nostr:npub1xdtducdnjerex88gkg2qk2atsdlqsyxqaag4h05jmcpyspqt30wscmntxy nostr:npub149p5act9a5qm9p47elp8w8h3wpwn2d7s2xecw2ygnrxqp4wgsklq9g722q
Thanks to you both for making this nostr-login proof of concept. Local nsec bunker storage is gonna be a game changer.
Trying to integrate your module into my onboarding client. I have a few issues you may consider:
- I’m not a fan of outright obliterating NIP07 login buttons. Especially while we’re all still testing and getting bunker infra set up… some people will still want to sign in via extension. So I won’t call ‘init’, but instead instantiate one of the included components.
- not really a fan of “branding” the login form (as separate from the hosting app). Y’all do deserve credit but this is just too noisy (a theme switcher on the modal …?) and smells like phishing.
- would like to see a “form only” component that I could use right on the signup page, without all that modal stuff.
- my only option then is to instantiate the modal component and try to restyle it. But it cannot be styled. Using svelte, I haven’t found a way to inject CSS overrides to make it “less modaly” …
- I feel like I’m being given a black box of canned functionality and “that’s all you get” … from an opensats funded project.
Init will not override nip07 extension, so if someone has it they will keep using it as usual.
Thread collapsed
This project has nothing to do with opensats.
Re your other points I agree that we should provide much more customization. Which design elements you would like to exclude? Header?
We could provide just functions that accept username and handle the rest, then you could implement your own forms as you wish. These isn't much login in them aside from checking nip05
Thanks.
I’m still a bit foggy on the how various nip46 implementations work. (I imaging a lot of nostr users and nostr devs still are…tbh… given the recent “awareness” that original nsecbunker has access to read nsecs) Given this, I’m trying to wrap my head around the code your developed with `noauth`, `noauthd`, and `nostr-login`…
In the end, what’s important to me as a client dev is:
- what are minimum tools I need to implement “local storage” nip46 signin and signup form for my users?
- how do i host a “local storage” nsec bunker at my client domain? (if my new signups are gonna get a nip05 name out of it… I’d rather it be from my onboarding client domain… with integrated key management tools right there … cause first client “should be able to be” the only client a new user needs.)
To implement nip46 sign in simplest thing is nostr-login or nostr-ignition. Couple lines of code and your app can be signed into.
If you want to give new users your own nip05 you don't have to run the full nsec.app service - I can fire onAuth event on sign up and you can run users through your own onboarding and give them your own nip05.
If you do want to host your own version of nsec.app I will have some instructions in readme soon.
These are awesome tools!
My only concern with running either (nostr-login or nostr-ignition) is the lack of customizability. Thanks for offering. Because nostr-login supports “local naec storage”, I’ll use this.
Yes please. I’d like to:
- add a “form only” component for nip46 signup (or signin) without the modal, modal header, or modal footer content.
- run users through my own onboarding, and give them my own nip05 without needing to host nsec.app myself. (Without breaking “oauth” style nip05 signin flow for my new users in other clients?)
P.S. I will prolly want to host nsec.app at my own domain in the future… or provide some affordance for new users to manage their keys from within the onboarding experience.
Thread collapsed
Nostr ignition seems to be functionally the same, both are a way to access keys using nip46. It's more customizable atm from what I read in their docs, although I am not sure how ready it is.
Thanks for your feedback I will get back to you when we have more customization options and onAuth event fired for you to run your own onboarding.
Thread collapsed
Thread collapsed
Thread collapsed
Thread collapsed
Thread collapsed
Thread collapsed




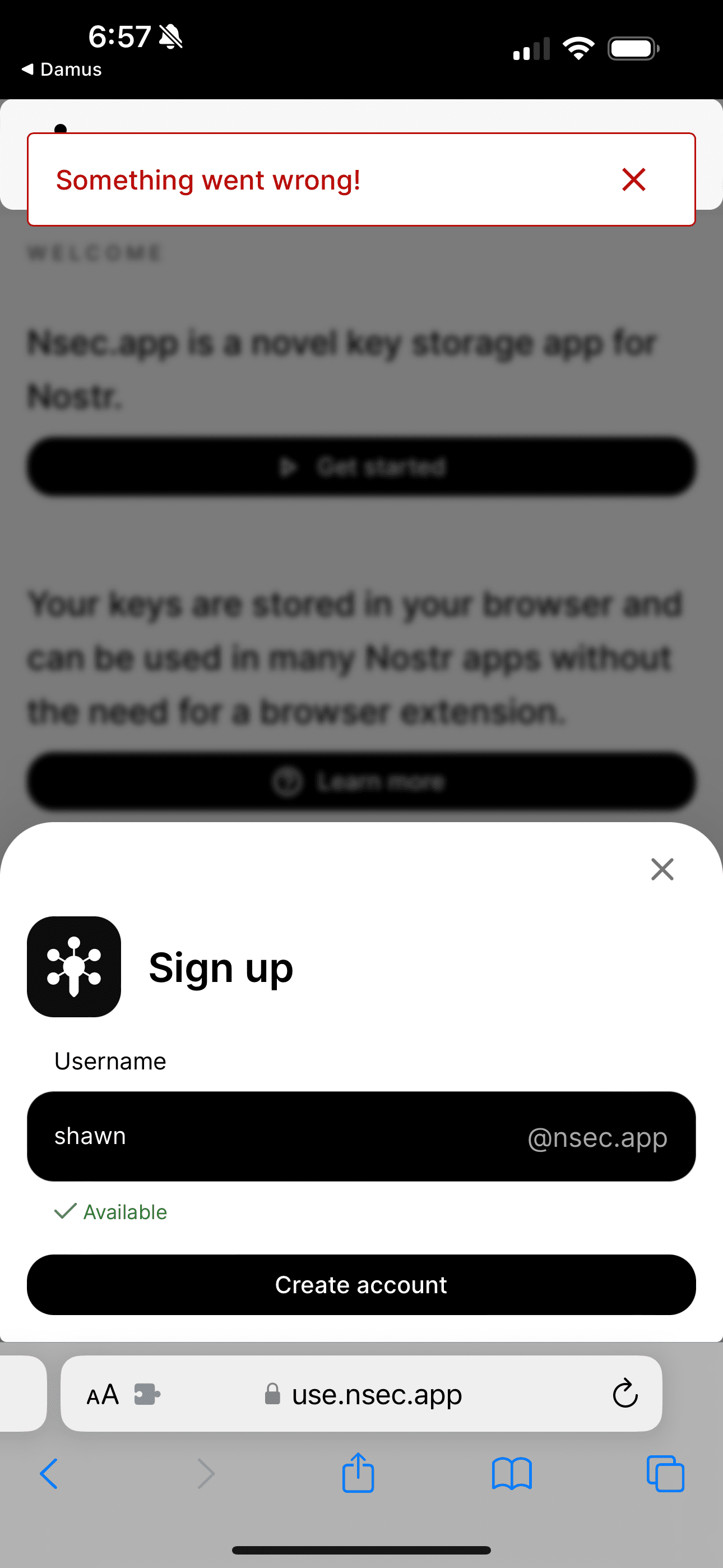



















 #m=image%2Fjpeg&dim=864x1920&blurhash=%5B184unxv9FWGsit7t8WC_0W9-%3AW900W9xtW98%5Et7D%25Rk%25Mt9xcWG00og-%3Ba%24%25MR%24-%3Aaw_1RhD%24W9&x=3d2e72462776d73311ce79f9b10a3ac563e9a356865133010d48743ffad95c6e
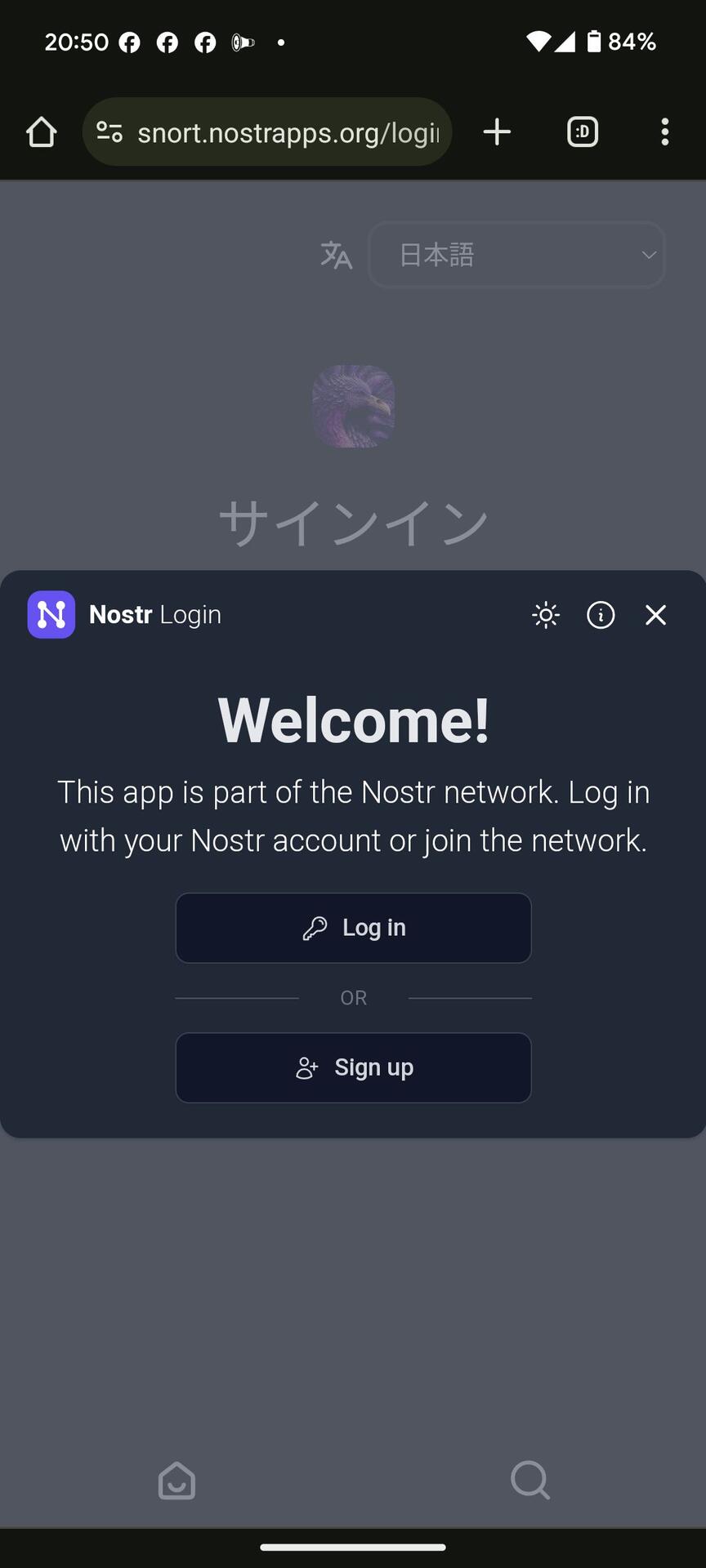
#m=image%2Fjpeg&dim=864x1920&blurhash=%5B184unxv9FWGsit7t8WC_0W9-%3AW900W9xtW98%5Et7D%25Rk%25Mt9xcWG00og-%3Ba%24%25MR%24-%3Aaw_1RhD%24W9&x=3d2e72462776d73311ce79f9b10a3ac563e9a356865133010d48743ffad95c6e #m=image%2Fjpeg&dim=864x1920&blurhash=%5BTKd%7DLRks%3Bay00WURjj%5B%25Mt7ofay%7EqRjWBWB00t7t6ofIUWBayfQIUj%5Dj%5BWBIUt7ofj%5B00WBayfQ&x=97caa05b00ba7a8e649179892a49e2531cec27f4ec934f26428f1839eca8c909
#m=image%2Fjpeg&dim=864x1920&blurhash=%5BTKd%7DLRks%3Bay00WURjj%5B%25Mt7ofay%7EqRjWBWB00t7t6ofIUWBayfQIUj%5Dj%5BWBIUt7ofj%5B00WBayfQ&x=97caa05b00ba7a8e649179892a49e2531cec27f4ec934f26428f1839eca8c909





