this is exactly the kind of disingenuous bullshit that makes you a bad actor.
do you honestly think this helps users make better decisions?
Monero user nostr:nprofile1qqs27aqdrx96hwx8hqks53ccav65hvlk47dfscumsh22tncnw89t4pgppemhxue69uhkummn9ekx7mp0qy2hwumn8ghj7un9d3shjtnyv9kh2uewd9hj7qghwaehxw309aex2mrp0yhxummnw3ezucnpdejz7q7z90p says monero has better receiver privacy than lightning. I issued him a challenge. Will he accept it? 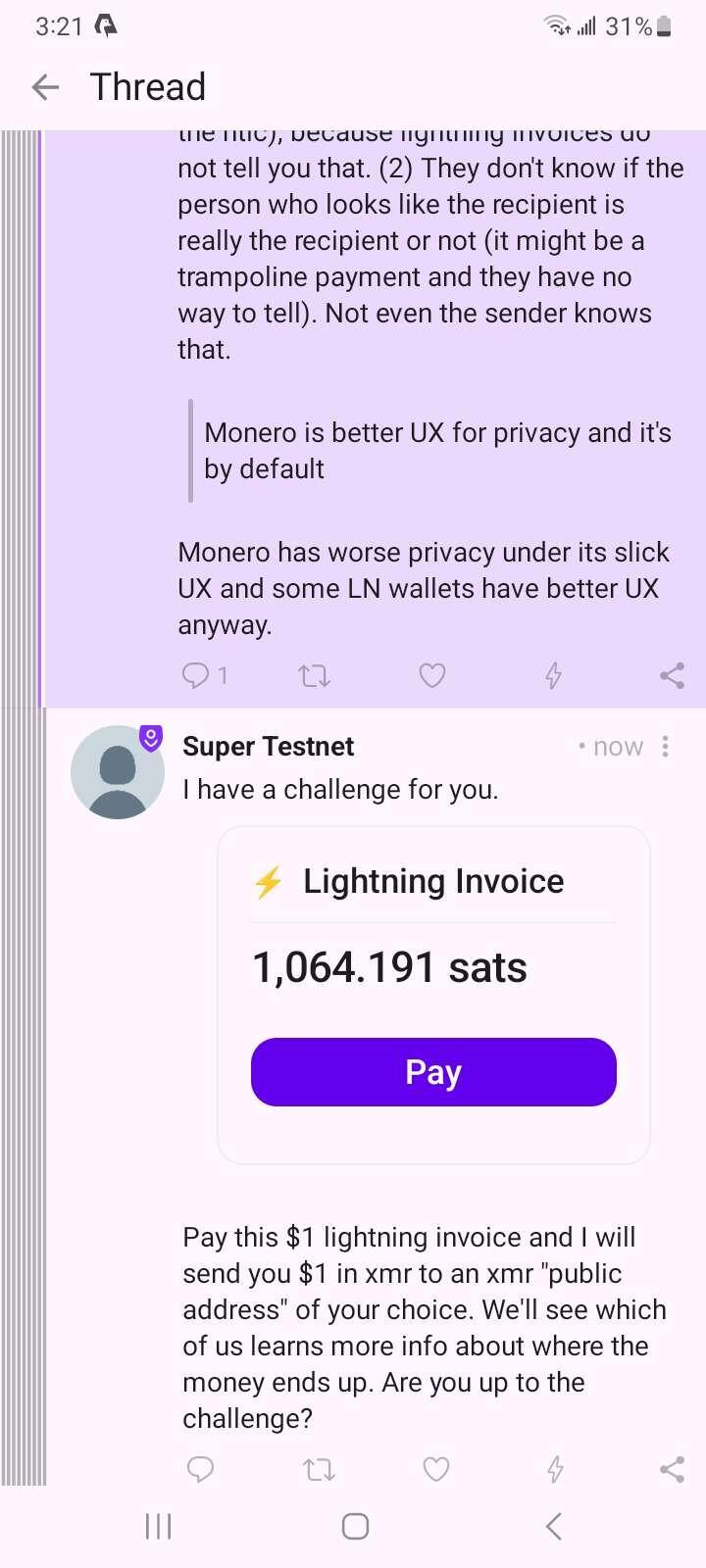
this is exactly the kind of disingenuous bullshit that makes you a bad actor.
do you honestly think this helps users make better decisions?
Not sure how this is bullshit.
This could be a practical demonstration for users to make informed txns.
its bullshit because *he sent the monero*
which is how he knows that information.
but he isn't saying it.
his "point" is
the *sender of a tx knows more about the *receiver on monero
than on LN
which is true
and irrelevant in most cases.
but he enjoys misrepresenting it to mean more than it does.
Is that not the exact use case you WANT privacy for? When I send a user funds.. at least a big part.
Yeah I get the whole overhead tracking the chain surveillance government bs,, but he didn't say that at all in these.
He never said he can track all monero txs and I didnt get that impression from the posts.
sending a monero tx isn't "tracing monero"
hes clearly saying he can trace monero
and knows uninformed retards like nostr:nevent1qqszt2rej65lgngj50cadfg8uzd7d744ehr052w4vmmhzul8hxyejvqpzamhxue69uhhyetvv9ujuurjd9kkzmpwdejhgtczypgdujfvle28y3gd7xspwm7ldkg4a97ttk0c60kvaa7jtlc23pcauqcyqqqqqqgfckvjv will pretend like it gospel
iow
disingenuous bullshit
I'll be the first to say 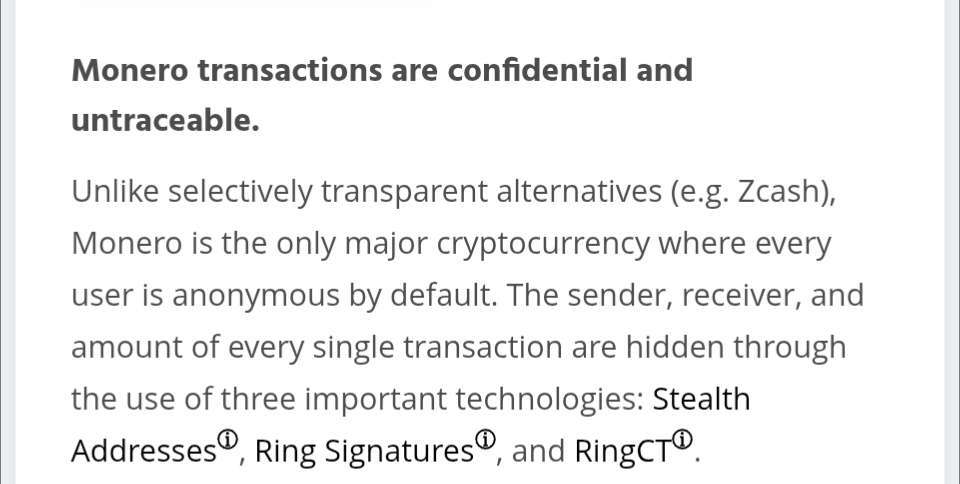
So as long as you aren't PART of the tx it's untraceable and the amount can't be known.
I'm splitting hairs here sure but this reads a certain way.
And this is coming from a guy who I think you'd agree we have had discussion in good faith so no gotchas here. Just trying to understand.
So in this test, the sender used a view key (part of moneros design) to see exactly where he sent the Monero, which he knew from the beginning, including the amount that he sent. This is natural for a layer one blockchain transaction. And to me, means the test is fairly disingenuous.
Also this fued is stupid in my opinion.
this is a correct opinion
we're good homie
I'm not saying his "challenge" doesnt show anything at all
I'm just saying STN is misrepresenting it.
in a way that is unhelpful to people.
and he gets the back of my hand.
I did what? I read and shared a thread that proved sending XMR is not as private as sending bitcoin over lightning in the eyes of the SENDER. Seems like you’re angry and big time mad about this outcome. And fuck you for calling me a retard you can suck my retarded dick.
> and irrelevant in most cases
It is highly relevant when you're being tracked by authorities. They typically start by sending you some money and then watching what happens to it next on the blockchain. E.g. that's what they did in this case where they traced a finnish man's monero: https://cointelegraph.com/news/finnish-authorities-traced-monero-vastaamo-hack
And in the Columbian case (where they ALSO traced a guy's monero) they also relied on the ability of the sender (in this case, Morphtoken) to point out exactly where he sent the money: https://cointelegraph.com/news/chainalysis-leak-monero-traceability
Lightning fixes this.
The simple fact is, on lightning, the sender can't trace his own payment, but on monero, he can, and this difference helps authorities arrest monero users.
nobody is denying targeted surveillance is possible.
stop acting like a fucking twat.
As Kanzan points out, monero has serious weaknesses against targeted surveillance
If *you* are worried about targeted surveillance, lightning offers better privacy than monero
yes
feel free to investigate if running a full LN stack yourself
is a better fit for your privacy model than just using #Monero.
Well, technically speaking, Monero isn't actually at fault in any of these stories.
Both of these stories start with exchanges telling the authorities what pubkey received their money. The fact that they *know* what pubkey received their money (and can prove it) is a design flaw in monero. Lightning fixes it.
Also, in both of these stories, after the money went from the exchange to the user's pubkey, the analysts watched the blockchain to see where the money moved next, and it went to another exchange with a probabilistic identifier marking the user's pubkey as a possible sender. This enabled them to contact that exchange and find out the user's identity, which led to an arrest in one case and better evidence for the charges in the other.
Lightning fixes this too, because not only does lightning not tell them what channel the money went into in the first place, but when it moves out of the channel, the analysts don't get to see that, because the transaction isn't broadcasted. So they never see the money go to an exchange and thus can never know to contact them to obtain the user's identity.
Targeted surveillance is possible even with Lightning as well; it's just that the attack vector would be different. And that's not Lightning's fault either, just like it wasn't Monero's fault in previous cases.
I like that I can point out how lightning fixes a privacy attack vector and the response is "ok but it doesn't fix ALL attack vectors -- there's probably some other one it's vulnerable to."
Yeah, probably. But even if other attack vectors exist, that's no reason not to fix this one. I think monero should fix it too, and I am glad FCMP is being worked on to hopefully do that.
I don't see any major issue here that urgently needs fixing — it feels more like a hassle that just requires some extra steps to get around.
Even the sun has spots. 😏
Aside from being a tool for your spy games involving heroin sales and the purchase of military secrets, Monero is also just a regular means of payment, and things like this theoretically make it easier to use. You can come up with several scenarios where this "vulnerability" automates problem-solving.