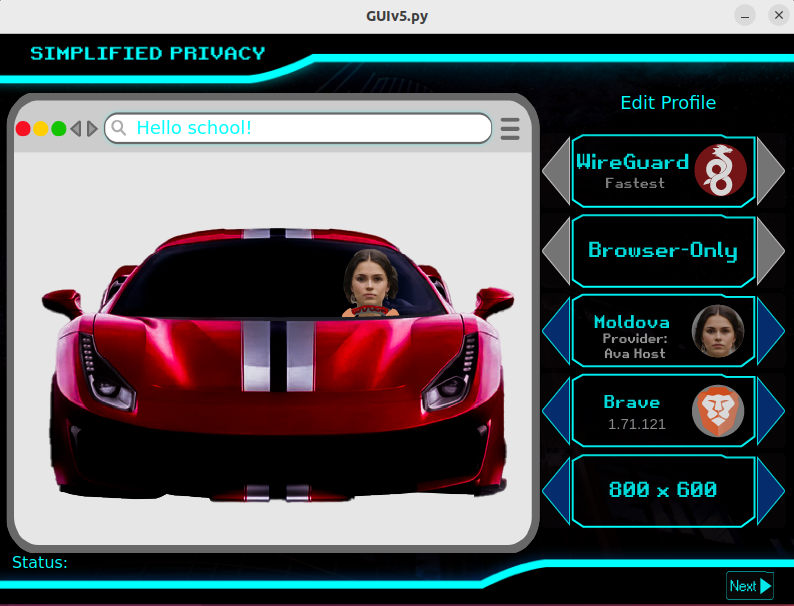
On the server,
Simplified Privacy uses small 1-country "underdog" datacenters, that AVOIDS situations where the website you're visiting, uses the same large datacenter router as your VPN
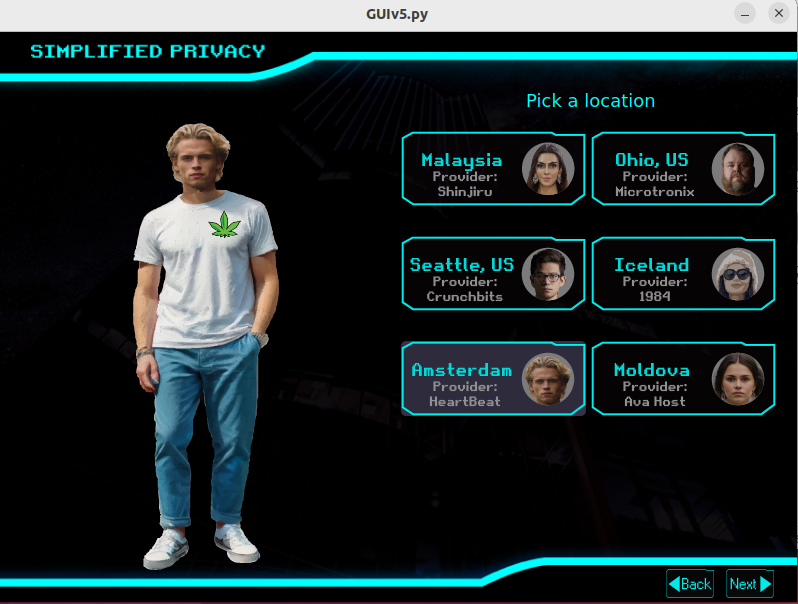
Together,
By splitting up your traffic up to different underdogs, combined with using different fingerprints, it presents a realistic, yet easy-to-use solution, to the rising threat of AI surveillance
~~~~
Explain it to me like a TV commercial
QubesOS is a pain in the ass to manage. Do you hate setting up new virtual machines?
Well unlike virtual machines or containers which slow down performance during use, are slow to load, and suck up storage space,
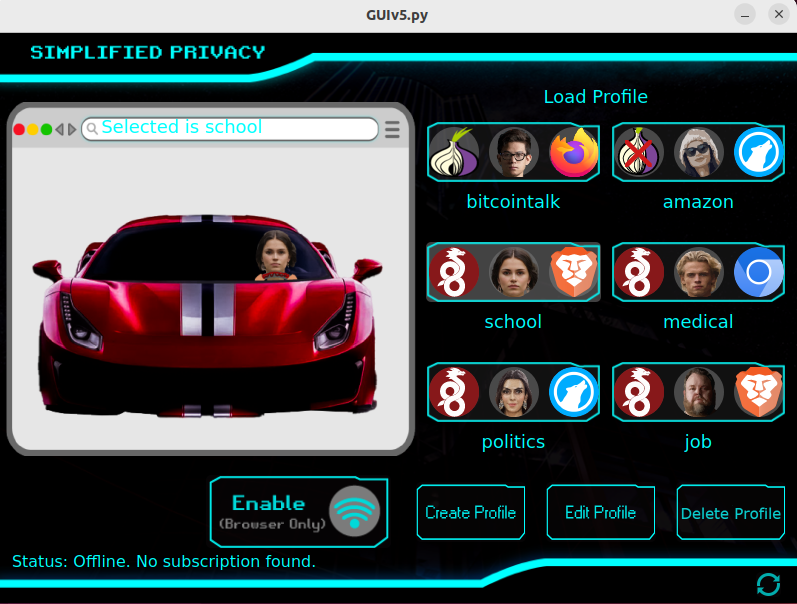
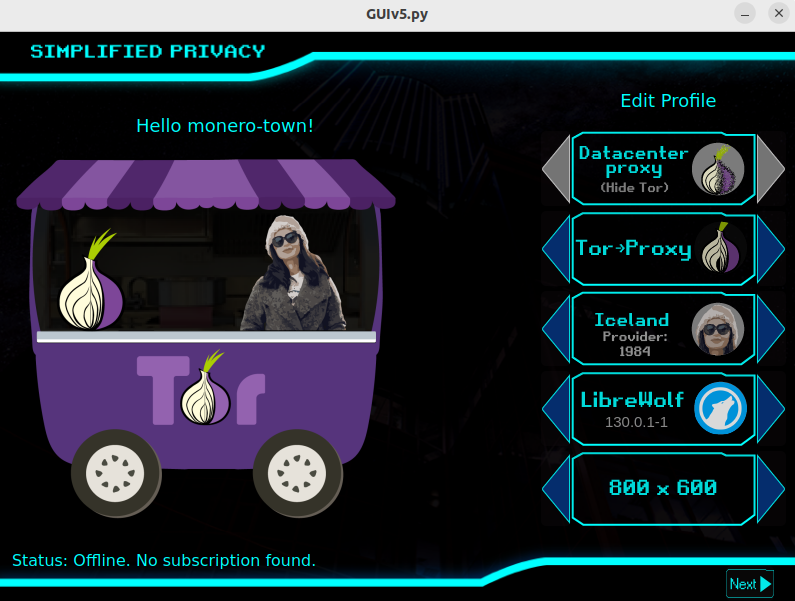
With Simplified Privacy, in a single click, and with zero performance drag, you can create multiple realistic identities, which each have their own graphical display screen size and isolated filesystem, which are then routed to different countries, have the timezone match, and with different $1 burner VPN billing codes.
That's right, try it out for just $1/month in Monero or Bitcoin Lightning.
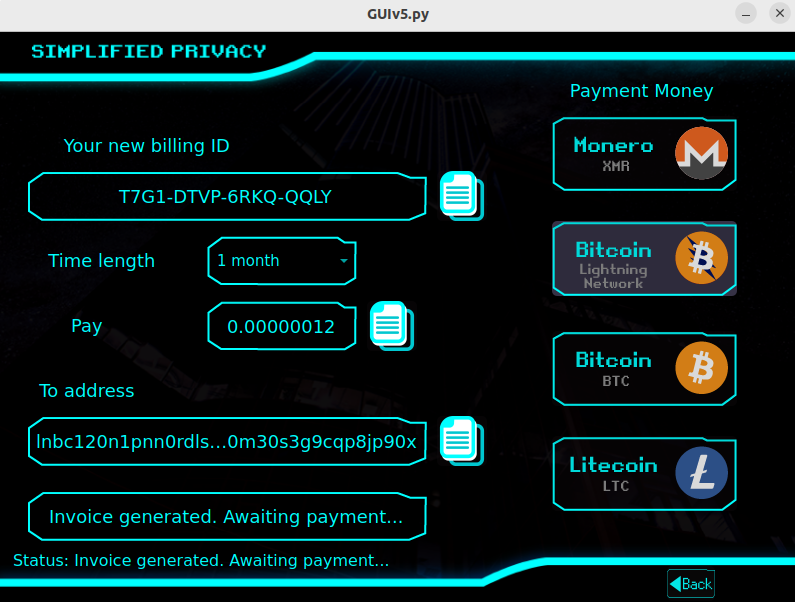
No Email required. Fully open source from day 1. And they didn't even print shitcoins!
~~~~
Explain it to me like I'm exiting the Matrix

Neo, You think there are all these different websites,
But they are all Cloudflare. And Cloudflare trains AI to recognize you based on your browser fingerprint.
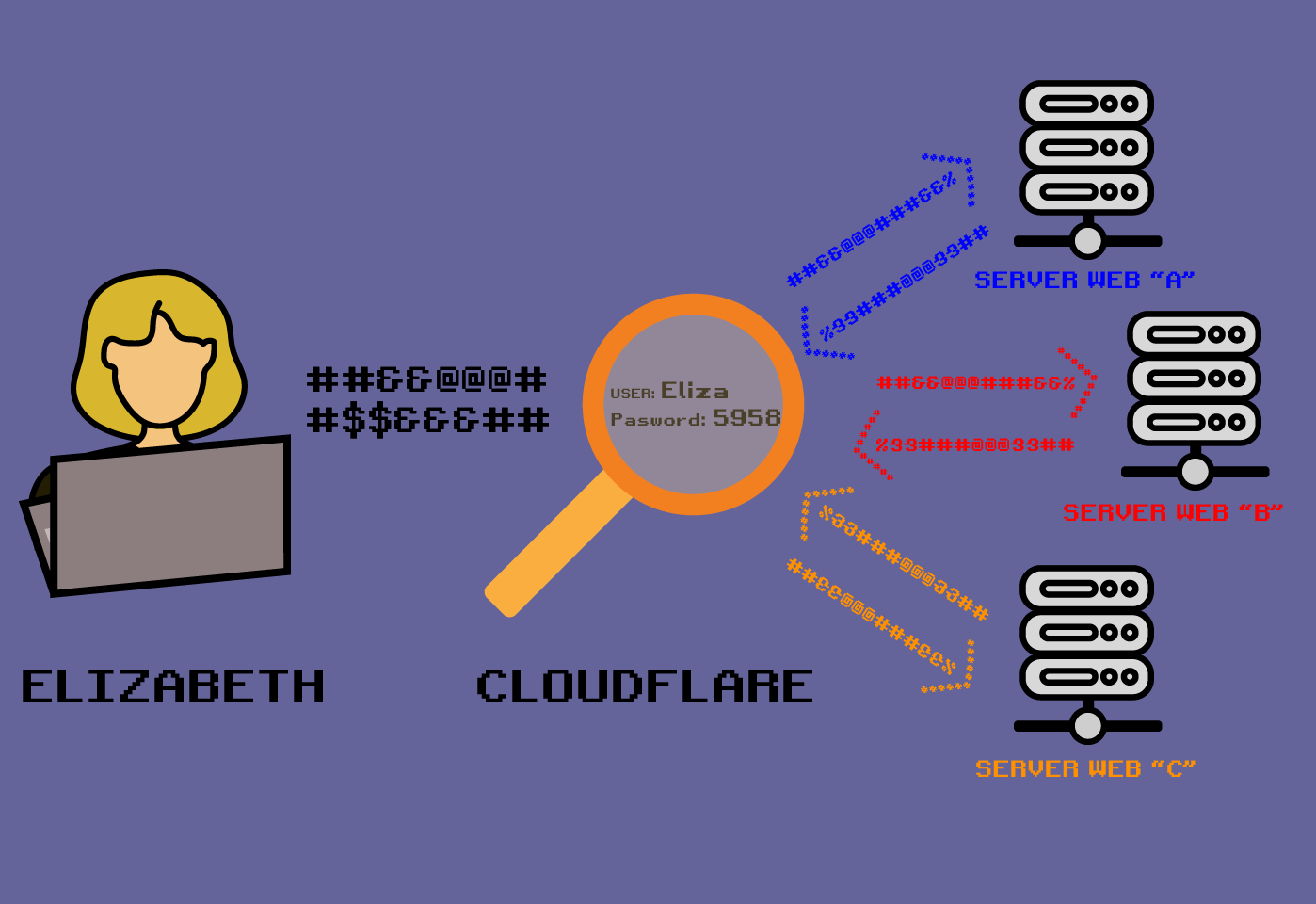
Neo, You think there are all these different VPNs,
But they all use the same large providers, like M247 and DataPacket. Mullvad, IVPN, Proton, Nord, TorGuard, and others all use M247 for many locations such as New York.
And even worse, the WEBSITES you're visiting often use the SAME providers as your VPN. So it goes:
You -> M247 VPN -> Cloudflare -> M247 VPS
Can you handle the truth Neo?
Because you're passing through the same providers with the same browser fingerprint to Cloudflare, nearly everything you do is surveilled, even if you're using a VPN.
What if I told you that the very people who you're trying to evade, designed the systems that the most famous provider uses?
But now that you know this Neo, you have a choice.
If you take the blue pill,
You can keep using Mullvad's government-browser and feel safe.
Or you can take the red pill,
And try Simplified Privacy.
~~~~
Explain it to me like a Teenage Girl

My school banned Chat GPT! I could lose my upcoming college scholarship if they find out I’m using it! So you know how VPNs hide your IP address or where your traffic is coming from?
I learned the websites don’t just see this IP address.
They also do browser fingerprinting, which is analyzing everything about you. It’s got the Screen size, browser version, time zone, probe for relevant cookies, and even some complex AI stuff to make a unique identifier of the browser. You thought Cindy was a loud mouth? LOL They sell the fingerprints.
Before I thought it was like totally anonymous.
But even though you are sharing this IP address with other people, you might be like the only one coming out of that British VPN IP with a Miami clock, with 1280x800 resolution, and that exact browser version or whatever. Totally insane right?
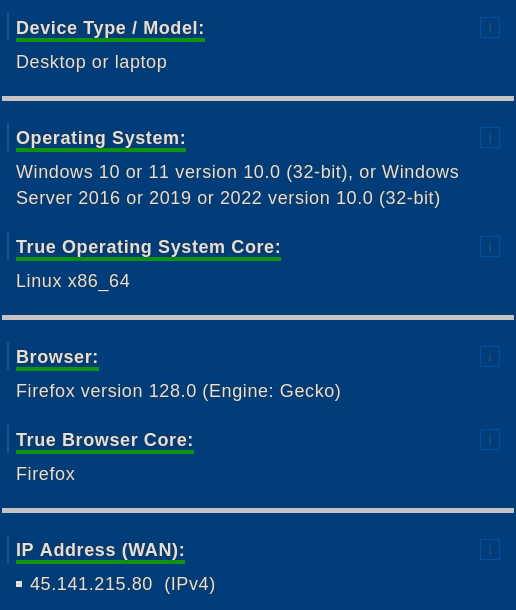
OMG like if we login with that same browser to our school Gmail, or anything tied to our real names, even though we’re using a VPN, it like brands the fingerprint to be tracked. But then my boyfriend showed me Simplified Privacy.
~~~~
Explain it to me like a Crypto-Anarchist

These corrupt government thugs want to track our every move like dogs with a collar.
All these VPN companies are lying assclowns, they use the same cloud providers, like M247 and DataPacket. The NSA can't tap every router on the planet earth. So they focus on the routers and switches of the largest providers in each country, and then the same provider is both the VPN, and the website you're visiting.
For example, Discord is hosted on DataPacket. So if you use Mullvad for Discord, then DataPacket sees your real residential IP and ALL Discord data. It's a pure conflict of interest to hide from the company with that same company. Plus it's a one-stop shop for global court orders.
Speaking of which, by using large international providers, the country of the VPN doesn't matter anymore. For example DataPacket is Mullvad's Mexico exit, but it's a UK/US company. So you ain't hiding in Mexico, you're getting a UK or USA court order.
And even worse, when you do an audio call on SimpleX, XMPP, Signal, or anything it uses WebRTC. WebRTC is connecting you and the person you're talking to peer-to-peer. This means there's a good chance M247 is seeing the IPs of both people, since every other VPN also uses M247. And then you're doxxing BOTH SIDES of the conversation by these large providers, even if it's SimpleX.

Mullvad is lying bro. They mouth off about being in Sweden, but M247 is all over the US, with the web panel going through Cloudflare. US Cloudflare is seeing Mullvad's customer panel and communication with M247, and Mullvad even rented servers using a Gmail.
Even worse, CIA contractors like Oracle buy and sell Browser Fingerprints tied to our names and data. Some weak script kiddie clowns try to evade using:
1) "user-agent spoofing", aka lying
2) blocking access
The issue with user-agent spoofing is that you're essentially bullshitting with your words only. The website asks you, "hey what's your screen dimensions?", and you just straight up lie in their face. This is shockingly ineffective, because websites will test you by having you render graphics, or access the browser via JavaScript.

Google Captcha and Cloudflare both have AI to spesifically identify your bullshit. So with "user agent spoofing", your fingerprint sticks out even more, because you got your regular fingerprint combined with the bullshit user-agents.
For example now you're really 1080x800 resolution with a Miami clock, Swiss IP, Brave v1.7 but LIES with a 800x800 bullshit resolution, bullshit UK clock, and bullshit Firefox user-agent. That's even more unique you dipshit!
In fact, user-agent spoofing is so worthless, that the "Chameleon" browser extension, which relies purely on user-agent spoofing, literally white-lists Google and Cloudflare. In other words, the most popular user-agent spoofer literally GIVES UP and doesn't EVEN TRY to deceive the MOST COMMON AND POPULAR tech companies.
The other common technique is blocking. This is what LibreWolf, Brave, and the government-created Tor-browser that Mullvad leeches. Weak Mullvad can't even develop their own tech, they lease it from the US military.
The issue is you're blocking technology many websites use. So most websites break, or are an epic pain in the ass to use. In fact, Brave's newer versions stopped even offering "Strict" mode for fingerprinting, because it broke so many sites.

Some turn to virtual machines to deceive websites. The problem with this is that it consumes massive time to set up the virtual machines, time to start them up every day, and wastes system resources. Because it wastes CPU and RAM, it's not only slower to use, but also slower to load. And it prevents you from having many open at once.
Instead, I've been using Simplified Privacy. At first I thought they were just a bunch of assclowns mouthing off obvious stuff for SEO to sell Graphene phones.
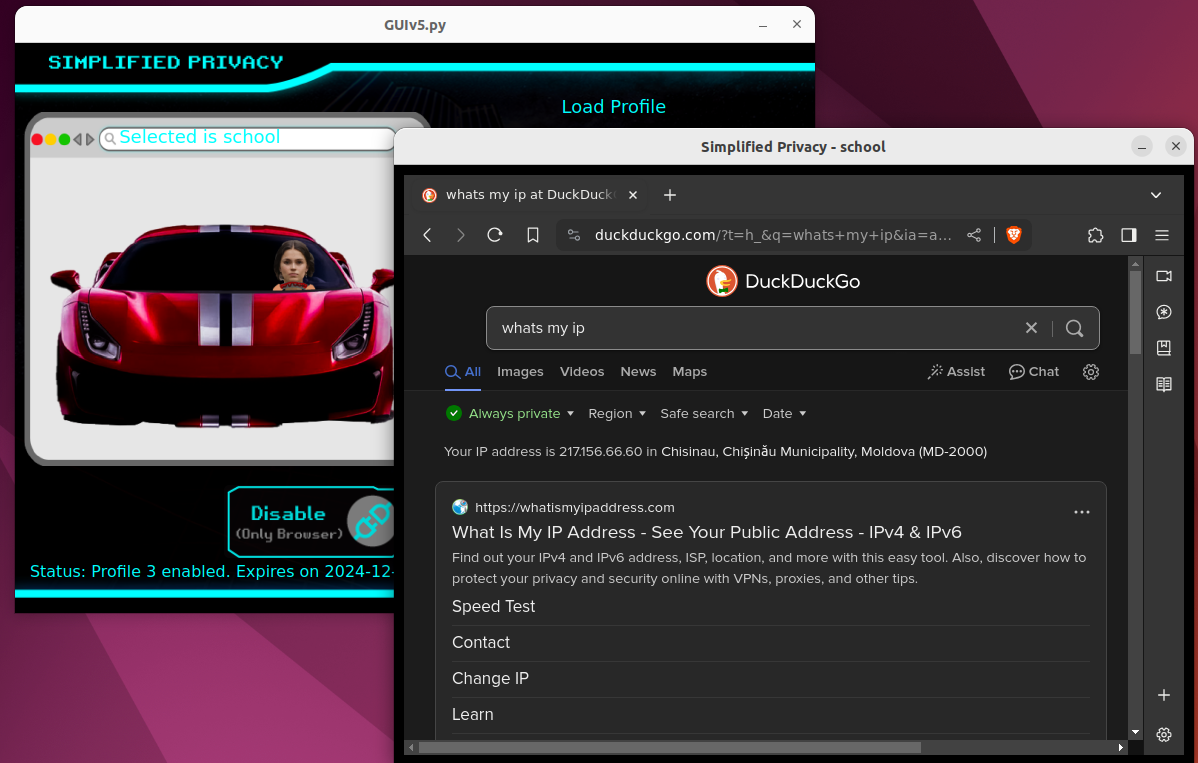
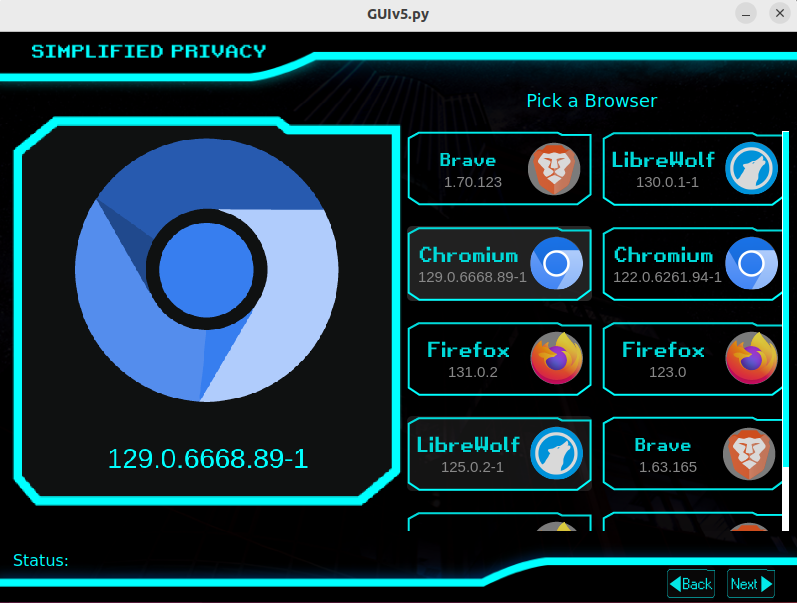
But then I saw their new VPN. This thing creates a second new lightweight graphical environment, that realistically hides from browsers your actual screen size. While having instant load and zero resource consumption or disc space.
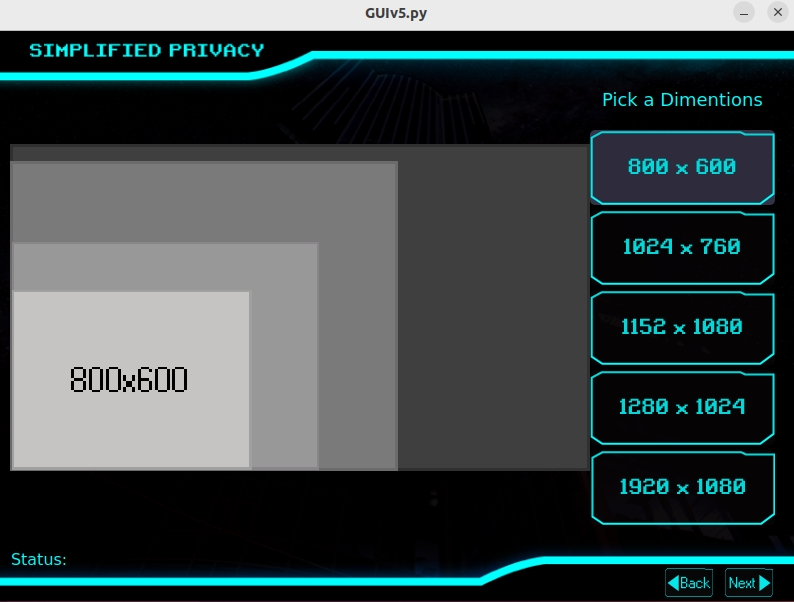
Unlike Mullvad-Tor Browser, where you accidentally make it full-screen and the jig is up. Simplified Privacy even puts this 2nd new graphical environment in a virtual cage, so you can’t fuck up. And to the website, it doesn’t appear to be spoofed.
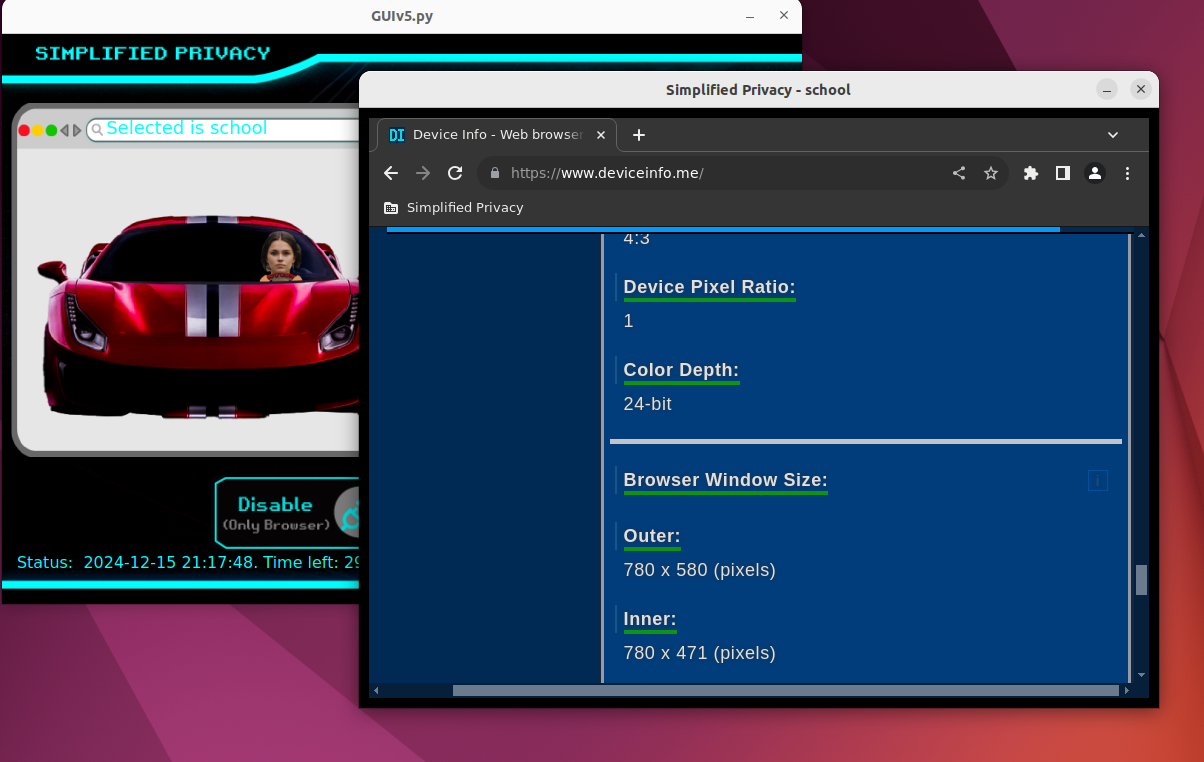
Then they isolate the filesystem in this fake environment, to control what files that application sees and uses in order to improve privacy. And finally establish an exclusive, secure, connection for the browser to hide your actual location.
Cloudflare ain't got shit on me.
~~~~
Explain it like Cloudflare

Hi, I'm a Junior Communications Analyst for Cloudflare Inc.
SimplifiedPrivacy is trying to abuse baseless conspiracy theories to paint our AI detection as nefarious. In reality, our AI can protect your website from DDoS attacks. Our AI already assigns a trust score to every IP address, and someday every device.
SimplifiedPrivacy claims using our service is quote "joining the borg". But if you're doing nothing wrong, you have nothing to hide. And we delay or block Tor users to deal with rising cybersecurity threats.
While SimplifiedPrivacy's rhetoric is harmful misinformation, their service actually HELPS us. Because they offer Tor -> Socks5 proxy routing.
This enables end-users to enjoy the privacy of Tor, while allowing us to easily block SimplifiedPrivacy's IP addresses, IF they refuse to stop DDoS coming through them. So if you're complaining about our treatment of Tor users, then go use SimplifiedPrivacy.
~~~~
Explain it like a Mullvad fanatic

PrivacyGuides-org recommends Mullvad. Yes Mullvad used Gmail to buy servers and do customer service, but as PrivacyGuides-org responded on their forums, it was a paid account so Google doesn't scan it.
While I dislike their marketing, I like that Simplified Privacy uses different datacenters and providers than Mullvad and the other VPNs. This way, I can continue to use Mullvad for my system-wide traffic. And then use Simplified Privacy for just the browser, so I know have two completely different hops.
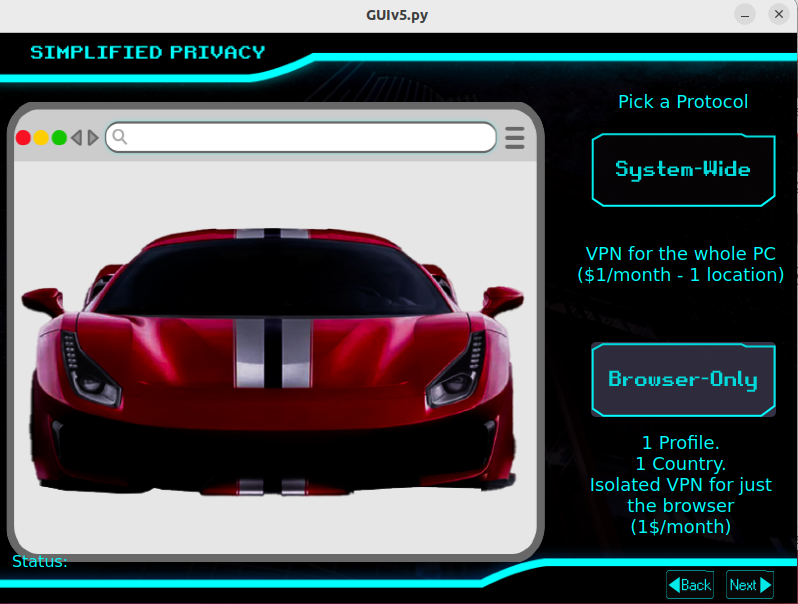
Because Simplified Privacy hates Mullvad so much, I know they aren't colluding. And this is much easier than Qubes.
~~~~
Explain it like Qubes

I'm Joanna Rutkowska the creator of QubesOS and author of InvisibleThings.
SimplifiedPrivacy is obsessed with my blog post from 2011 that:
There's a huge flaw in Linux, that ALL programs can see the display for ALL other programs. This means ANY software you run, can see your password manager like KeePass. Visually looking at all your KeePass entries, to know about your whole life.
Even worse, all programs share the keyboard, so it means a non-sudo program can capture the sudo password. Or even see what's going on in a sudo terminal.
Linux still has this problem a decade later. Qubes protects you against this, and that's what you should be using if you're worried about running untrusted software.
I'm not endorsing them, and I didn't audit it. But SimplifiedPrivacy claims to protect against these problems, since they create a 2nd graphical display, but it's more-so targeted at browser break-out.
But why don't you stop using my name, and stand up for your own project?
~~~~
Explain it in my own words

Mullvad executives were born in Sweden. Fine, good for them.
I'm moving countries to do this. Goodbye to my family dude. Learn a new language. It's fuckin real.
I told the girl I was dating, I can't marry her. It's not fair to her, I don't have the time to devote to her. This project is my child.
I sold the shirt off my back to make this happen. We're running on PGP-debt now. The engineers took a fraction of what they can make in the fiat corporate world, doing it for the love.
But now that debt is coming due, and with 10 servers running, I've got to persuade enough people to:
a) Use Linux
b) Use Cryptocurrency
c) Use this on Linux with Crypto
Or we will go bankrupt, and my dream will die. But regardless of if it succeeds, I am so proud of the team for making it. And if I'm crazy enough to start it, I'm crazy enough to think it might work.
So if you want to see this happen: Smash that repost, and let's spread the knowledge to our Nostr family.


























