I’m here #🌝
Interesting attack on VPN services.
Thoughts? nostr:npub1f6ugxyxkknket3kkdgu4k0fu74vmshawermkj8d06sz6jts9t4kslazcka
It seems to me that any cellular network should be considered a hostile network.
Researchers have devised an attack against nearly all virtual private network applications that forces them to send and receive some or all traffic outside of the encrypted tunnel designed to protect it from snooping or tampering.
TunnelVision, as the researchers have named their attack, largely negates the entire purpose and selling point of VPNs, which is to encapsulate incoming and outgoing Internet traffic in an encrypted tunnel and to cloak the user’s IP address. The researchers believe it affects all VPN applications when they’re connected to a hostile network and that there are no ways to prevent such attacks except when the user’s VPN runs on Linux or Android. They also said their attack technique may have been possible since 2002 and may already have been discovered and used in the wild since then.
[...]
The attack works by manipulating the DHCP server that allocates IP addresses to devices trying to connect to the local network. A setting known as option 121 allows the DHCP server to override default routing rules that send VPN traffic through a local IP address that initiates the encrypted tunnel. By using option 121 to route VPN traffic through the DHCP server, the attack diverts the data to the DHCP server itself.
Interesting attack on VPN services.
Thoughts? nostr:npub1f6ugxyxkknket3kkdgu4k0fu74vmshawermkj8d06sz6jts9t4kslazcka
It seems to me that any cellular network should be considered a hostile network.
Researchers have devised an attack against nearly all virtual private network applications that forces them to send and receive some or all traffic outside of the encrypted tunnel designed to protect it from snooping or tampering.
TunnelVision, as the researchers have named their attack, largely negates the entire purpose and selling point of VPNs, which is to encapsulate incoming and outgoing Internet traffic in an encrypted tunnel and to cloak the user’s IP address. The researchers believe it affects all VPN applications when they’re connected to a hostile network and that there are no ways to prevent such attacks except when the user’s VPN runs on Linux or Android. They also said their attack technique may have been possible since 2002 and may already have been discovered and used in the wild since then.
[...]
The attack works by manipulating the DHCP server that allocates IP addresses to devices trying to connect to the local network. A setting known as option 121 allows the DHCP server to override default routing rules that send VPN traffic through a local IP address that initiates the encrypted tunnel. By using option 121 to route VPN traffic through the DHCP server, the attack diverts the data to the DHCP server itself.
@chef
It’s that time. Time to get some exercise in, get off your arse and go for a walk. lift weights do some yoga whatever. help pass the time all welcome.
nostr:npub1yx6pjypd4r7qh2gysjhvjd9l2km6hnm4amdnjyjw3467fy05rf0qfp7kza nostr:npub15u3cqhx6vuj3rywg0ph5mfv009lxja6cyvqn2jagaydukq6zmjwqex05rq nostr:npub1jv3tmy30yrr0ek0fzdz5wfanh0pdp947fqgewyz44qndmg75ev9sz7lakg nostr:npub147wy3decmxy3vs9u4nse80ha7nkcydt7zdge8lc9gk8ddglh4t6qudjwdr nostr:npub12r0yjt8723ey2r035qtklhmdj90f0j6an7xnan8005jl7z5gw80qat9qrx
nostr:npub1x3n9jcp54npw2l6scvewdvy47jhvj30706u783nu2hktu6a8gc5q8f00qs nostr:note1ysyw5w8gqlfpyf8ww8eg6twqw8q926jncpn448xz9p8s7t53xzcsaxdd05
https://i.nostr.build/AalZL.webp nostr:note1e3j7frxkpxtkca37zl9e7lhzjjqalnklsp9as6u9ehyy7n78rdesf7jtfd
I hear that
Well mate. Over this rain tho. Just won’t let up. Been wet for weeks.
#austriches
This is a disgrace. nostr:note1y4e7r0xqumcaghh0sf6seqf5qpy8rypq6j2xr6f2jss8v49jk3fsjrzpev
You should put that up on zap.cooking a nostr client by nostr:npub15u3cqhx6vuj3rywg0ph5mfv009lxja6cyvqn2jagaydukq6zmjwqex05rq
Orange eyes gone. Sad
#proofofsteak 
Cool little birds 

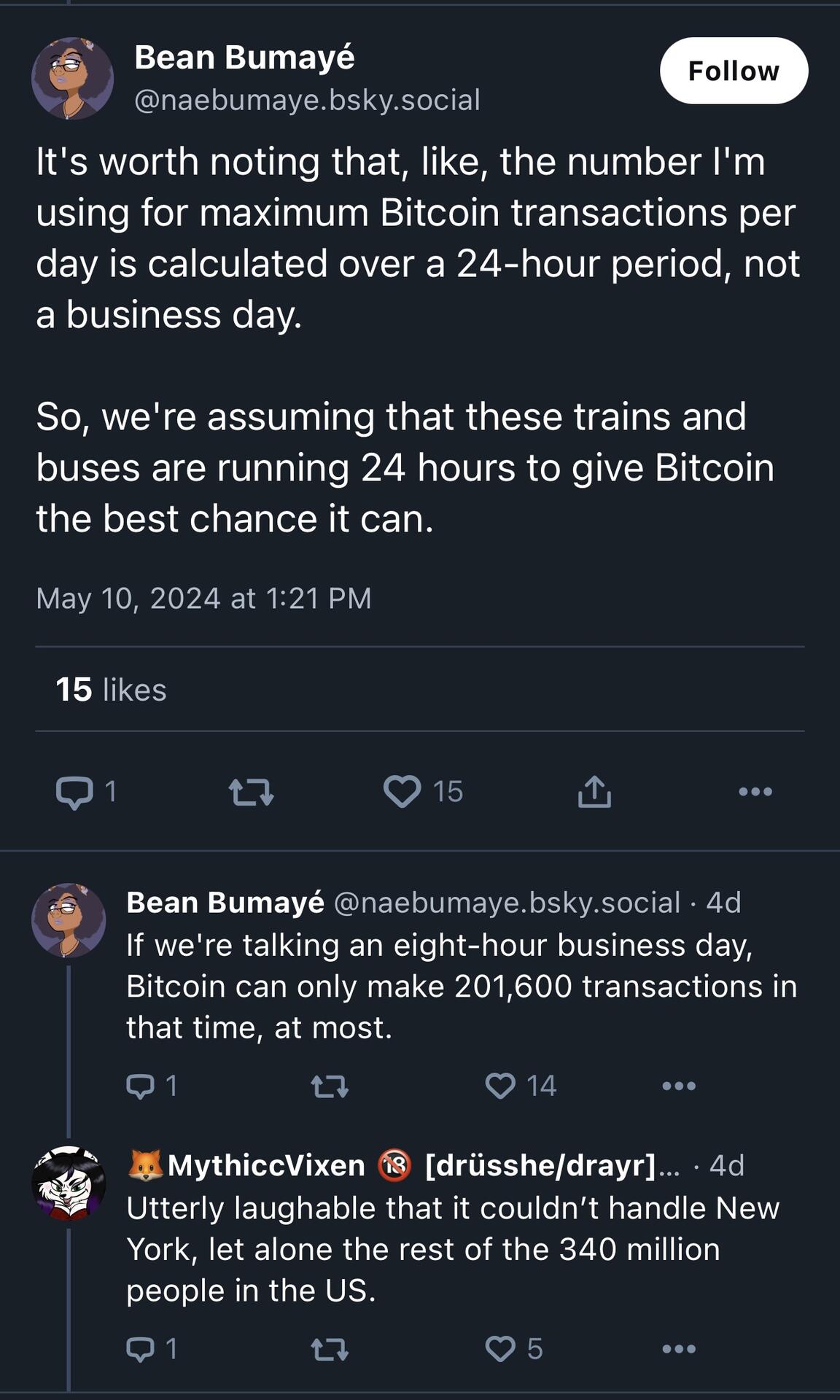
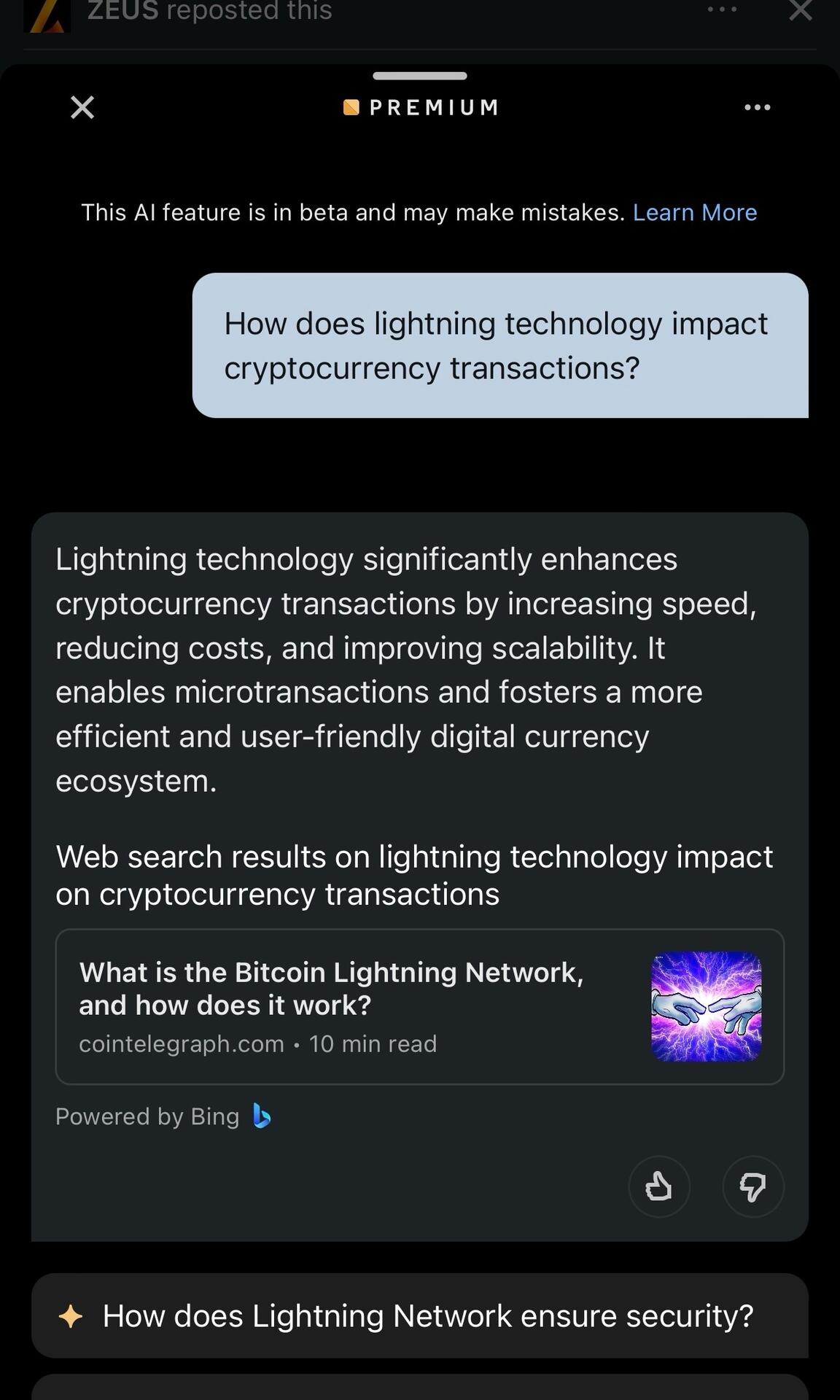


 nostr:note1pczarpenvs2upfrdnzeqajqyc54x2uhaj5953a9wmqangl75dupq7sxdyl
nostr:note1pczarpenvs2upfrdnzeqajqyc54x2uhaj5953a9wmqangl75dupq7sxdyl