nostr:nprofile1qqs24yz8xftq8kkdf7q5yzf4v7tn2ek78v0zp2y427mj3sa7f34ggjcpzamhxue69uhhv6t5daezumn0wd68yvfwvdhk6tcppemhxue69uhkummn9ekx7mp0qyg8wumn8ghj7mn0wd68ytnddakj703s8dt. When I open the about me/description section in my profile editor, "Recommends:" isn't there.
Tried using Primal, same issue.
I'm just struggling to figure out where that "Recommends:" bit is coming from or why it's showing up.
Go to About Me and do Select All, delete, save.
Which client are you using?
Check again, be sure you saved, if you did, it could be a case of "location", if you are using a VPN try changing server to a different country.
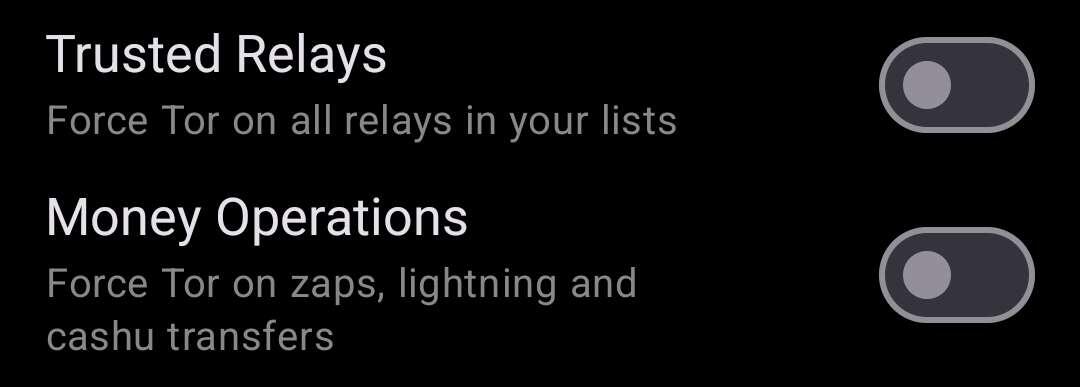
I am unable to zap from amethyst using tor built-in feature from nostr:nprofile1qqst4qyeqenw7zm0fwjsty68h6cnys5jre2xd8ngqpjv5a2j26s78fspzemhxue69uhhyetvv9ujucm0d9hx7uewd9hj75a0pev wallet, anyone knows how to solve this?
#asknostr
That will be the case with any NWC
Workaround:
Toggle off these two
Many theories,
The hoax one:
Which fails to explain,
1. The accuracy,
2. The speed in which they are done (at night in open farm fields over night, in silence)
3. The silence in which they are done, this amount of work requires lots of labor and loud machines, done overnight in a farm field would wake up anyone in the vicinity.
The extraterrestrial one:
Nothing to back it up AFAIK...
Hopefully someone else will offer more insight in the matter, it is truly interesting and puzzling
A VPN is a good choice to improve your privacy if needed, just understand that it is not a perfect solution
Rule of thumb: select a VPN that do not KYC you and the payment method matters, if they do not accept Bitcoin or even better Monero,I would not consider it as appealing
Follow nostr:nprofile1qqs80n2hqvjppgqh2c5t2dtl5e2mr7kw4d90u468xwaaenke8r0frgspz3mhxue69uhhyetvv9ujuerpd46hxtnfduq3samnwvaz7tmjv4kxz7fwwdhx7un59eek7cmfv9kqzxthwden5te0wpuhyctdd9jzuenfv96x5ctx9e3k7mg6k4xa4 and check mullvad.net, both solid solutions
.- coinos.io (supports eCash and on Chain Bitcoin and Lighting)
.- minibits.cash (eCash and LN)
.- Wallet of Satoshi (LN)
.- npub.cash (LN, eCash)
All the above allow you to create your LN address if available
More wallets will join soon, just a matter of time.
That feed is loaded with both video and images (mainly memes). ...
You can't get #Amethysts? iPhone I guess, quite limiting in customization, variety of applications and not ideal for your digital privacy
nostr:nprofile1qqs24yz8xftq8kkdf7q5yzf4v7tn2ek78v0zp2y427mj3sa7f34ggjcpzamhxue69uhhv6t5daezumn0wd68yvfwvdhk6tcppemhxue69uhkummn9ekx7mp0qyg8wumn8ghj7mn0wd68ytnddakj703s8dt, suggestion, an idea from this post. A filter to select only images or only videos in the tiktok like feed would be quite appealing 🚀
I'll try and let you know, on the road, can't right now, will do that with my PC
nostr:nprofile1qqs24yz8xftq8kkdf7q5yzf4v7tn2ek78v0zp2y427mj3sa7f34ggjcpzamhxue69uhhv6t5daezumn0wd68yvfwvdhk6tcppemhxue69uhkummn9ekx7mp0qyg8wumn8ghj7mn0wd68ytnddakj703s8dt, Is there a guide to enable the notifications in #Amethyst successfully?
My experience so far have been non positive:
The steps suppose to be simple:
1. Install NTFY
2. Open Amethyst and go to settings, select "Push Notifications", select NTFY
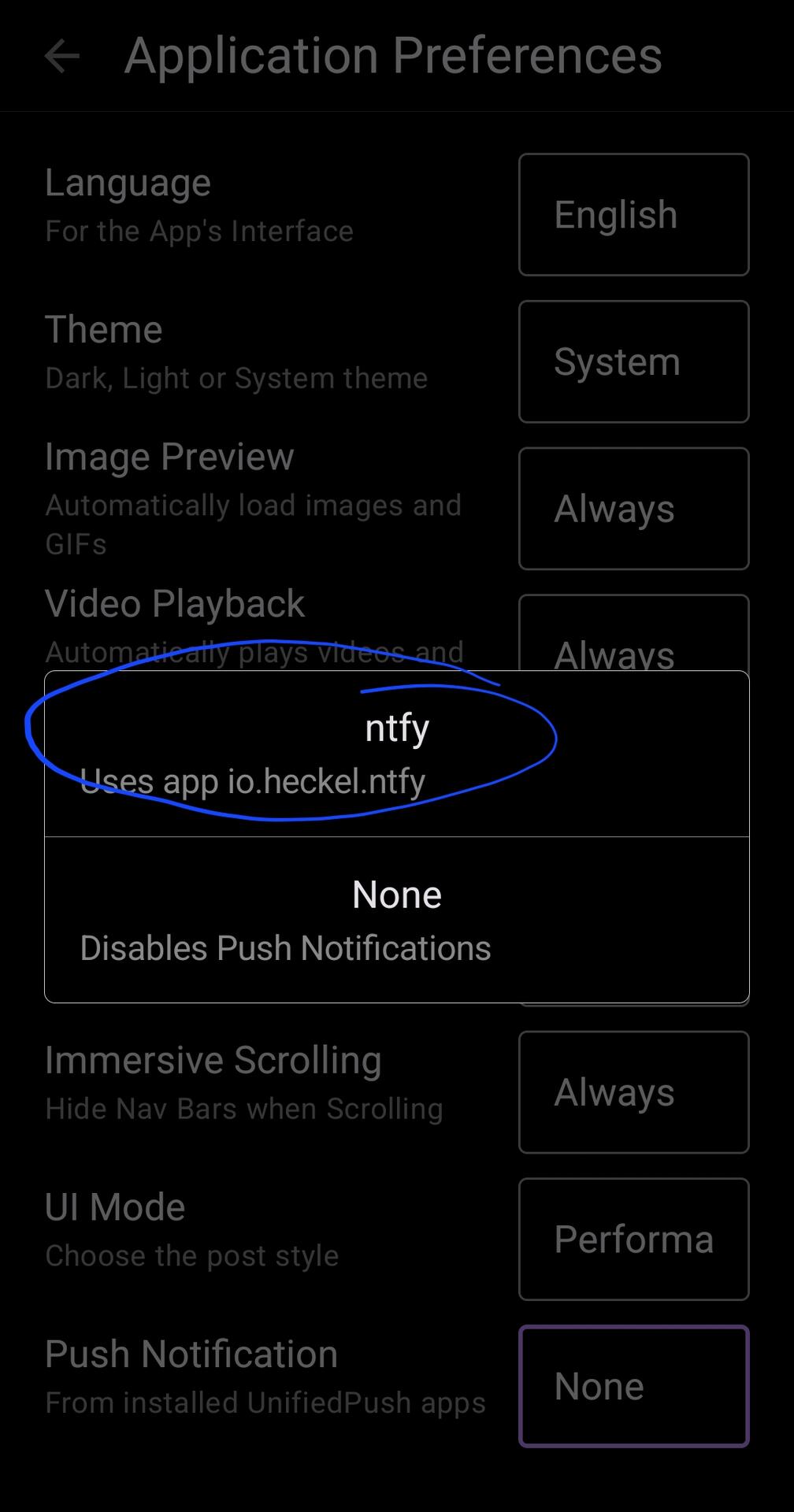
Done, very simple, but, didn't work for me... No notifications arrived for zaps or DMs, okay, troubleshooting time... Clear cache in both apps, nope, checked I have good trustable relays for DMs, yep, all good, uninstalled NTFY, installed again, repeated the process, worked!
Hmmm, but why? Need to know... Uninstalled NFTY again, installed it again, repeated the process, no dice, not working, repeated the process around 10 times, no dice :(
Anyone with a similar experience that can give me a hint as to what it can be the problem?
nostr:nprofile1qqs24yz8xftq8kkdf7q5yzf4v7tn2ek78v0zp2y427mj3sa7f34ggjcpzamhxue69uhhv6t5daezumn0wd68yvfwvdhk6tcppemhxue69uhkummn9ekx7mp0qyg8wumn8ghj7mn0wd68ytnddakj703s8dt, Any plans to add native notifications to the app?
#asknostr
#notifications
#Nostr
Tried it once, didn't work, forgot about it.
Just tried again, doesn't work for me either, I don't think is a working feature. I wish it was added "natively" as you stated.
Did you click on maybe later? It is great they added that if it really works, I will try again and create a new account.
Few months ago was helping a friend setup an account, impossible without mobile or email verification. I reach out to Proton and they stated it was for security to avoid spam and that they did not keep that information... sure... tried tuta, the same... so had to use a disposable email to continue
nostr:nprofile1qqstxwlea9ah3u6kjjszu6a7lrnhqkfh8eptp2z6v0e9558tlkkl2rgpzemhxue69uhk2er9dchxummnw3ezumrpdejz7qgwwaehxw309ahx7uewd3hkctcpremhxue69uhkummnw3ez6ur4vgh8wetvd3hhyer9wghxuet59u4kl3vp just added biometric protection to the app plus a very appealing golden dark theme
Looking great!
#Wallets
#Minibits
#Nostr
And yet, most IT current workforce needs to reinvent themselves and fast, AI is taking already all low entry level jobs, but that will come soon to medium and high level, very few niches will still require the human labor
There are services that have implemented already some of these solutions, check them out, one is Mullvad VPN, someone sent me this snapshot while discussing the same subject in a CyberSec forum
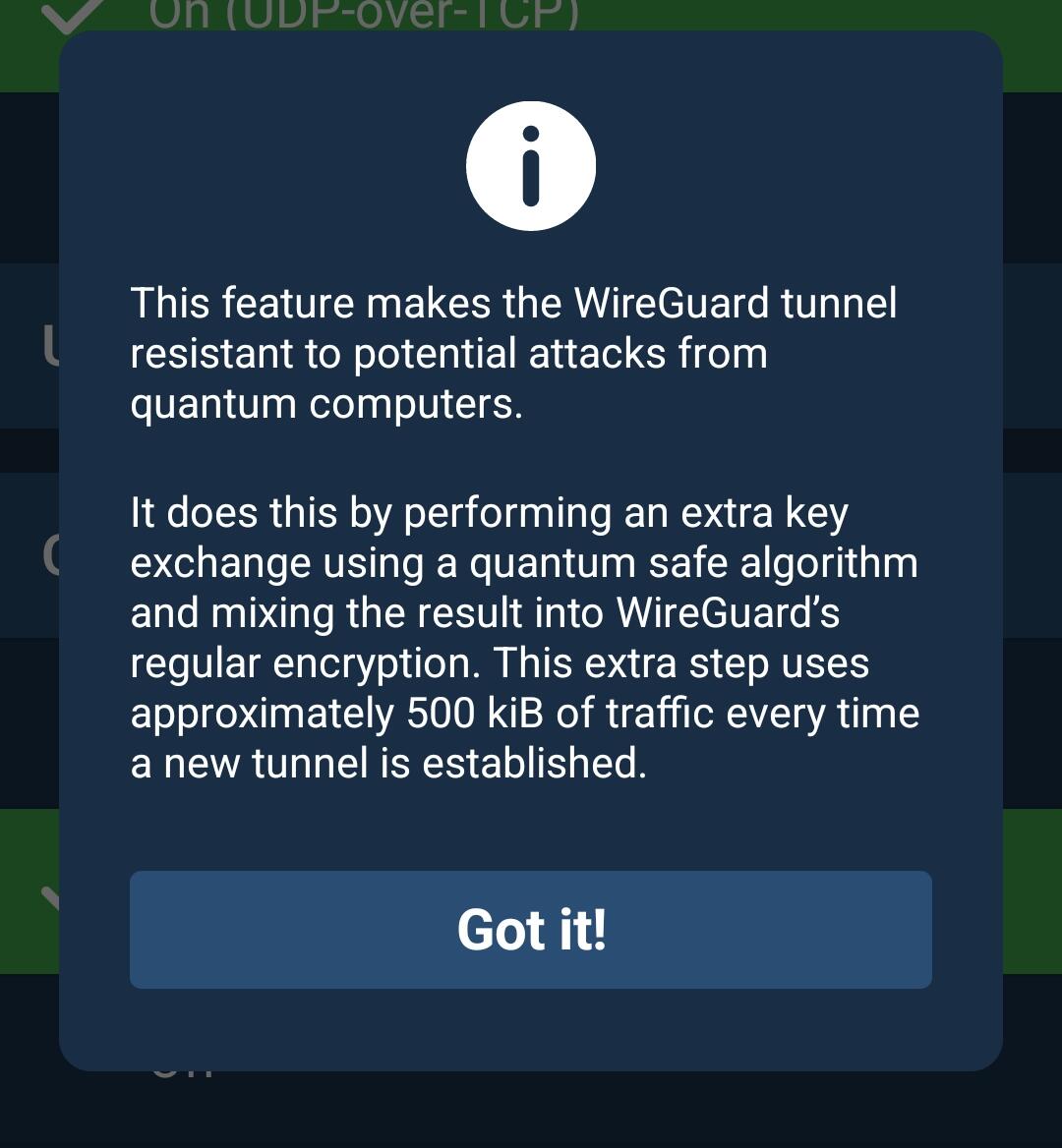
Check nostr:nprofile1qqs24yz8xftq8kkdf7q5yzf4v7tn2ek78v0zp2y427mj3sa7f34ggjcpzamhxue69uhhv6t5daezumn0wd68yvfwvdhk6tcppemhxue69uhkummn9ekx7mp0qyg8wumn8ghj7mn0wd68ytnddakj703s8dt, Primal has the tendency to filter a lot of content
Q2:
Post-Quantum Cryptography: One approach to combat quantum attacks on classical encryption is to transition to post-quantum cryptography (PQC). PQC algorithms rely on mathematical problems that are believed to be hard for both classical and quantum computers, such as lattice-based, code-based, and multivariate cryptography. Implementing PQC standards and protocols would ensure continued security even if quantum computers become powerful enough to break classical encryption.
Key Exchange and Rekeying: Another strategy is to focus on key exchange and rekeying mechanisms. In the event of a quantum computer breaking classical encryption, rekeying with fresh, post-quantum secure keys would mitigate the impact. This approach would require frequent key updates and efficient key management systems.
Hybrid Approach: A hybrid approach combines classical and post-quantum cryptography. This involves using classical encryption for initial communication and then transitioning to post-quantum encryption for sensitive data or long-term storage. This hybrid approach would provide a temporary buffer against quantum attacks while PQC standards are widely adopted.
Error-Correcting Codes: Improving error-correcting codes for quantum computers could also help combat quantum attacks. By reducing the number of physical qubits required for logical qubits, error-correcting codes could make it more difficult for quantum computers to achieve a sufficient number of qubits to break classical encryption.
Quantum-Resistant Hash Functions: Developing quantum-resistant hash functions would provide an additional layer of security. Hash functions are used in digital signatures and message authentication codes, and quantum-resistant variants would ensure the integrity of data even if quantum computers become powerful enough to break classical hash functions.
Monitoring and Adaptation: Finally, it's essential to continuously monitor the development of quantum computing and adapt cryptographic protocols and algorithms accordingly. This would involve staying informed about advancements in quantum computing, assessing their potential impact on cryptography, and updating cryptographic standards and practices as needed.