A "quick" question may be quick to ask, yet doesn't mean it's quick to answer.
What's an all natural and effective way to reduce/eliminate a #tick population?
Whomever you brought if from should have included screws in the kit.
You could put them behind a small pfsense-capable router if the wifi network is public or semi-public.
But still anyone who is on that router's wifi would be able to access the Bitaxes.
You could probably use the firewall in the router to only open the Bitaxe ports to specific IP addresses.
You could also isolate the Bitaxes via the router by using Tailscale and only allow access to the Bitaxes to IPs on the same Tailnet.
The other benefit to using the pfsense firewall is the ability to use a VPN to mask the Bitaxe IP.
I've found the most important thing is to keep it cool enough. I had issues with this early on, however figuring out the proper placement made all the difference.
Parents are the worst part of youth sports
Why #archlinux over #ubuntu?
I used to rely on keybase to pass around docs among devices. I don't believe keybase has been maintained for some time now and the file transfer seems to have stopped working.
In comes #Syncthing, which I've used for various things over the years. I now have multiple devices syncing through an encrypted and self-hosted server and passing docs around works really well.
One thing I don't like to rely on are the shared Syncthing discovery servers, so I configured Syncthing to run without using them.
Also, the docs weren't quite clear on how to config encryption so all docs are stored encrypted on the central server, while being decrypted by the remote devices. I finally figured it out. While not intuitive it is quite easy to do now that I understand how to do it.
Would anyone be interested in me further documenting this use case?
#foss #opensource
Can you explain to me how web apps, e.g. wallets, secure data in encrypted enclaves within the browser. Recently I realized that I didn't understand this nearly as well as I should.
Here's how I did it -
1- download F-droid directly and install it
2 - use F-droid to install Aurora Store
It all works seamlessly.
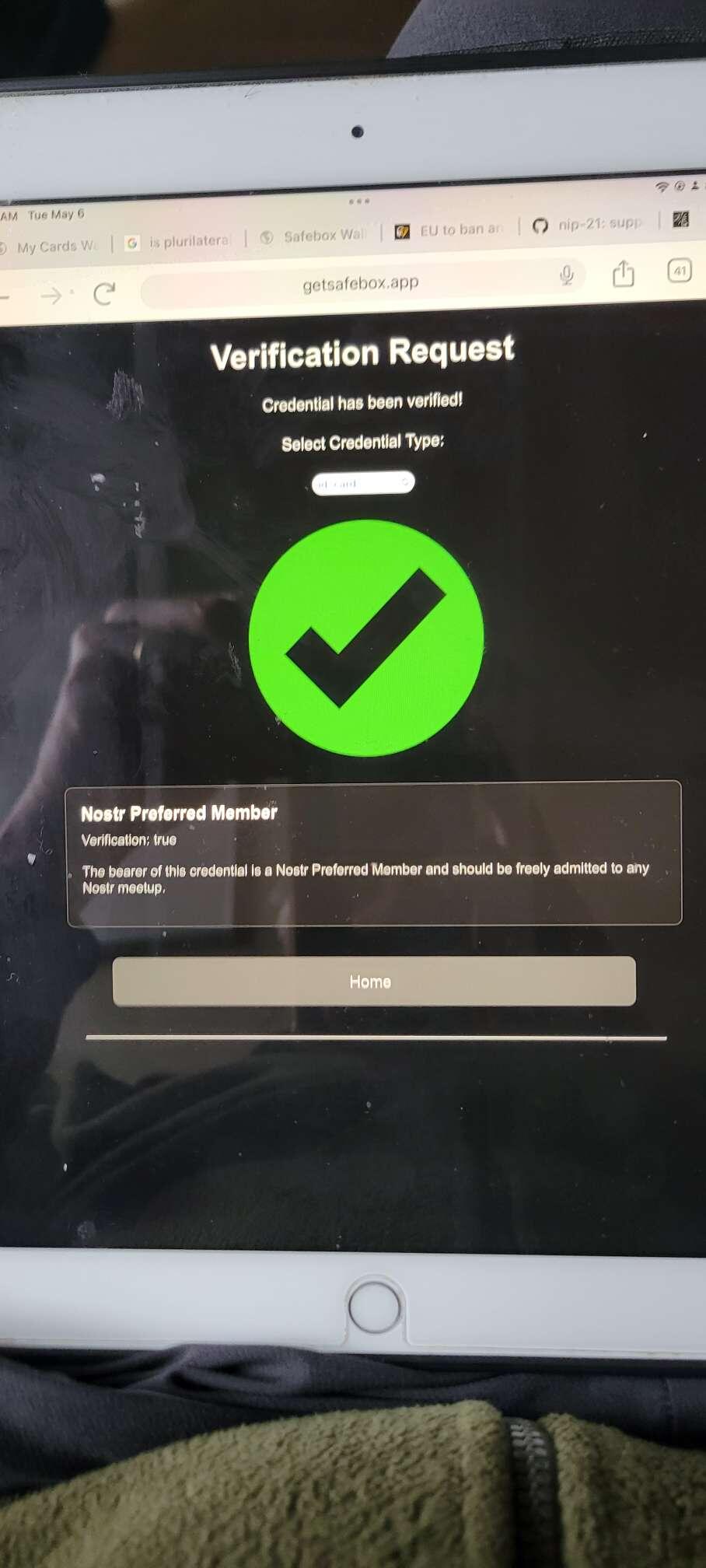
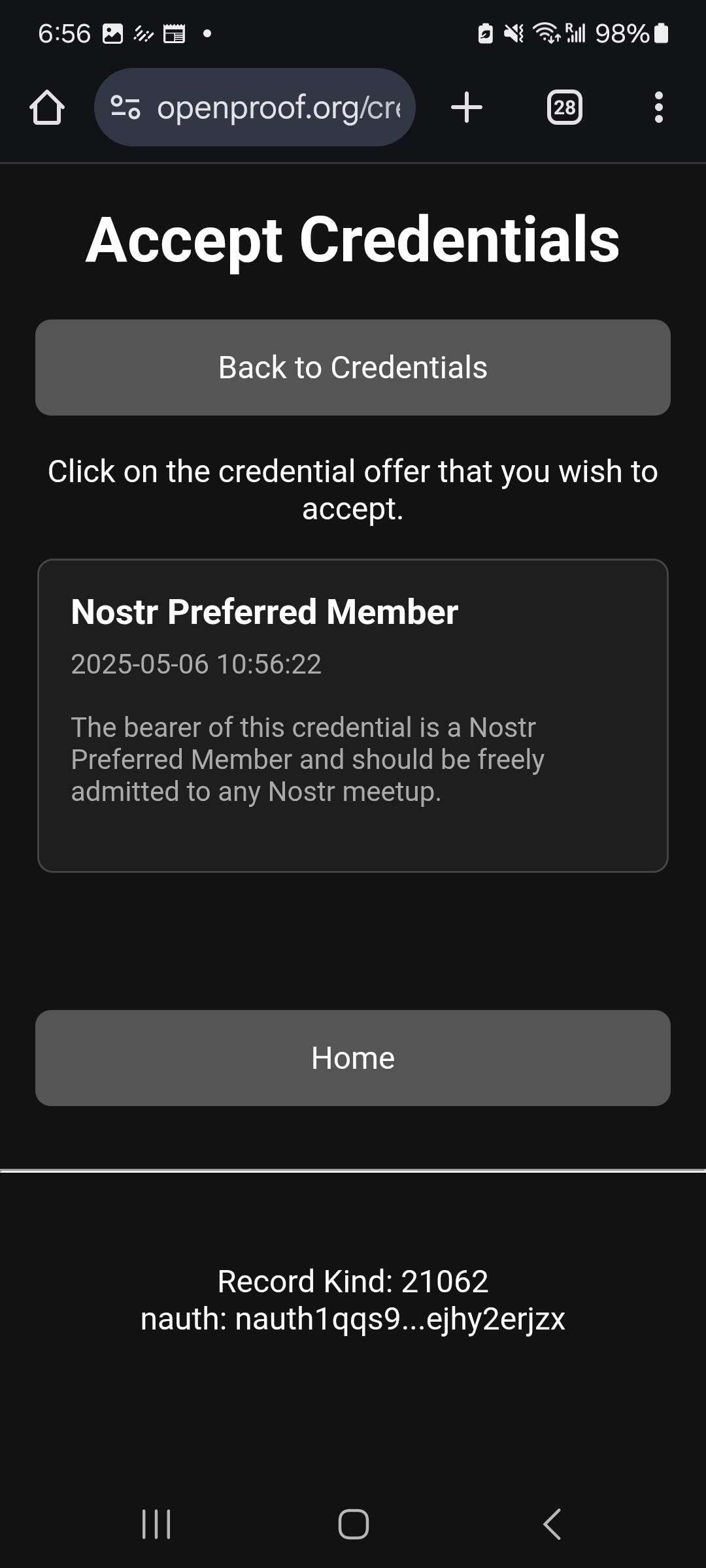
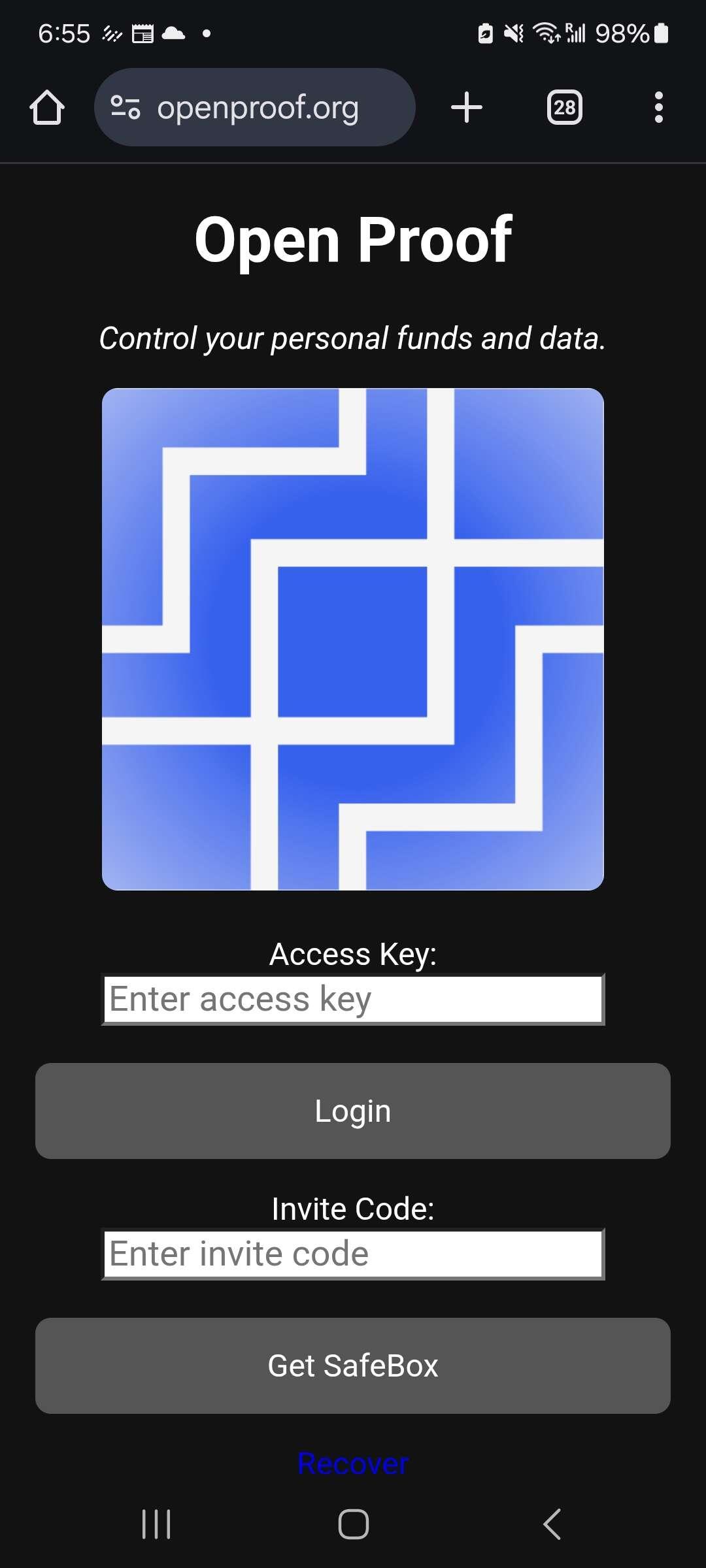
Yesterday, I fired up a completely separate instance of #nostr #safebox at https://openproof.org
Credential issuance, presentation and verification all worked seamlessly - as it was all one system. Better yet, zero https/rest/api calls between the two instances. Initial invocation was a visual channel (QR code) and the rest gift wrapped nostr events.
This is the future of inter-app coordination!
Is this similar to Hashicorp vault?
Have you measured the ph?
I've come to appreciate the importance of 7+ on the ph scale.
Otherwise most of what goes into the body comes right out 🌊
Ships frozen is unfortunately a non-starter for me.
Thanks, I forgot it was possible to download F-droid directly and install from the APK.
Glad you got it working and +1 on the above suggestion.
Do you have a firewall running anywhere that could be blocking ports?
Thanks, I'm also trying to figure out how to aquire the initial sats w/o buying them on an exchange, for example.



