How BCH Will Make Monero Obsolete - The Bitcoin Cash Podcast
https://odysee.com/@CashDragon:6/BCH-will-obsolete-XMR:a
#news #crypto #bitcoin #bch #bitcoincash #monero #xmr #privacy #technology #blockchain
The timeframe he gave "a year or so" is around the same time FCMP is going to be implemented on Monero. Maybe even by the end of the year.
Doesn't seem likely that darknet and privacy-centric markets move to BCH when they can continue using Monero for the same thing. Maybe they'll add it as an option? But for example Shielded Zcash (essentially what BCH will offer), Litecoin MWEB, and Lightning have been available for awhile. Why havent they been adopted in these places? We already have many examples that optional privacy = low usage of that privacy on all these things.
BCH is still missing other privacy components like Dandelion for node level privacy. It also doesn't have the battle-tested history, ethos, and constant improvement of Monero in these environments. He seems to be clueless when he smugly says "fine, use Monero if youre drug running..." uhhhh that's where your actual privacy is going to be put to the test and have it's kinks worked out. In adversarial environments. If it works for them it's going to work for your average user.
Not hating. I'm not opposed to using ZK on BCH. They should still do it for their users, but it just seems unlikely to overcome existing network effect of Monero for all those reasons.
Is gold Keynesian? The Austrians who Bitcoiners generally love seemed to think it was great despite it's ongoing small amount of inflation.
You're esentially saying when you pay someone you "traced" it to the person you paid (no shit, what a revelation).
No, read the actual thread. He came up with a challenge separate from our original discussion. I never denied anything in his challenge about Lightning and Monero. It says right there in your screenshots.
Second, on the transaction level with Lightning, you're relying on third parties not colluding to maintain your privacy. Nodes on Lightning can see amounts going through them. Nodes on Monero can't see amounts even when using someone elses node and even if they colluded. Lightning nodes in a transaction are directly linked and know the hop before and after. Monero stealth addresses are unlinkable to other addresses. Technically, if Lightning nodes on your path collude they'll know with 100% accuracy both the amount and public node it went to.
The privacy he's describing gets even worse in the real world since most LN users are on non-private custodial wallets and LSPs (Compare custodial LN wallet downloads and the largest LSPs). Centralized honeypots of information that can see most of the network and directly reduces your privacy even if you're using it LN correctly.
I checked the Core Lightning github and multipath payments are "on" by default there too. See, for example, this issue: https://github.com/ElementsProject/lightning/issues/3926
It involved an error report where a user encountered this entry too many times in their error logs:
"Detected large payment, splitting into 100 sub-payments"
I checked the Eclair github too and multipath payments are "on" by default whenever trampoline routing is used (which is the case in Phoenix, which always uses Acinq as a trampoline node)
Thanks for the info. Appreciate you bringing the receipts.
I mostly use Zeus now when I use Lightning (which isnt very often), and Atomic Multi Path is optional on it. I just realized I was confusing AMP with MPP. They do similar things but seems like AMP is an improvement over MPP. I haven't checked other LN wallets in quite awhile. Good to be proven wrong and see MPP is on by default more than I previously thought 🔥
I can't know how much money I sent to someone on the Lightning Network?...
Maybe I can learn from you. You sound smart. 🤪
Worked well enough for gold for thousands of years 🤷♂️
There are plenty of debates and discussions going on all the time, but you are just oblivious to them because you arent involved with Monero (obviously)
Bitcoin Core isn't a centralized team of developers? They're 98% of node software.
If a node guessed it was the full amount passing thru it would be right most of the time. If many transactions are passing through large hubs (because they are well connected and require less hops to the destination = more likely to succeed and cheaper) an adversary could collect quite a lot of info on the network. But sure it existing gives some plausible deniability. If it was made default that would be even better.
>"Monero also requires trusting that the other 14 keys are not held by the same entity or cooperate to deanon you."
You mean 15 decoys? That only applies to senders and every spend exponentially decreases the likelihood of being denon'd. Also, you don't have to trust others not being the same entity/colluding for reciever or amount privacy on Monero (both technically possible with LN if the nodes on your routes are colluding, but very unlikely)
>"This is true for any privacy system and impossible to avoid."
It's not true. Cryptographic accumulators are not really affected by the problem you describe because you're proving you're one of the global set of all transactions instead of a tiny subset - which is what will FCMP be.
I've been around many different Monero communities/forums/groups for years and I've never heard Coinomi before. Not sure who recommended it to you but that is not the norm at all. It's usually Cake, Monerujo, Feather, or the GUI/CLI.
Yes, scanning can be annoying, but that is what guarantees no one but you can see your transactions (any proper LN privacy wallet, like Zeus, also requires scanning). If you use it somewhat often it's not really a big deal. Wallets with periodic background scanning make this a non-problem. You are always caught up (or very close). You should check it out on Cakes new update. It's very new so I'm sure in time more wallets will adopt it.
The only Monero wallet left that holds users viewkeys to eliminate sync time, at the cost of some privacy, is Exodus I believe. There used to be another one MyMonero but it's been defunct for quite a long time.
Block filters only help privacy when querying, not when broadcasting a transaction.
Not sure what you meant by the last part. Generally more people using something means a larger anonymity set.
I've grown to appreciate Lightning more, but there are a lot of nuances to both. We could talk about them forever.
"not in working order" is exaggerated. Sender privacy is not in the most ideal state possible.
Amount and receiver unaffected.
It's still better than 99.9% of cryptocurrencies.
You don't even need a spam attack to deanon Bitcoin. That comes built in by default.
> He's wrong about unencrypted receiver (or meant something else)
I meant what I said: monero does not encrypt the receiver. If it did, monero devs could tell me what encryption standard they use (in lightning, we use the Sphinx encryption standard specified in bolt4) and they could point me to the code where the recipient's key gets encrypted (in lightning, that code is here: https://github.com/lightningnetwork/lnd/blob/b068d79dfbd2f583d890fd605953d0d4fb897a27/htlcswitch/hop/iterator.go#L114)
Monero does not encrypt the recipient's public key -- it gets published in plaintext on the blockchain -- so the protocol does not specify any encryption standard for that and there is nothing in the codebase where it gets encrypted.
Maybe technically it's more like hashing? Regardless, the practical effect is the same since it's a string of indecipherable and seemingly random characters that are seen once and never again. Third parties can't link a stealth address to a public address off-chain or to any other stealth address.
nostr:note1pg4lep6yf65599m78rpgf4e7x75pkpgr2wv6akzjdvzl97ncljeqgd35uv
Rings won't expand because they won't exist. They're being replaced with cryptographic accumulators. And you can't deanon those with spam.
But I'm guessing you'll have an issue that it addressed your criticism with a hardfork. Damned if we do or don't.
Super Testnet offered a challenge for things I never claimed about Lightning, nor denied about Monero.
Yes.
If you want to get a bit more detailed...
From the perspective of a third party observing the blockchain:
-Amounts are perfectly hidden (zero knowledge), but mining fees are not
-Address/receiver could be any Monero user in existence (since it is a unique one-time address that is seen once and then never again - effectively zero knowledge)
-Spenders use ring signatures to automatically "mix" your transaction with 15 decoys (but they're real transactions that happened on chain). Compared to the previous two it's the "weakest" part of Moneros privacy currently.
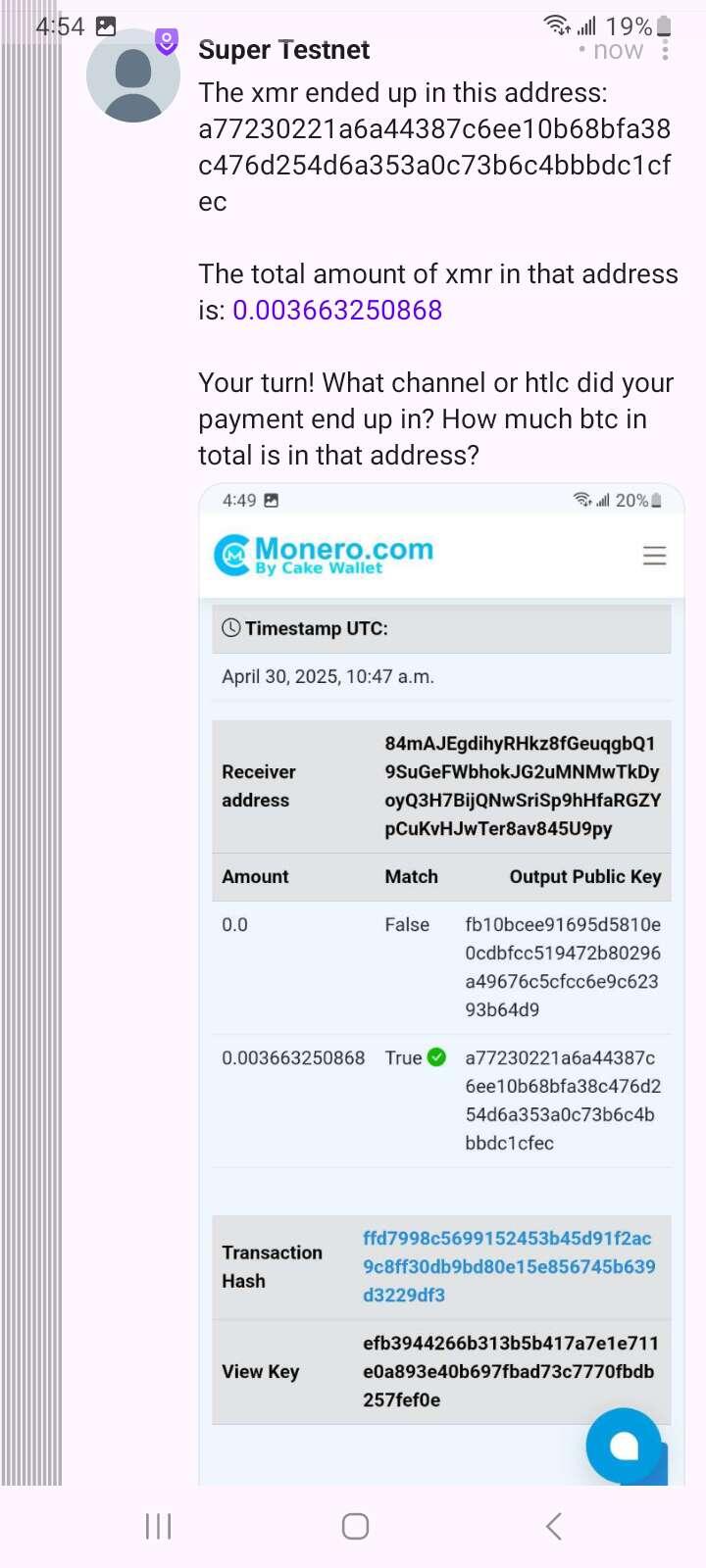
>"I can tell you that: it's the address I identified. That was the final destination."
You sure it's final? So is it still there?
How are you sure the address on my profile is mine either? Maybe I just put someone elses up there for fun.
> How did he do that?!?
I was able to do it because of a flaw in monero: by design, the sender knows what address he sends his money into and can report that info to authorities with cryptographic proof. This has led to multiple legal charges against monero users, see the attached thread for more info.
Lightning, of course, fixes this. nostr:nevent1qqs9t6glu9k3ps7ct6ad8a3cj9jfntxvlhayh8e3cc56rf4ghdpcjnsppamhxue69uhkummnw3ezumt0d5qs6amnwvaz7tmwdaejumr0dspzqgvra9r4sjqapufyl0vnc4kv4fz70e29em4c655y37vz206f0wt45p7m94
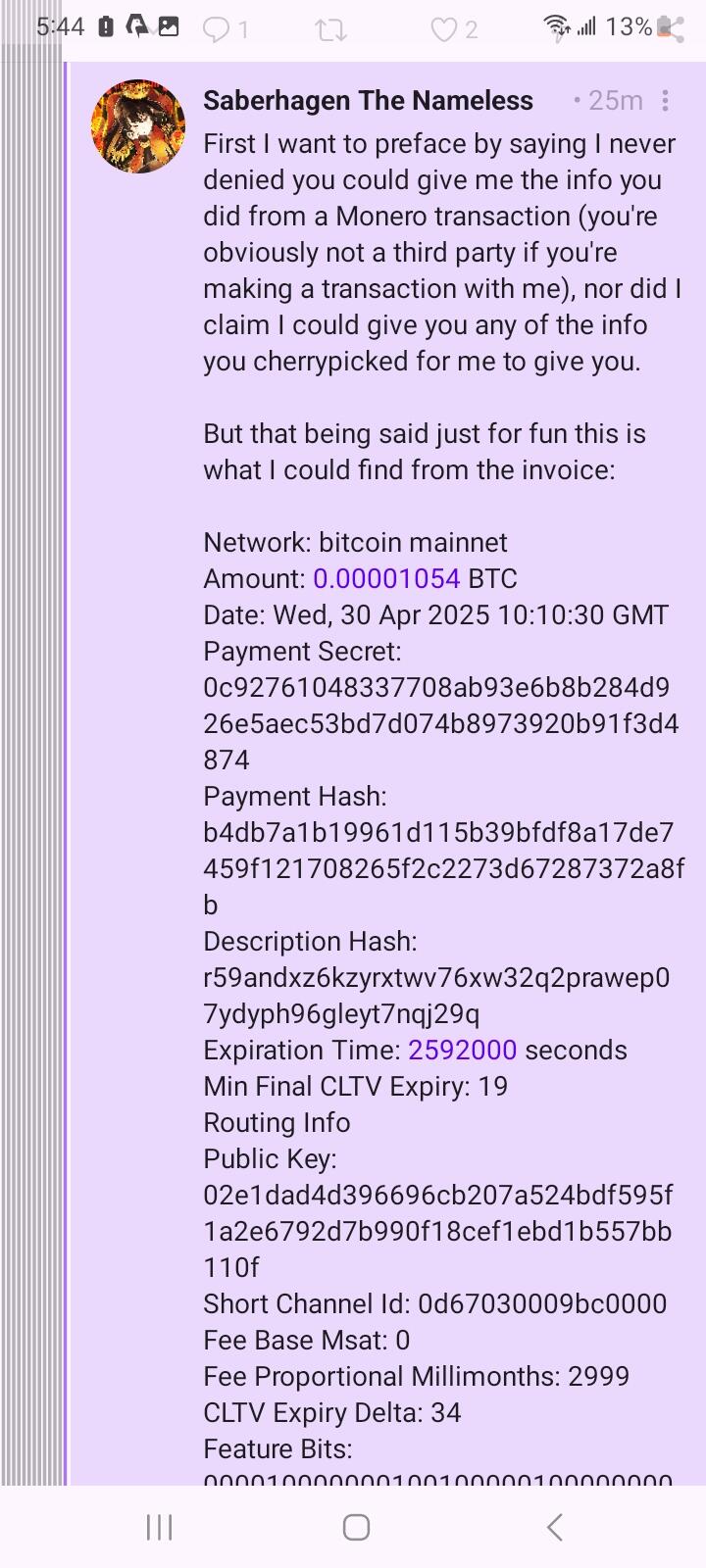
You can't tell me the total balance in my wallet or the final destination either (same challenge you gave me for your Lightning invoice)
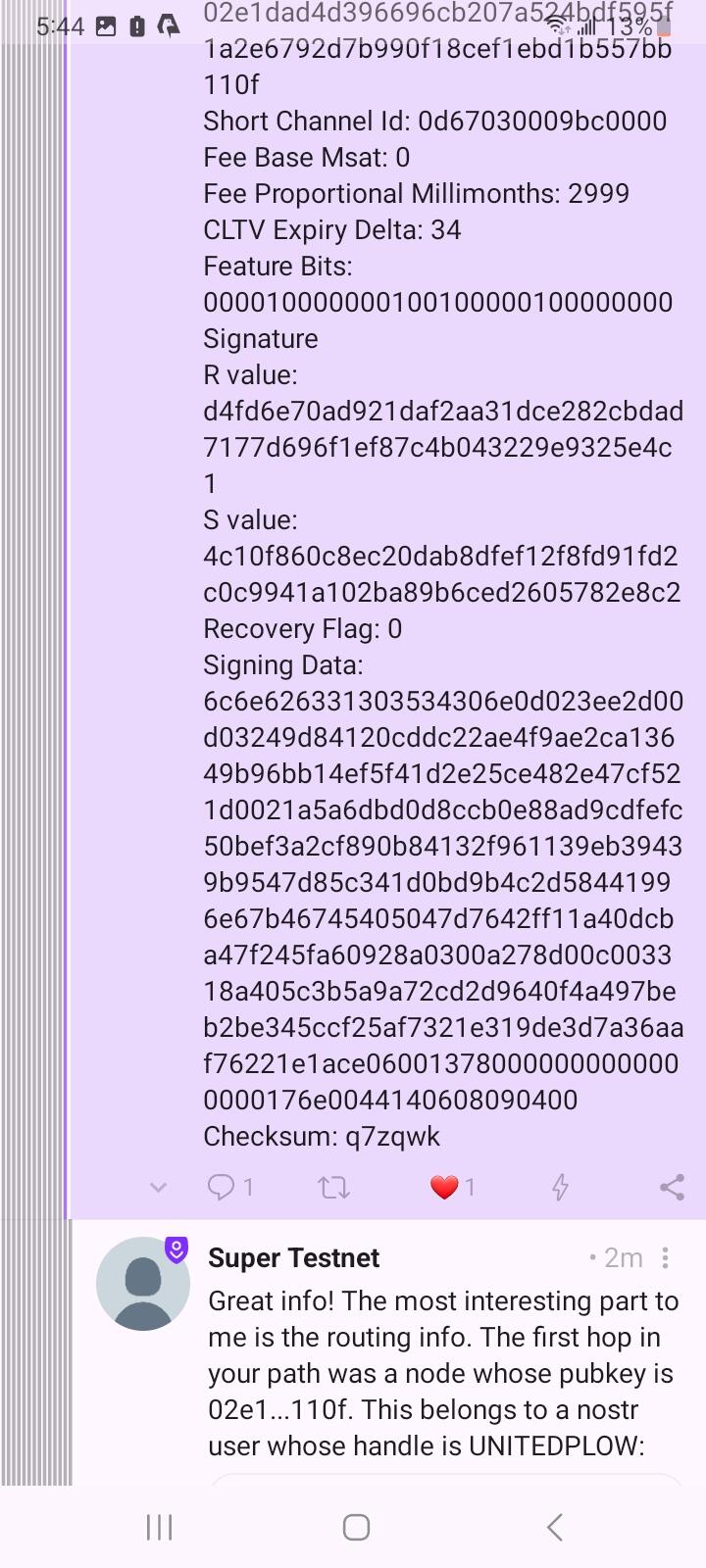
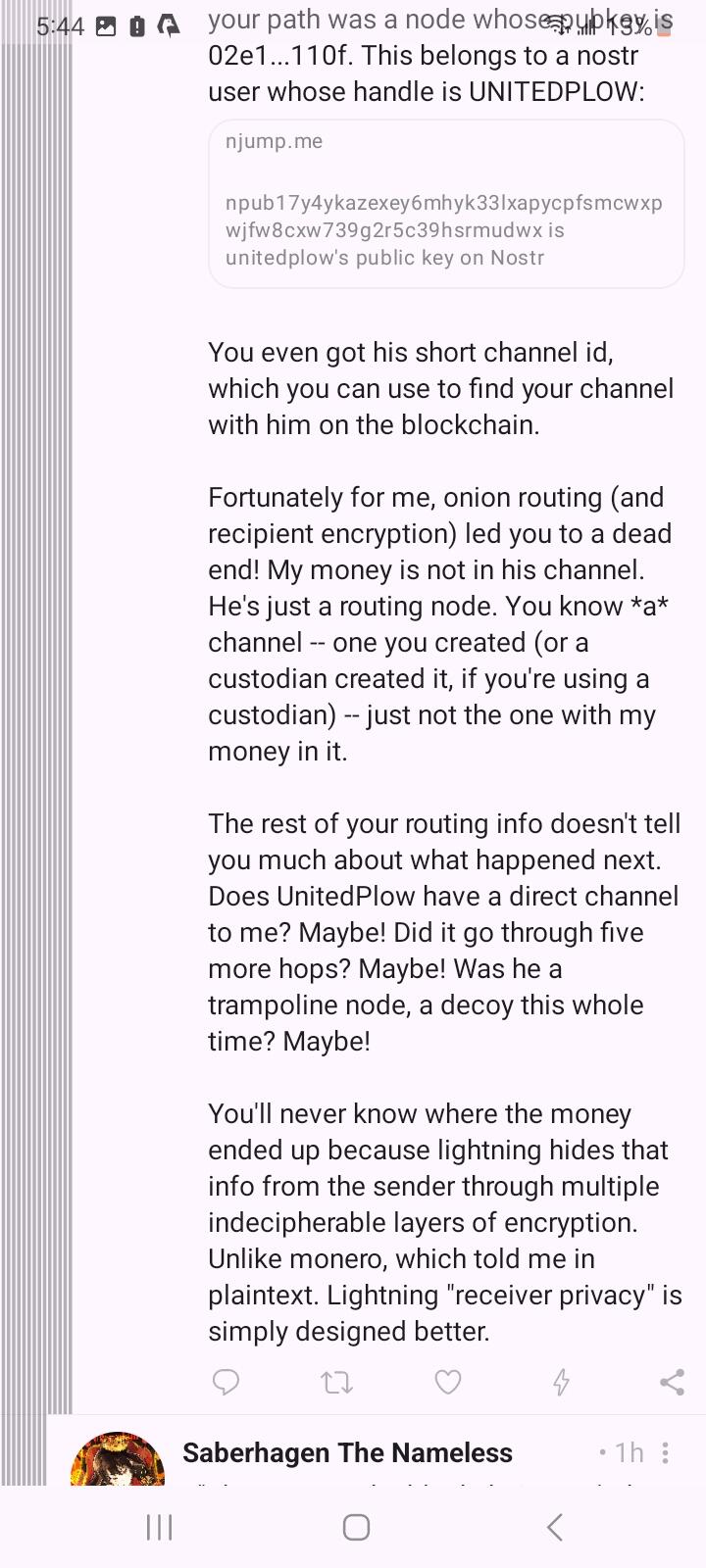
I know at least the public key of the first hop involved (potentially final destination) and can report that info to the authorities in the same way along with the invoice and preimage for cryptographic proof that I paid 🤷♂️
nostr:note1pg4lep6yf65599m78rpgf4e7x75pkpgr2wv6akzjdvzl97ncljeqgd35uv
Wow! He figured out the amount he sent me AND the stealth address he created!
How did he do that?!? 😂😱