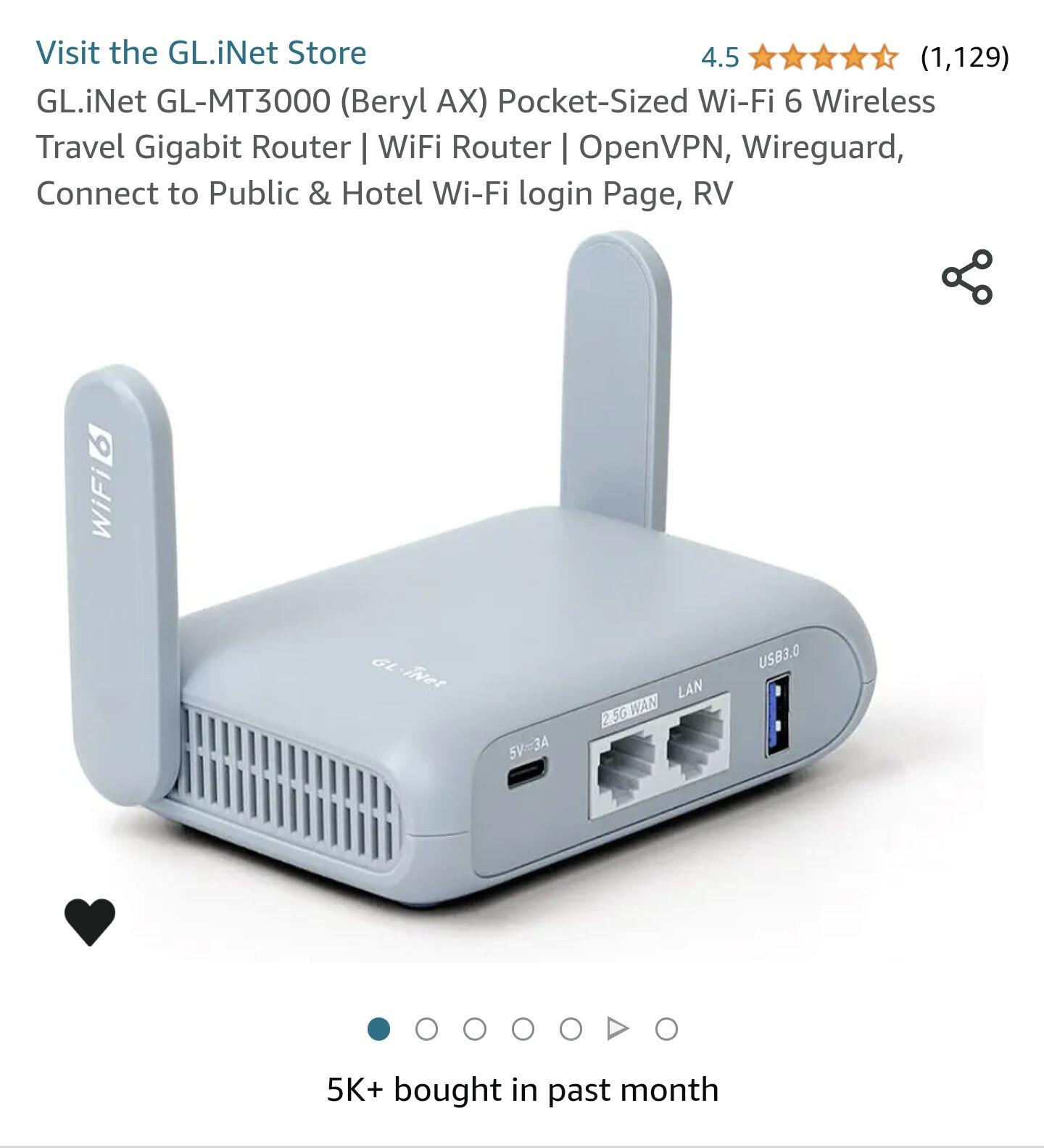
PrivacyTechPro tip:
Your router likely has proprietary software installed from a large company that has full access to your internet connection and can "call home" at any minute.
Use a hardware firewall and a VPN on your network.
Every IOT (Internet of Things) device you connect to your home network not only announces your IP address, but also expands your network attack surface to hackers.
I recommend #Protectli Vault Pro VP242 4x 2.5G as a hardware firewall for most client's home and small business networks.
#cybersecgirl #privacytechpro #network #security