nostr:npub1getal6ykt05fsz5nqu4uld09nfj3y3qxmv8crys4aeut53unfvlqr80nfm is it possible to use https://github.com/getAlby/bitcoin-connect without having to show this popup every time you open the app 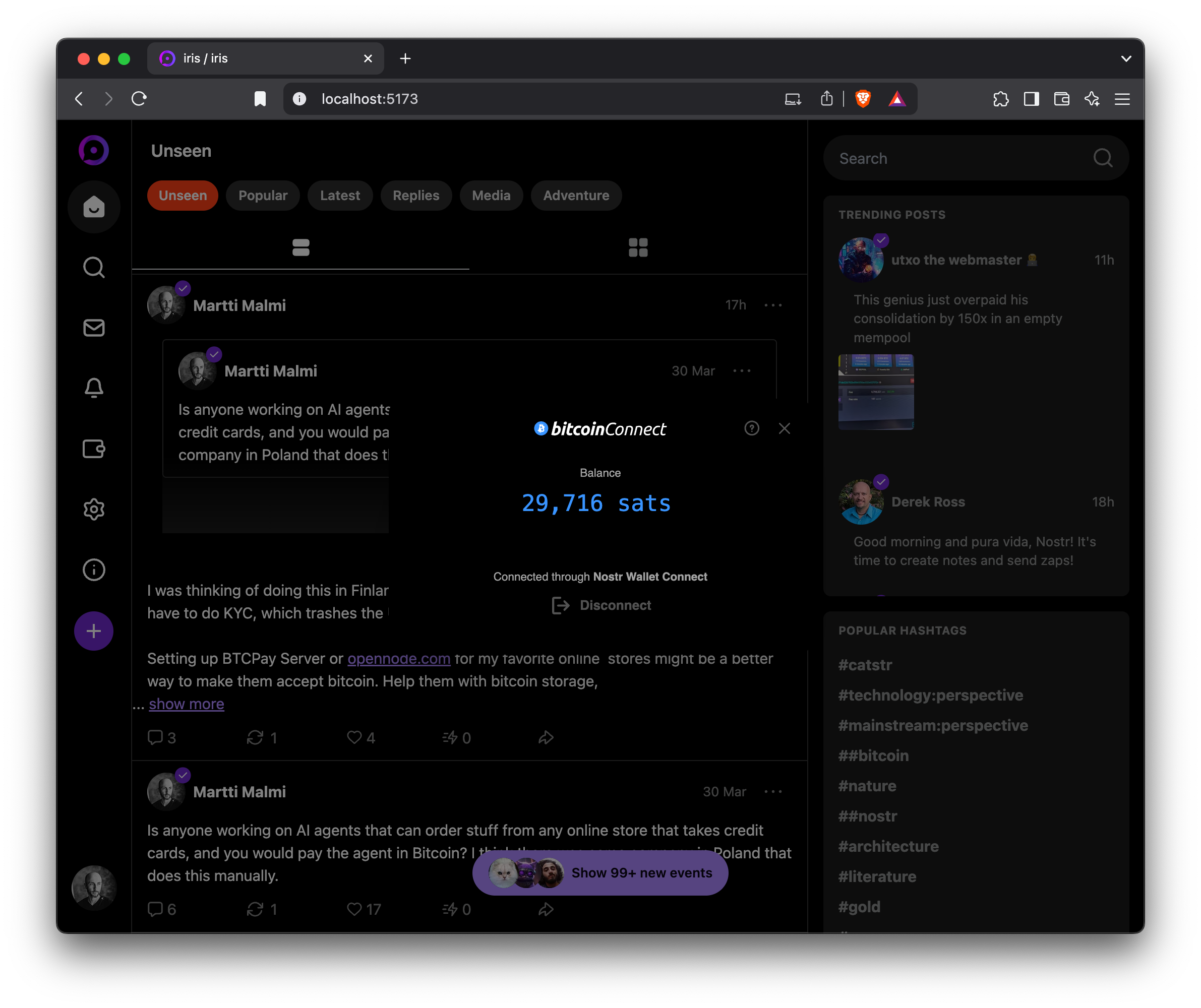
I was thinking of doing this in Finland, but then you'd be a money transmitter and probably have to do KYC, which trashes the UX and defeats the purpose.
Setting up BTCPay Server or https://opennode.com for my favorite online stores might be a better way to make them accept bitcoin. Help them with bitcoin storage, exchange and accounting. The EU kindly doesn't yet require KYC from them.
What would be even more rad? Crawl online stores onto Shopstr, let users send orders that are paid in Cashu. Notify merchant of pending orders and let them redeem the nuts. User can reclaim the payment if merchant did not respond.
Nostriches could maintain collections / virtual stores of their favorite items by various merchants, and get a referral bonus when people buy from them 🤔
I'd do a "non-fiat swag" virtual store that lists high quality merchandise made of durable materials like wood, leather, hemp or steel, instead of the usual plastic made in China.
I was thinking of doing this in Finland, but then you'd be a money transmitter and probably have to do KYC, which trashes the UX and defeats the purpose.
Setting up BTCPay Server or https://opennode.com for my favorite online stores might be a better way to make them accept bitcoin. Help them with bitcoin storage, exchange and accounting. The EU kindly doesn't yet require KYC from them.
What would be even more rad? Crawl online stores onto Shopstr, let users send orders that are paid in Cashu. Notify merchant of pending orders and let them redeem the nuts. User can reclaim the payment if merchant did not respond.
When ordering online, you’re doxxing your mailing address anyway. Convenience of paying with bitcoin is the point here. Also lightning is pretty good privacy wise.
Is anyone working on AI agents that can order stuff from any online store that takes credit cards, and you would pay the agent in Bitcoin? I think there was some company in Poland that does this manually.
Meshtastic is interesting, but apps that work on every phone over bluetooth and wifi would have better reach, and simpler setup
Briar: "Censorship-resistant peer-to-peer messaging that bypasses centralized servers. Connect via Bluetooth, Wi-Fi or Tor, with privacy built-in." https://briarproject.org/
Would be cool to have bluetooth & wifi sync on native Nostr apps. Would be useful in offline situations and countries where the internet is censored.
Yes, it's the northernmost part of Finland, near the Norwegian border. It felt almost like a different country from South Finland ❄️
Eivør & Heilung in Helsinki last week https://video.nostr.build/3f7743986a99bbd7becf1830ef82bca9b3e61458217fcb6d404021a91975967d.mp4 https://video.nostr.build/77a1e2e6a19b7373bc3e4827dff55de2f834e1e7cd20ac04a169fd874e7ddc12.mp4 https://video.nostr.build/3073b53c630a66d84071f2d7a09aeef6db245c65f2d8c5244da8d1d60c747387.mp4  https://video.nostr.build/53a40ae19ab1259ab2b58aafdbf7301b8feab97213df03bf4cee98020cffcac1.mp4 https://video.nostr.build/d7e79b02c3a76c6a32d12cac9042e099937f8c32e227dd58aff78a0e6878bd4d.mp4
https://video.nostr.build/53a40ae19ab1259ab2b58aafdbf7301b8feab97213df03bf4cee98020cffcac1.mp4 https://video.nostr.build/d7e79b02c3a76c6a32d12cac9042e099937f8c32e227dd58aff78a0e6878bd4d.mp4
Eivør & Heilung fan 
Eivør & Heilung in Helsinki last week https://video.nostr.build/3f7743986a99bbd7becf1830ef82bca9b3e61458217fcb6d404021a91975967d.mp4 https://video.nostr.build/77a1e2e6a19b7373bc3e4827dff55de2f834e1e7cd20ac04a169fd874e7ddc12.mp4 https://video.nostr.build/3073b53c630a66d84071f2d7a09aeef6db245c65f2d8c5244da8d1d60c747387.mp4  https://video.nostr.build/53a40ae19ab1259ab2b58aafdbf7301b8feab97213df03bf4cee98020cffcac1.mp4 https://video.nostr.build/d7e79b02c3a76c6a32d12cac9042e099937f8c32e227dd58aff78a0e6878bd4d.mp4
https://video.nostr.build/53a40ae19ab1259ab2b58aafdbf7301b8feab97213df03bf4cee98020cffcac1.mp4 https://video.nostr.build/d7e79b02c3a76c6a32d12cac9042e099937f8c32e227dd58aff78a0e6878bd4d.mp4
Posts are marked as "seen" when they've been in the viewport for 1 second
nostr:nprofile1qqsy2ga7trfetvd3j65m3jptqw9k39wtq2mg85xz2w542p5dhg06e5qpz4mhxue69uhhyetvv9ujuerpd46hxtnfduhszxrhwden5te0dehhxarj9enx6apwwa5h5tnzd9az7qgwwaehxw309ahx7uewd3hkctczcs834 is that algo self-contained and/or documented or open-source? I'd very much enjoy having something similar in my self-hosted version of nostr:nprofile1qqszv6q4uryjzr06xfxxew34wwc5hmjfmfpqn229d72gfegsdn2q3fgpr3mhxue69uhhxct5v4kxc6t5v5hxs7njvscngwfwvdhk6tcpzfmhxue69uhkummnw3e82efwvdhk6tcpz4mhxue69uhhyetvv9ujuerpd46hxtnfduhsk7wj75 's noStrudel
"Unseen" feed just shows posts you haven't seen before, latest first. "Popular" takes last 200 likes by your follows and shows most popular posts first.
I'm thinking of combining unseen and popular feeds into a "for you" feed. It would intertwine latest and popular posts, unseen only. Maybe limit consecutive posts from same author.
I enabled zap receipts from pubkeys outside your social graph (like many zap receipt issuers are) and now most zaps are visible again on iris.to.
I'm terrified of the possibility of fake zap receipts, but for some reason no one has spammed them yet 😄 Maybe at least nip05 should be checked for zap receipt issuers, although that's not a long term solution.
you can long-press the like button for emoji reaction
Also added a bunch of zapping & wallet improvements. If you're using the Iris cashu wallet, it's now in the background and you can manually wallet-connect it and one-click-zap with it. Working on auto.
iris.to replies and quotes might be targeting correctly now, finally
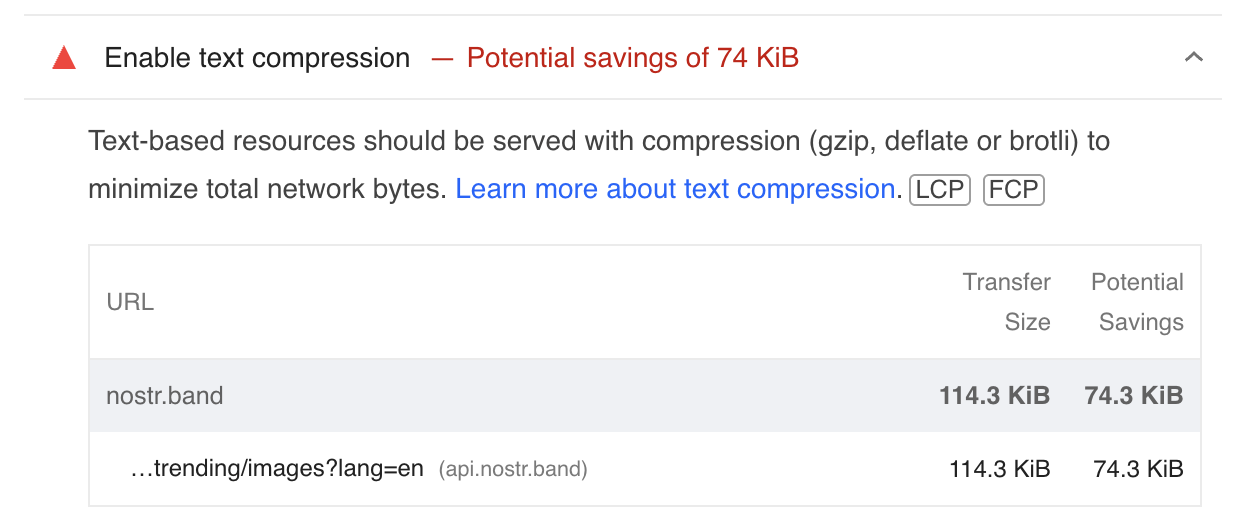
Routing it through a CDN or nginx might be the easiest way to add it
any plans on NIP-30 support on Iris nostr:npub1g53mukxnjkcmr94fhryzkqutdz2ukq4ks0gvy5af25rgmwsl4ngq43drvk?
Added nip-30 support for kind 1. I don’t see them used much though. Mostly some mostr.pub enthusiasts.
Lugano was so much more crazy and fun than I expected 😄
I played my first gig since high school. Can't wait for the next Rockamoto!
nostr:npub1jt97tpsul3fp8hvf7zn0vzzysmu9umcrel4hpgflg4vnsytyxwuqt8la9y nostr:npub1fk8h6g8zhftw8c7pga2zjd84p2z949up5lc3qdchm9v4m0q7mwws7jcwld nostr:npub1excellx58e497gan6fcsdnseujkjm7ym5yp3m4rp0ud4j8ss39js2pn72a nostr:npub1lr2zzf989mvf393y0tv39ara6a4vddkd6y87z784up9vl6ks6j3qtudl6a nostr:npub1au23c73cpaq2whtazjf6cdrmvam6nkd4lg928nwmgl78374kn29sq9t53j nostr:npub1ydxytlu95vwpn0m3pzn507nma8x5472u043pupcgpj3dvcamglfql6rlcw nostr:npub1z77juddgcul5la7jq578nsurpxh99633ccanngf863m4gh6gv2msm009sr
https://video.nostr.build/bfcda3d2f4c4d0e6cea5cf2f998307d7ada0bc42858b48864c4a9bd28359c1b7.mp4
https://video.nostr.build/ef74d46ad5dbed1eba0530b070b8175ecd2e44d00e0bb6ab1bdbe27997c89342.mp4

You have a point. The user's own avatar is one of the first images shown on the page, in a certain size, so you could even guess the Nostr user.
Without the proxy, requests are sent to multiple servers, making it more difficult to associate everything the user does.
On the other hand, those other image hosts might include those that are built expressly for logging and tracking users. Popular service like nostr.build or imgur.com can do that kind of analysis anyway.
Using a proxy, you can at least choose which host(s) you trust. Ultimately, the choice of proxy should be configurable, just like relays. Image loading without proxy is privacy-wise somewhat equivalent to outbox model (or nip05) where you connect to random addresses that see your requests.
Relays also know a lot about what you're looking at, and you might even reveal your identity by authenticating. The only way I see around this is onion routing where Nostr requests would be relayed on behalf of others, so there's plausible deniability.
Associating network address to a geolocation is a feature of the internet protocol. Tor and VPNs (where you also need to trust a 3rd party) seem to be the only solutions to that.
When it comes to image proxying, file size is one very pragmatic consideration. Without a minimizing proxy, avatars can be 100 times larger. Maybe multi-resolution image formats are the best solution to that.
Maybe we can have something like Signal for connecting sessions on different devices / clients so they see the same messages.
Full write access to everyone is not an option. Unconnected newbies could maybe zap to get noticed.
I'll be there
Matthew Green's (cryptography prof at Johns Hopkins) take on Apple's "Private Cloud Compute": https://threadreaderapp.com/thread/1800291897245835616.html?utm_campaign=topunroll
"So Apple has introduced a new system called “Private Cloud Compute” that allows your phone to offload complex (typically AI) tasks to specialized secure devices in the cloud. I’m still trying to work out what I think about this. So here’s a thread.
1/
Apple, unlike most other mobile providers, has traditionally done a lot of processing on-device. For example, all of the machine learning and OCR text recognition on Photos is done right on your device.
2/
The problem is that while modern phone “neural” hardware is improving, it’s not improving fast enough to take advantage of all the crazy features Silicon Valley wants from modern AI, including generative AI and its ilk. This fundamentally requires servers.
3/
But if you send your tasks out to servers in “the cloud” (god using quotes makes me feel 80), this means sending incredibly private data off your phone and out over the Internet. That exposes you to spying, hacking, and the data hungry business model of Silicon Valley.
4/
The solution Apple has come up with is to try to build secure and trustworthy hardware in their own data centers. Your phone can then “outsource” heavy tasks to this hardware. Seems easy, right? Well: here’s the blog post.
5/
https://security.apple.com/blog/private-cloud-compute/
TL;DR: it is not easy. Building trustworthy computers is literally the hardest problem in computer security. Honestly it’s almost the only problem in computer security. But while it remains a challenging problem, we’ve made a lot of advances. Apple is using almost all of them.
6/
The first thing Apple is doing is using all the advances they’ve made in building secure phones and PCs in their new servers. This involves using Secure Boot and a Secure Enclave Processor (SEP) to hold keys. They’ve presumably turned on all the processor security features.
7/
Then they’re throwing all kinds of processes at the server hardware to make sure the hardware isn’t tampered with. I can’t tell if this prevents hardware attacks, but it seems like a start.
8/
They also use a bunch of protections to ensure that software is legitimate. One is that the software is “stateless” and allegedly doesn’t keep information between user requests. To help ensure this, each server/node reboot re-keys and wipes all storage.
9/
A second protection is that the operating system can “attest” to the software image it’s running. Specifically, it signs a hash of the software and shares this with every phone/client. If you trust this infrastructure, you’ll know it’s running a specific piece of software.
10/
Of course, knowing that the phone is running a specific piece of software doesn’t help you if you don’t trust the software. So Apple plans to put each binary image into a “transparency log” and publish the software.
But here’s a sticky point: not with the full source code.
11/
Security researchers will get *some code* and a VM they can use to run the software. They’ll then have to reverse-engineer the binaries to see if they’re doing unexpected things. It’s a little suboptimal.
12/
When your phone wants to outsource a task, it will contact Apple and obtain a list of servers/nodes and their keys. It will then encrypt its request to all servers, and one will process it. They’re even using fancy anonymous credentials and a third part relay to hide your IP.
13/
Ok there are probably half a dozen more technical details in the blog post. It’s a very thoughtful design. Indeed, if you gave an excellent team a huge pile of money and told them to build the best “private” cloud in the world, it would probably look like this.
14/
But now the tough questions. Is it a good idea? And is it as secure as what Apple does today? And most importantly:
I admit that as I learned about this feature, it made me kind of sad. The thought that was going through my head was: this is going to be too much of a temptation. Once you can “safely” outsource tasks to the cloud, why bother doing them locally. Outsource everything!
As best I can tell, Apple does not have explicit plans to announce when your data is going off-device for to Private Compute. You won’t opt into this, you won’t necessarily even be told it’s happening. It will just happen. Magically.
I don’t love that part.
17/
Finally, there are so many invisible sharp edges that could exist in a system like this. Hardware flaws. Issues with the cryptographic attenuation framework. Clever software exploits. Many of these will be hard for security researchers to detect. That worries me too.
18/
Wrapping up on a more positive note: it’s worth keeping in mind that sometimes the perfect is the enemy of the really good.
In practice the alternative to on-device is: ship private data to OpenAI or someplace sketchier, where who knows what might happen to it.
19/
And of course, keep in mind that super-spies aren’t your biggest adversary. For many people your biggest adversary is the company who sold you your device/software. This PCC system represents a real commitment by Apple not to “peek” at your data. That’s a big deal.
20/
In any case, this is the world we’re moving to. Your phone might seem to be in your pocket, but a part of it lives 2,000 miles away in a data center. As security folks we probably need to get used to that fact, and do the best we can to make sure all parts are secure.
//fin
Addendum: “cryptographic attenuation” should read “cryptographic attestation”, but I’m sure folks will get the point."
#apple #privacy #AI
Sounds like it's still a black box, a trusted 3rd party.
My email correspondence with Satoshi in 2009-2011: https://mmalmi.github.io/satoshi/
Bitcoin is the free market alternative to banks and government money. How can we do a free market alternative to insurance companies?
Insurance is the natural enemy of public harms like the junk food industry. It could even proactively protect our personal safety and health.
The problem is, just like banks, current insurance companies are behemoths that are entwined in the system and lobby the government to stifle competition and innovation.
We need free market insurance that is independent of government institutions, just like Bitcoin.
Fiat culture, high time preference. Buildings owned by investment firms, not the people who live or work there.
I originally started Iris without any framework and learned the hard way why frameworks are used. Now using preact, a lightweight react variant.


👍

Spam prevention should work by discarding events from users that are not connected to your social network like normal users are. For example, swarms of users that are connected by only 1 or less follows from legit users.
Iris already discards messages from completely unconnected users, but need to add shared block list support and better detection of sybil swarms.
This should work especially for trending algorithms, where reactions from socially connected users are more valuable anyway, and missing a like doesn't matter so much.
Currently Iris trending list comes from nostr.band, but I want to do it locally at some point. That's the only way you know what you get.
Iris now supports secret chats that don't leak metadata, implementing the https://hrfbounties.org/ bounty #3. It works also for group messaging.
It's a quick & dirty solution, but works. A shared nostr account is created for the secret chat / group. Its nsec can be shared via link, qr code or invite message from a single-use anonymous account.
Users can then communicate using the shared account's messages-to-self. Iris signs the inner messages with your own key, but the arrangement could be used for anonymous group messaging as well.
I'll also add inner message encryption at some point, so you can ensure that only certain group participants can read the message.
This arrangement doesn't introduce any new event kinds and works also in clients that haven't implemented a special UX for it. You can just log in with the nsec and message yourself.
I had to disable the Iris social graph filter to let invites through, so now Iris DMs are open to spam again, but I'll try to figure out a better solution.
As always, the UX needs a lot of attention, but I believe here's an MVP.
Screenshots:
Alice wants to message Bob:

Alice sends a secret chat invite to Bob:

Bob automatically follows the invite from Alice. They can now message each other in the secret chat:

Here's how the invite looks in another client. I will add an "nostr:ninvite" URI in addition to the nsec.

Use Iris, not retina!