I think, if someone joins nostr, and stays on nostr:
They are willing to learn.
Probably learning curve shall be simplified, but I see this as a great bar to enter.
#nostr #grownostr
I believe this is correct. What I’m unsure of is whether you can create your new parent/bunker key, and give it “ownership” of an existing keypair.
What I would love to do someday is create an “offline” master nsec, and somehow — like in Bitcoin — use it airgapped to sign a message or otherwise give my nsecbunker admin control over any of my existing primary Nostr keypairs.
So the two contrasts with how I currently understand nsecbunker to function are, 1) offline key generation and storage and 2) delegation/control over existing keys and not simply generating new “child” keys in-app.
This account ( nostr:npub14qz92uedt0a8jte8jqg63jr3s5cc99cej36jh883z6tprlu354uqqe2q26) is my daily driver. It’s my nym and my social graph, whereas my other keys are primarily used for client testing and Other Stuff. I generated this key inside Damus back in 2022: it has never touched another client and I’d love to keep it that way.
Thus my daydream: an offline-generated-and-stored “parent” nsec with the ability to “adopt” child accounts that already exist.
Heh, yo nostr:npub1l2vyh47mk2p0qlsku7hg0vn29faehy9hy34ygaclpn66ukqp3afqutajft what are the chances of this “adoption” thing working in nsecbunker at some point?
I think you can add nsecs to bunkers, that were not generated there, but it won't have a parent key or so.
I think there are already some way to do airgapped signing, but not sure if it is already convenient.
But you need to keep in mind, that if you have to approve all actions, then it will be really bad UX for decrypting DMs e.g. Except if you can somehow bulk approve.
Amber (android) signer seems to do that btw. The bulking.
But also, we are getting there with nostr DMs as well 🤙
You don't need haskell for it.
You can use it in any programming language, you just have to host the cli with it as well.
Not too complicated, and you get a private solution.
I already did it in python.
GM! ☕️
If I understand correctly, when you use a nsec bunker, only your bunker knows your nsec, and each logged in app, will get an own new keypair that it can use to make interactions on your behalf.
But this right can be withdrawn anytime simply.
So if your account is compromised, you can just delete the right of that keypair.
The only real danger is then, that the bunker itself gets compromised, and your real nsec leaks. From that, it is kind of impossible to recover.
So bunker does not solve fully the leak problem, but makes it so much better.
But if you think about it. With power comes responsibility.
#asknostr #grownostr #plebchain
There are acounts that posts many invoices everyday. Seems to me, they are trying to milk nostr.
I think, buying products does not make you happy, only cause you joy.
But the sellers and society tries to convince us, that what we feel when we buy new pair of shoes is happiness.
But I think it is incorrect.
Happiness is generated inside. Joy is caused by external things.
Joy disappears, happiness stays.
Just my 2 cents.
#RRR
Random Run 'Round
To build a new system, we will need legends, the best of bests.
We are in a really good shape.
As comments you mean?
Use digital, so we can find the "bad guys".
*Bad guys: the definition is defined by us on the fly, so that we can solve "any" problems.
Out of Context Spam Filtering
How about hiding by default comments that are out of context. Usually spam is fully out of context, or?
#asknostr #nostr #plebchain
In an infinite game, there is no winning, only surviving.
You could win "battles", but what does it worth if you fall out of "business".
This is the #IndiaStack (thanks nostr:npub16dhgpql60vmd4mnydjut87vla23a38j689jssaqlqqlzrtqtd0kqex0nkq ).
Maybe it’s just me, but I think #nostr has this already covered with npubs, zaps and relays. 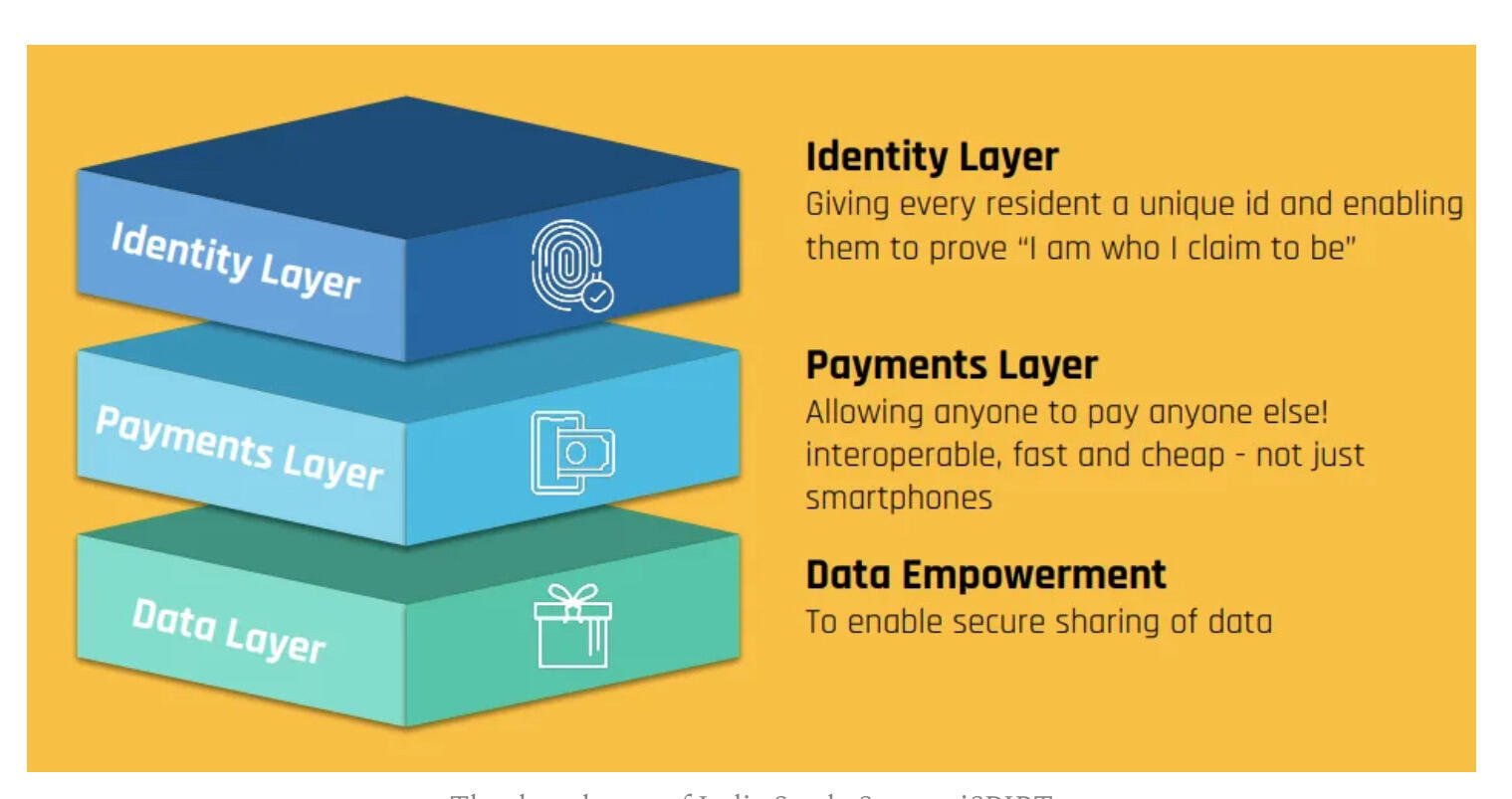
Lol, if you put it this way.
I would call nostr a pseudo-anonym identity layer. But what else would you need?
Hmmm. Imagine you could identify yourself to webshops with just signing a http auth. No more phone auth, email auth, telling your cats name, etc. Just a simple signature.
But, raises the question of "identity leaks". How do you recover from such?
Every action has an anti-action.
Did you know
that amazon fair pricing policy drives up the prices of items outside of amazon too?
#nostr #amazon #grownostr