LibreWolf.net
The core issue is this: Nobody has a financial incentive to expose the vendors selling protection service to block Tor/VPNs.
Unless more people:
1. use privacy services
2. actually report their experience when things go wrong, and
3. are willing to walk away if they're told to stop using Tor/a VPN
...this will continue to be the norm. It falls on you. Nobody else is doing the work, clearly.
Not sure if this was rhetorical, but if not...
They believe they're being protected from "attacks" because that's what the people selling the service tell them. They tyoically don't ask what attacks, but if they do they get super generic answers like "hacking", "DDoS" and the like. Since they haven't "been hacked" it seems like their vendors are being honest and accurate.
The thing they often don't realize is that these services don't block attacks, they block everyone using privacy software, good or bad.
They also don't realize how many sales they are losing. There's no metric for that, and most people will never report it because they've done so before and they were told to just use a different browser.
They also don't kniw how easy it is to bypass this "protection" they are buying. For example, today, it was literally clicking one button ("New identity"). If they realized this, they would instantly understand that an attacker will take the time to click that button, but a customer may not.
Just bought a couple hundred bucks worth of stuff over Tor. Had to get a new identity once near the end, but it otherwise worked fine.
I'm doing my part to show businesses and they should not block #Tor users from doing business with them.
Amazon already knows this, but I've been trying to buy direct from vendors rather than going through a marketplace.
The only way this could have been more #cyberpunk is if I could pay in #bitcoin instead of Mastercard. One step at a time, right?
#privacy
I saw a VW Rabbit in beautiful condition the other day. 👨🍳💋 Complete with the original mudflaps!



Note the size of the parking spot as compared to the size of the car. 😂
Matthew Green provides sober look at the #e2ee situation in the #UK with regards to #Apple's #iCloud.
I don't like Apple, but this seemed like a fair piece to me.
I have to wonder how Apple knows which users are in the UK. IP address? Time zone settings? Whatever address they typed into their iCloud profile?
It seems like some people may suddenly move out of the UK and suddenly start using a VPN all the time.
The majority of people in cybersecurity in the US are still on Signal. Matrix is growing fast though. I don't know anyone in the industry who uses SimpleX. That one seems even less well adopted than Briar.
Yes. Open source hardware and developer software.
They said the same thing about the UK two years ago. From what I read, the UK finally got around to passing that law, Apple rolled over without a fight, and it's radio silence from Signal. No indication they followed through AFAIK.
Maybe if enough people raise hell about it they'll take a stand. It worked for usernames (even if it did take nearly a decade and they still collect phone numbers, still, it's some progress).
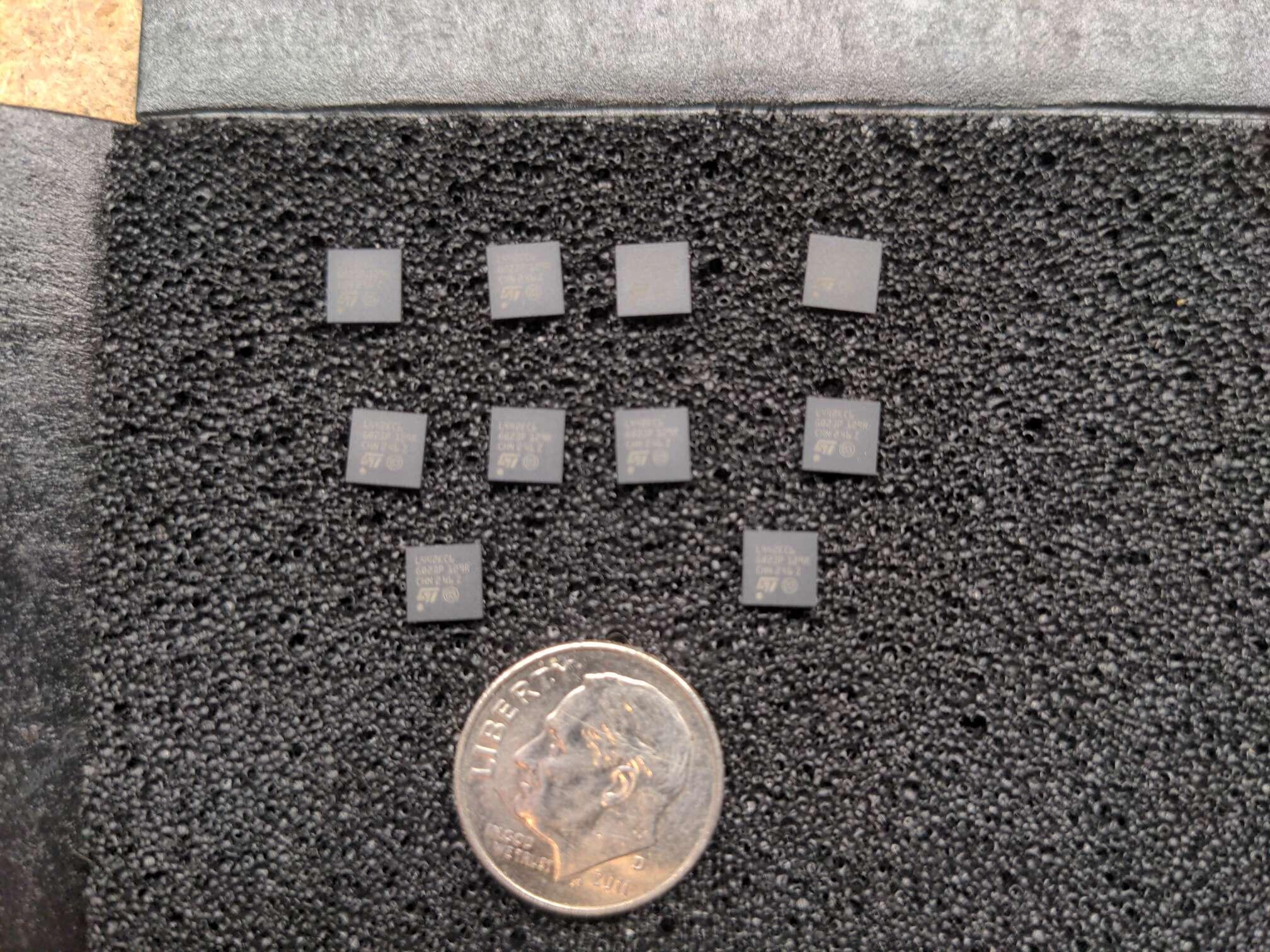
No, it's custom hardware. It has an entire tiny computer in there to keep all the secrets safe and secure. 😁 Here's what the board looks like

Here's a pic of the CPU on an unfinished board

And finally, a picture of the CPUs with a US dime for scale
I'm too much of a #hippie to even #recycle this case that has a blemish on it. It will now be the case for my personal #Signet so it doesn't go to #waste.

Fortunately, the next print came out just fine.
#3DPrinting #electronics #security #cybersecurity #privacy
A. Yes, and this is only a problem for open platforms
B. Even if there was not an economic incentive to be there, it may still be worth it to meet people where they are
I deleted my Twitter account a whole ago, and maybe there's a lot fewer people with freedom tech now as a result, but it was more important to me to stop letting someone else directly profit off of me than it was for me to spread the good word.
If I were actually trying to build a movement, I'd have brand accounts absolutely everywhere. Facebook, TikTok, Threads, YouTube... you name it. Without going to these places, you're largely preaching to the choir. Not very effective at spreading your message.
Told ya. As Mozilla shifts from Googles money, they will use you to make some.
How the mighty have fallen.
https://infosec.exchange/@mttaggart/114071999359445580
#Mozilla #Internet #Browser #Browsers #Technology #Privacy #ToS #TermsAndConditions #Terms
In stark contrast, the LibreWolf privacy policy is just 3 sentences. https://librewolf.net/privacy-policy/
I'm working on it, but I'm not yet confident in my ability to run a node and not lose all the money locked up in channels (and few people will accept a channel with less than 100K).
After I figure out, document and test my backup and restore process, that's when I will feel comfortable using it for real. Until then, even the 50K channel I have open feels like too much.
Bike to some place every day. Maybe the grocery store, or hardware store, dollar store... wherever. It's much more motivating when riding a bike actually gets you somewhere instead of just riding in place.
Tell Johnny we're all glad he's not dead. #IYKYK
Yeah, there are a lot of us on here.
My current focus is to get a couple stable solar nodes up and running so I have good coverage.
After that, I plan on having an MQTT bridged channel to provide service uptime for my local services: matrix, nextcloud, jitsi, etc. That will let me know when my router is down (normally I get those noticed via email, but if the router is down, I won't be seeing any of those emails until after the issue i'd fixed).
Probably distribute info about our local 2600 channel on #Meshtastic to anyone who shows up to 2600 meetings.
General texting replacement for local folks. Maybe a weather channel that gives the forecast. Hazardous weather warnings such as tornado watches/warnings. We have lots of fun ideas.
No, using TCP/443 will fake out the really basic filters. Anything that looks to see if the traffic looks like HTTPS will see through that in a heartbeat though.
There's iodine, which uses DNS queries to get data back and forth.
A few other try harder to disguise themselves, but if you look at the packet size and timing, they're still detectable too.
More context would help point you in a more specific direction.
