Sounds like Gentoo users mindset
Today someone asked me if Signet used Argon as the hashing algorithm. I knew it was a good algorithm when I looked, but I wasn't 100% sure. So I dug up a code reference.
Benny, if you see this, no, it uses scrypt.
https://gitlab.hax0rbana.org/signet/signet-client/-/blob/trunk/client/signetapplication.cpp#L235
For any non-crypto people, the punchline is this: "scrypt is maximally hard against brute force attacks"
What is your rationale behind usage of scrypt instead of argon2? Is it performance issues?
I didn't meant to offend you, it seems I incorrectly assumed that it is the task for your students to try to breach the school network.
As for Metasploit alternative and "Kali/ParrotOS + nmap being a no-brainer" - I think you are messing different stages of an attack as per cyberkill chain framework. There are a lot of scripts and tooling available and they are developed to solve some specific task well.
Metasploit is mostly used for a weaponization and exploitation stages. And personally I see nothing wrong with using it to demostrate a basic attack.
I don't think there are good open-source drop-in replacements for it, but I consider demonstration of a specific vulnerability exploitation manually is a good option, but I am not sure if your goal is to cover some technical aspects of red team or something else.
I would recommend against such amateur penetration test. It is not a good idea from legal point of view and might have an impact on network because when used improperly, "hacking tooling" can be accidentally used to conduct Denial of Service.
nostr is not only a social media like twitter, it is pretty powerful technical stack referred to as "protocol". The essential thing I personally like - your account (identity) is not bound to some one central server (instance of mastodon or twitter itself) - there are "relays" run by different people/organizations, and can be easily run by you as well. It makes nostr pretty nice thing when it comes to censorship resistance, as there is no single point of failure (and there is no "nostr CEO")
It's the international bitcoin cold war I'm looking forward to. Along with all the other boxes checked off to boot.
blob:https://coracle.social/f07e8a36-a078-40d6-b242-b378044178e9
blob: link is not working
https://video.nostr.build/1464e62c2373624b10182b847cf1f0ae0ec5a6d535a395e7ed583ba2a3d492c8.mp4
Not more relevant, however, they fixed this :(
This is why services like simplelogin or own domain with a catch-all/unique per-website aliases is a way to go.
Followed and zapped
They know about Nostr?!
Aren't longer addresses consuming more space as well? Or do you mean that sends are significantly larger?
Stay humble and read man
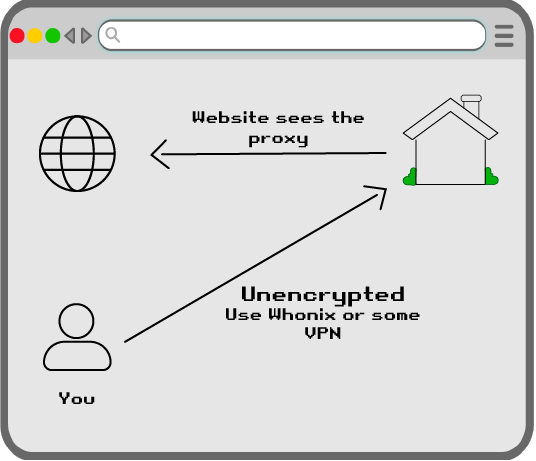
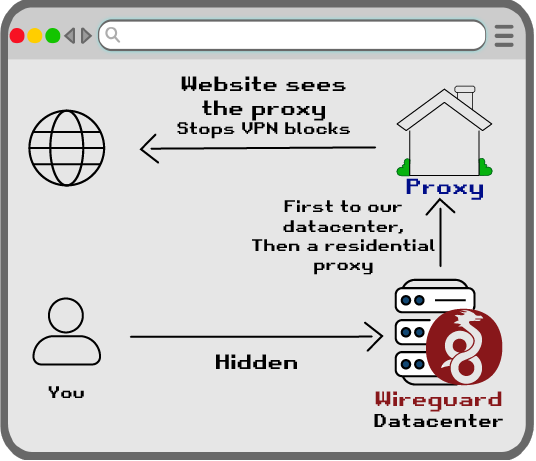
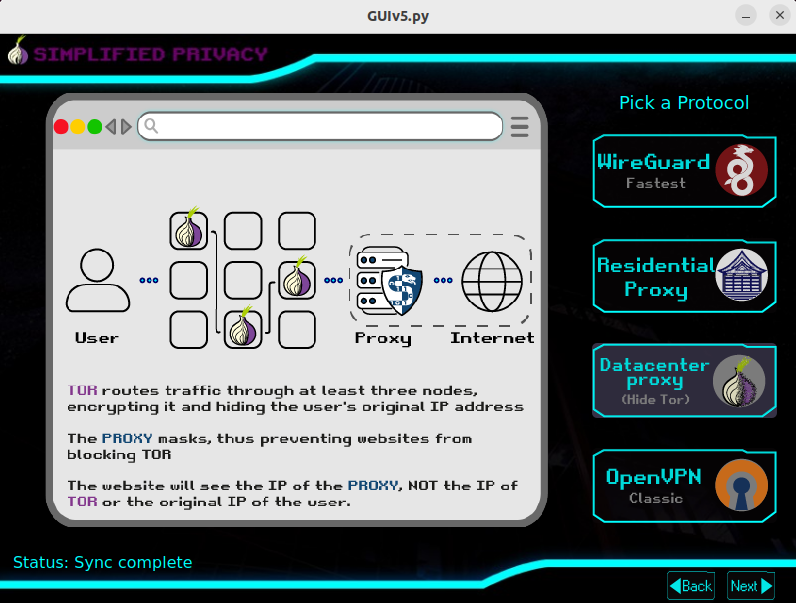
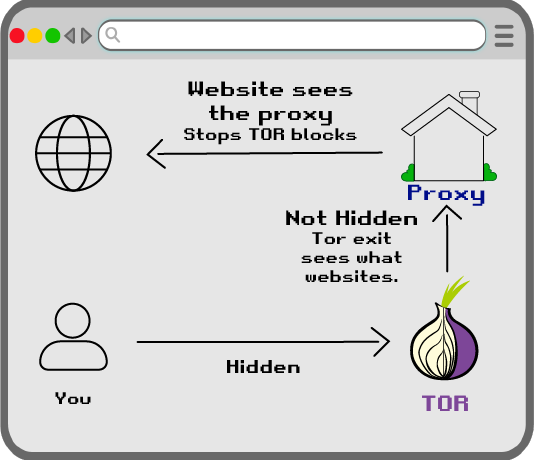
I think that another significant difference between Wireguard (and almost any other VPN solution) from SOCKS5 proxy is that with VPN, website might detect MTU of your connection, which will indicate VPN usage, while with SOCKS5 it will be the default value of 1500 (unless SOCKS5 server uses any sort of tunnel themselves). This makes it harder for a website to detect proxy.
Given this, might be a good idea to use Wireguard+SOCKS5, where SOCKS5 is only accessible over Wireguard, making it basically an encrypted proxy, combining benefits of VPN and proxy.
What client are you using? I am having similar issues with #Amethyst, no issues when zapping using #gossip
Those nasty gamers should stop!
If privacy is your goal, I would prefer signal over email. Email has too much metadata leaks.
If your goal is conversation confidentiality, PGP is sufficient. However, Signal has better UX, IMO.
Finally, cheap sats incoming
It might be due to changes I have made to "My relays" were not applied before application was restarted. Current (known to work) relay configuration looks like following:

The only significant change I have made that I remember is that I previously had "Read" disabled for DM relays.
Today I have opened gossip again, and Private chats loaded immediately, including previous ones. At this point I am unsure what exactly was broken and how can I help you to reproduce this issue, sorry.
nostr:nprofile1qqs83nn04fezvsu89p8xg7axjwye2u67errat3dx2um725fs7qnrqlgpr9mhxue69uhhyetvv9ujuur0wd6x2u3wwpkxzcm99u0at9yj almost made fdroid obsolete for my needs. Two nextcloud apps left and already asked for them to be added to Zapstore. Disabled the f-droid app for now
Can you briefly list advatnages and disadvantages of zapstore comparing to f-droid please?