I always keep my zap sats and my real chunks separate. buy on robosats, send to the primal integrated wallet. (but really setting up your own node isn't THAT crazy.)
pubkeys are your account not your username/alias. re-sign in to your mobile app with your Nsec if you want to write notes on the mobile app or use the web client on your mobile device but make sure your extention's stored Nsec is the same as your desktop client/Extention.
With IPv6 being assigned by your ISP it can change your server's IPv6 address making your website disappear over night because the ISP decided to rotate addresses. Very bothersome. Also, I am fairly certain there is no current protocol for attaching aliases to IPv6 addresses. So unless you post your server's IPv6 address to your site clients they would have to bookmark a 32 digit address and somehow make sure they don't get phished by a single misplaced digit.
Inside a printer ink cartridge
📹 FStoppers
https://t.co/0ibrwNrMHM https://video.twimg.com/amplify_video/1834938050666729472/vid/avc1/1280x720/r8KuMnpqJoDarkn_.mp4?tag=16
I bought a Laser printer, toner is WAAAAY better for the average person. I only print something once or twice a month. Toner doesn't dry out. It just works, and the text is crisp! Fricken Lasers!

Does anyone know why "zaps sent" and "sats sent" are different values? When sending through Nostr it's called Zapping right? There's no difference? #NostrHelp #noStrudel 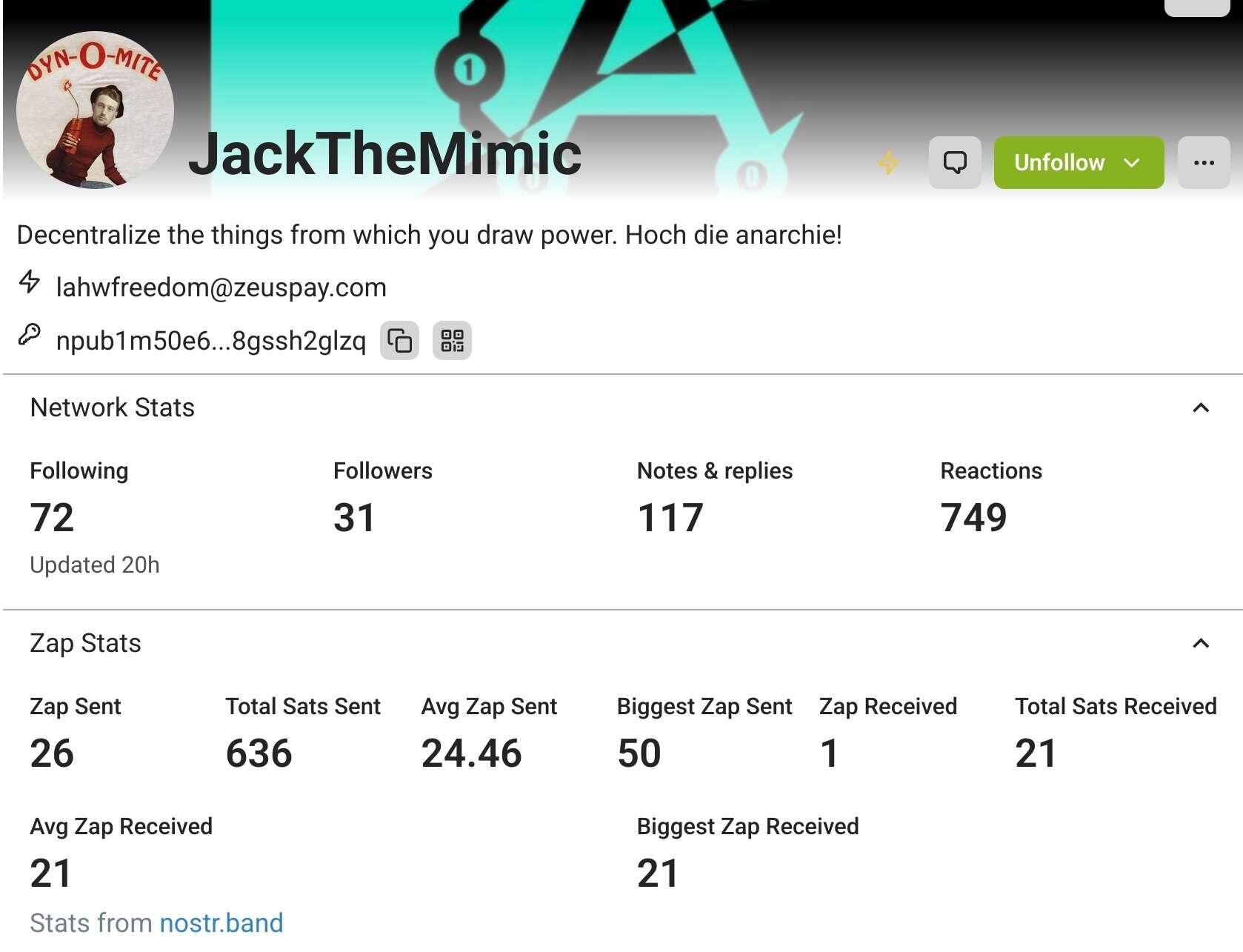
Can anyone explain to me why we still have DNS when IPv6 has so many unique ip addresses and we can have rated aliases like on the lightning network? Once you confirm the official IPv6 of the desired server and cache it locally why do we need DNS?
So we don't get copycat aliases? Even then a simple reputational alias aggregator solves that. Can anyone explain why I can't host my own server and serve content through my own "domain" (.com and the like wouldn't even be neccesary anymore) without having to deal with a registrar?
#NostrHelp someone #PleaseExplain 
But you repeat yourself, just with a euphemism.
I don't see this as self-censorship. If you value spam and others don't they are not your WoT. Your follows are your business. If someone unfollows you, it does nothing to your speech other than to signal you are not saying/doing things they like. If you speak only with the goal of pleasing everyone you are doomed to fail.
I am not entirely certain what that means. Is that anything like Hidden services?
Don't pull the ladder up after you. Create a video or note describing the problem and how you fixed it. More people give up and live with the buggy software than do what you just did. We need more blogs or videos titled "[My exact problem and fix for this software.]"
Testing an old idea: NFC-based transient accounts: accounts that log off as soon as the app goes to the background, deleting all traces of the account from the phone.
It looks like this in debugging speeds: https://video.nostr.build/ef4274d150303fd28f5e7b6b02a7b0102176263dfb1b491969a0caab6b61e6ad.mp4
If you are an activist and if your phone is confiscated, they will never find anything on the phone. Not even your public key.
Walk around with Amethyst installed and an NFC tag hidden in your clothing. When you need to use Amethyst, tap the tag, insert your password and login. Lock the screen to delete everything.
The NFC has a NIP-49 password-encrypted nsec. If you need, destroy and dispose the NFC tag.
This Cypherpunk future is going to be awesome.
There was something I didn't quite understand about Merkle trees, and the first 5 webpages I looked at glossed over it. Finally I found my answer at this page, which I now consider a good resource for anybody wanting to understand Merkle trees:
https://www.derpturkey.com/merkle-tree-construction-and-proof-of-inclusion/
Thank you for leaving the ladder so we can climb up too.
I felt a similar way. I often find new tech, try it out, find a perceived flaw, and suggest a fix or work on it myself. If such investors cared about the stuff I do, I would have a similar meme made about me. Seems a bit like a "Trust the experts" type attitude. Results will show the work.
How does everyone find something to talk about every 20-30 minutes? Is the need to shout into the aether THAT strong? Yet here I am, again...
Some interesting comments about IPFS: https://news.ycombinator.com/item?id=37750529
Basically all people who have used it realized it wasn't working, but those who were heavily invested on it used their cognitive dissonance to reframe it as "good for internal networks" or to say that "now it is going to get better".
It seems like they are simply missing an incentive structure. 2 sats to stream content from a source. 1 sat is the content ID originator, the other sat goes to the host. Host your own, 2 sats, host someone else's, 1 sat each.
The chance to win is not a probability of finding a 256 bit number it is a range less than that. Also, the chances of mining a block is deterministic based on the participant computational load. This means if you were the only miner for 3 weeks you would find a block every 10 minutes with a bitaxe. It feels like you don't actually understand the probabilities here.
This year's seafood boil is a go! nostr:nprofile1qqs2wguqtndxwfg3j8y8sm6d5k8hjlnfwavzxqf4fw5wjx7tqdpde8qpp4mhxue69uhkummn9ekx7mqpr9mhxue69uhhqatjv9mxjerp9ehx7um5wghxcctwvsq3qamnwvaz7tmwdaehgu3wwa5kueglejxr7 nostr:nprofile1qqsptssu6n4pvsjxth30na0llrnpa4u8x52cv4jtke9j5uvm77ldvvspr9mhxue69uhhyetvv9ujuumwdae8gtnnda3kjctv9unmkwy6 #NostrBoil https://v.nostr.build/FVaxTEfuwgBeZ7h5.mp4 
 https://v.nostr.build/XpFpsr7ykcfUsrNo.mp4
https://v.nostr.build/XpFpsr7ykcfUsrNo.mp4
1. Y'all need more table for that feast.
2. OLD BAY, I mean what are we doing here?


