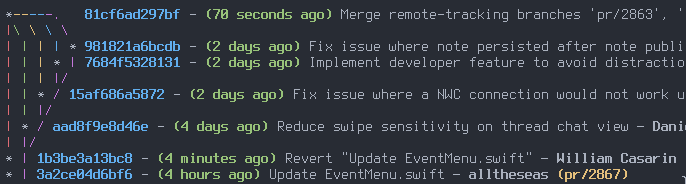
I haven’t looked into promenade so not sure on that.
if I’m understanding your question correctly with Frostr you can configure basic permissions on a given share within signing client (send / receive / both) meaning it has permission to either send a request to another share for sig, only receive requests, or both.
This effectively allows you to have a “third-party“ share (receive only) that you could give out to different clients/services for signing
nostr:npub1gg5uy8cpqx4u8wj9yvlpwm5ht757vudmrzn8y27lwunt5f2ytlusklulq3 I get this right?
I don't understand the receive/send distinction and why it's important. Is it just that you want certain shards to be passive and unable to initiate requests because they're in an untrusted context? This seems like it could be a nice complement to the usual pattern of nagging the user about every permission request.
On promenade, I highly encourage you to check it out: https://git.fiatjaf.com/promenade
It's currently used by https://start.njump.me to encourage new users to get started with a multisig bunker, without having to set up any signer software on their end. This seems pretty close to the ideal of abstracting away keys for new users without compromising security too much.
If we get key rotation, simplier coordination, and/or encryption using frostr, that's an improvement over promenade. But third-party shard custodians have to be plugged into the nostr social layer via NIP 89 so that we can avoid collusion of dishonest signers.
Demo of the new "Git repo tracker" feature I added to #Flotilla in [BudaBit club](https://budabit.club) .
https://v.nostr.build/FUejC8ryM37liSlE.mp4
- Start tracking repositories
- View latest issues and statuses
- Jump to #Gitworkshop by nostr:nprofile1qqs2qzx779ted7af5rt04vzw3l2hpzfgtk0a2pw6t2plaz4d2734vngpzamhxue69uhhyetvv9ujumn0wd68ytnzv9hxgtcppemhxue69uhkummn9ekx7mp0qy2hwumn8ghj7un9d3shjtnyv9kh2uewd9hj7hycrvd for detailed view
- Start a "threads" discussion on any issue
- Start Threads now also supported in "Jobs" tab
Enjoy!
#git #grownostr
Dude, this is fantastic. Nice work! I love seeing my stuff get forked to scratch an itch.
TURN YOUR NSEC INTO A ROTATABLE MULTISIG WITH FROSTR
This is a demo of our first two signing clients Frost2x & Igloo converting an nsec into a Frostr keyset and signing a note in nostrudel
FROSTR IS STILL UNDER DEVELOPMENT, ALL CODE IS OPEN SOURCE, PLEASE POKE HOLES IN IT AND BE ADVERSARIAL https://frostr.org
Can you compare/contrast this with fiatjaf's promenade project? Can frostr be reconfigured to support third-party shard custody? It would be great to solve key management and rotation without users having to learn how to do it (at least to start). Short of collusion between providers, I would imagine custodial shards would be pretty safe.
New Coracle release: 0.6.6
- Show complete website/lnurl
- Scan images for sensitive content
- Make muting on feeds more strict
- Apply muted words to nip05
- Fix list editing
Nutzaps is probably a better solution
Probably not a good idea, anyway way more than I want to take on right now
I get exactly the same behaviour as you describe it. I am on Android... So yeah definitely an ongoing bug. nostr:nprofile1qyvhwumn8ghj76rzwghxxmmjv93kcefwwdhkx6tpdshsz9thwden5te0xyerwt3s9cczuvf6xsurvwf0qy2hwumn8ghj7un9d3shjtnyv9kh2uewd9hj7qgwwaehxw309ahx7uewd3hkctcpvemhxue69uhkv6tvw3jhytnwdaehgu3wwa5kuef0dec82c33wpaxx63c09n8xvmt0qe8g6r5dfc85vmpvaeryae4x3kn2vntwcukzv3exvehxmt3096rvm3kdve8zmpnv9cnyepswak8s0mzwfhkzerrv9ehg0t5wf6k2qpqjlrs53pkdfjnts29kveljul2sm0actt6n8dxrrzqcersttvcuv3qxg99x3 does it already exist as a bug report?
This should be fixed on web, I'll release a new Android version today
I’m sad https://github.com/nostr-protocol/nips/pull/851 never got merged. We built a nostr.wine NWC service that relied on this improved onboarding flow in December of 2023. At the time Mutiny was leading the effort.
I don’t understand why it wasn’t merged then when we had 4 working implementations. It is the only reasonable NWC on-boarding flow I’ve seen for services (like nostr.wine).
Gotta nag the maintainers, there are 1000 open PRs. Looks like nostr:nprofile1qywhwumn8ghj7un9d3shjtndw46xjmnewaskcmr9wshxxmmd9uq3wamnwvaz7tmjv4kxz7fwwpexjmtpdshxuet59uq3uamnwvaz7tmxv4jkguewdehhxarj9e3xzmny9acx7ur4d3shyqg3waehxw309ahx7um5wgh8w6twv5hsz8thwden5te0wfjkccte9e3x2mn5dpjkxctjd4skutnrdakj7qpqu8lnhlw5usp3t9vmpz60ejpyt649z33hu82wc2hpv6m5xdqmuxhsys5fsc was going to do some additional work and forgot about it.
I totally respect that, microsoft is evil but the vendor lock in is strong. I'll look into finally getting started with ngit. In the meantime, feel free to @ me with issues here. Individually is probably easier.
Pretty neat VR NIP 29 client in development by nostr:nprofile1qy88wumn8ghj7mn0wvhxcmmv9uq32amnwvaz7tmjv4kxz7fwv3sk6atn9e5k7tcpr4mhxue69uhkummnw3ezucnfw33k76twv4ezuum0vd5kzmp0qyvhwumn8ghj7am9d33k7mt99ehx7um5wgh8w6twv5hsz9nhwden5te0wp6hyurvv4ex2mrp0yhxxmmd9uqzqpf863mj6ntr6lwm6nyshgcq4wyyvk6qqc9jyy5pksmnpa9ganz7d23h0k: https://github.com/visiondevcamptokyo/devcamp/
Ah, the good old "failed successfully" standby. Did the DVM request get sent? If so, it's pablo's fault
coracle, aka "nostr web"
I am the developer of coracle.social, so you might give that a try. Amethyst on Android and Damus on ios are the most popular mobile apps. 0xchat is very nice for DMs and chat.
Individually via github would be best
Nope, just an idea so far
Luckily most of these tools are highly targeted. The use of them doesn't break nostr's user-centric nature either, so I don't think it will actually result in meaningful centralization
There's also this though, which is relay based:
Maybe an image server could whitelist npubs. Otherwise you're describing a community relay, it seems. nostr:nprofile1qqsf03c2gsmx5ef4c9zmxvlew04gdh7u94afnknp33qvv3c94kvwxgsppemhxue69uhkummn9ekx7mp0qy2hwumn8ghj7un9d3shjtnyv9kh2uewd9hj7qgewaehxw309a5xyu3wvdhhyctrd3jjuum0vd5kzmp0gankr4 and some others focus on this use case.
CC nostr:nprofile1qqsfnz2sqsflkatdssmeztxr90s8xrd7r07xkhfwaa6eu9zkcguljpgpz4mhxue69uhkummnw3ezu7rdwgh8ymmrddesz9thwden5te0wfjkccte9ekk7um5wgh8qatzqyv8wumn8ghj7un9d3shjtnndehhyapwwdhkx6tpdskdh679 nostr:nprofile1qqs04xzt6ldm9qhs0ctw0t58kf4z57umjzmjg6jywu0seadwtqqc75spz4mhxue69uhhyetvv9ujuerpd46hxtnfduhsz9mhwden5te0wfjkccte9ec8y6tdv9kzumn9wshszxnhwden5te0wpuhyctdd9jzuenfv96x5ctx9e3k7mf0dv4ph5 for the image server whitelist.
Cryptography may be able to solve this use case too
That's the neat part, we don't
Is this the git version of consolidating utxos? Honestly didn't know you could do this.
Can you update the NIP-89 app handler event for nostr:npub13myx4j0pp9uenpjjq68wdvqzywuwxfj64welu28mdvaku222mjtqzqv3qk to support kind 30402 events. There aren't any apps that say they can handle listing events yet 😞
I don't really want to encourage people to use coracle for these, since I've removed a lot of support for them nostr:nprofile1qy2hwumn8ghj7am0deejucmpd3mxztnyv4mz7qg3waehxw309ahx7um5wgh8w6twv5hszrnhwden5te0dehhxtnvdakz7qgkwaehxw309a5xzan9dchxxctvwesjuer9wchsz9nhwden5te0v4jx2m3wdehhxarj9ekxzmny9uqzp5mwszpl57ekmthxgm9ck0uel64rmz095wt9pp6p7qp7yxkqk6lv9lxeyl is there a NIP 89 handler for shopstr?
- I could only upload one image at a time
- I couldn't find a way to copy the naddr of the listing or otherwise share it to nostr
- I had a hard time finding the "create listing" button
- The currency code you're using for sats is SATS, when it should probably be SAT
Check it out, you can now buy Coracle shirts on nostr!
This is the scariest image in existence
Instagram didn't always look like instagram. You might enjoy the next episode of the nostr:nprofile1qydhwumn8ghj7un9d3shjtnhv4ehgetjde38gcewvdhk6tcppemhxue69uhkummn9ekx7mp0qyw8wumn8ghj76r0v3kxymmy9e3k7unpvdkx2tn5dahkcue0qy2hwumn8ghj7un9d3shjtnyv9kh2uewd9hj7qgcwaehxw309ashgtnwdaehgunhdaexkuewvdhk6tcqyr0lrkrc8xjjuw0l5ehevvfljxcgwdx54nxeemx8r4u0ct42wxtr5xfzv0e in which nostr:nprofile1qyd8wumn8ghj7urewfsk66ty9enxjct5dfskvtnrdakj7qghwaehxw309aex2mrp0yh8qunfd4skctnwv46z7qg4waehxw309aex2mrp0yhxgctdw4eju6t09uqs6amnwvaz7tmxxaazu6t09uqkvamnwvaz7tmxd9k8getj9ehx7um5wgh8w6twv5hkuur4vgcny734deuk6vr3dduxserjwekhj6r4wqexcmr6wqunsmrj09erxwr8wuu8jamcdd6xkurn89jhzer5wvmkzum2dgukkwtr8a38ymmpv33kzum58468yat9qqs04xzt6ldm9qhs0ctw0t58kf4z57umjzmjg6jywu0seadwtqqc75sm7lh06 and I talk about this very thing.
SAME
Speaking of which, this may be relevant to your interests:
In a security loop nostr:nprofile1qqsvwct7ssehccgu040egxe4k8k9ru4wd605r2kfv9sf94gsu8pftcqpr9mhxue69uhhyetvv9ujuumwdae8gtnnda3kjctv9uqsuamnwvaz7tmwdaejumr0dshs8we63u
Lost my iphone
All paths end in: 
Wish I could use public private nostr key and cut thru this.
HELP?
This happened to me as well
Thinking about how to add push notifications to flotilla for closed communities — since push notifications have to be sent from a server, I need some way to get access to auth-gated content. The simple way to do this would be to just share the user's own session with the push server, but for obvious reasons that's a no-go.
The cleanest solution I can think of would be to allow an active NIP 46 session to delegate permissions to another session. All I really need is authorization to sign a `22242` event on behalf of a user.
Below is a draft NIP that introduces a `delegate` method to NIP 46 which "locks" the delegated session to the initially requested permissions:
The pattern is really weird in isolation, but it makes sense for use cases like portals and modal dialogs.
It worked in svelte 4 because this is just how javascript works. It seems like svelte 5 is trying to re-implement garbage collection by undefining props on unmount. Svelte 4 just used javascript for state management — even though there was some compiler magic with stores that get `unsubscribe` called automatically, it was basically relying on the javascript VM's garbage collector to avoid memory leaks. I suspect something about runes makes this more difficult.
My site currently generates personalized PageRank and GrapeRank scores in nostr:npub1gcxzte5zlkncx26j68ez60fzkvtkm9e0vrwdcvsjakxf9mu9qewqlfnj5z's NIP-85 format. The export function hasn’t been stress tested yet by more than a handful of users, but nostr:npub1xdtducdnjerex88gkg2qk2atsdlqsyxqaag4h05jmcpyspqt30wscmntxy has also generated PageRank scores using NIP-85, which means we’re (hopefully) soon going to start seeing clients put these scores to good use.
The question is which client is going to be the first!
Make a DVM and it'll automatically be everywhere
Just spending the day thanking people whose work I've benefited from. nostr-editor is the bomb and I'm grateful for it 🫂
nostr:nprofile1qyfhwumn8ghj7ur4wfcxcetsv9njuetn9uq3zamnwvaz7tmwdaehgu3wwa5kuef0qy08wumn8ghj7mn0wd68yttsw43zuam9d3kx7unyv4ezumn9wshsz9thwden5te0wfjkccte9ejxzmt4wvhxjme0qyt8wumn8ghj7cn9wehjumn0wd68yvfwvdhk6tcqyrdp36vxqpq0806f8pm0c9434yf2ukn0d75d29vu8h3tsge6pkv9z0wp47z dvmdash.live seems to be timing out for me
Right. But FYI, you don't need microsoft's service, you can roll your own with open source models that will return a confidence score between 0 and 1. And a lot of those models are totally open source -- https://huggingface.co/docs/transformers/en/tasks/image_classification They are just classification models which return a value between 0 and 1. And they're pretty fast & efficient since Google and other have been fighting this issue for 20+ years and have developed very good and efficient models. (Which work 99.5% of the time. I think it's impossible to get to 100%).
It's a totally different approach, but maybe you're right, good LLMs are relatively new and maybe could be considered to supersede fuzzy hashing. But the main problem of reverse-engineering the compression algorithm (which is one way to think about llms) still exists. If you're thinking of working on this I'm happy to see what I can do to help.
Right, that's basically how microsoft's product works. They don't release the database because you could then craft images that foil the fuzzy hashing algorithm they use.
OK so it would be a "label" event, with a score: https://github.com/nostr-protocol/nips/blob/master/32.md -- great. So, question is, will any clients actually want to consume/use these labels?
NIP 56 would be better, but do not do this.
#asknostr among the problems that Nostr faces, the child porn problem is a very, very, very bad problem.
A VERY bad problem.
What is the current thinking among developers about how to deal with this?
Nobody likes censorship, but the only solution I can think of (SO FAR) is running an image identification service that labels dangerous stuff like this, and then broadcasts a list of (images, notes, users?) who are scoring high on the "oh shit this is child porn" metric. Typically these systems just output a float between zero and 1, which is the score....
Is anyone working on this currently?
I have a good deal of experience of running ML services like image identification at scale, so this could be something interesting to work on for the community. (I also have a lot GPU power, and anyway, if you do it right, this actually doesn't take a ton of GPUs to do even for millions of images per day....)
It would seem straightforward to subscribe to all the nostr image uploaders, generate a score with 100 being "definite child porn" and 1 being "not child porn", and then broadcast maybe events of some kind to relays with this "opinion" about the image/media?
Maybe someone from the major clients like nostr:npub1yzvxlwp7wawed5vgefwfmugvumtp8c8t0etk3g8sky4n0ndvyxesnxrf8q or #coracle or nostr:npub12vkcxr0luzwp8e673v29eqjhrr7p9vqq8asav85swaepclllj09sylpugg or nostr:npub18m76awca3y37hkvuneavuw6pjj4525fw90necxmadrvjg0sdy6qsngq955 has a suggestion on how this should be done.
One way or another, this has to be done. 99.99% percent of normies, the first time they see child porn on #nostr ... if they see it once, they'll never come back.....
Is there an appropriate NIP to look at? nostr:npub180cvv07tjdrrgpa0j7j7tmnyl2yr6yr7l8j4s3evf6u64th6gkwsyjh6w6 ? nostr:npub1l2vyh47mk2p0qlsku7hg0vn29faehy9hy34ygaclpn66ukqp3afqutajft ? nostr:npub16c0nh3dnadzqpm76uctf5hqhe2lny344zsmpm6feee9p5rdxaa9q586nvr ?
Broadcasting public notes that identify CSAM is probably illegal, because it could be construed as "advertising" that content. I think the only option we really have long-term, at least in the US, is for someone(s) to run a service that crawls the network, matches images against microsoft's hash database product (closed source, but for good reasons, since hash databases can be reverse engineered), and reports matches to NCMEC. A bonus would be to do the same thing but analyze note text for exploitation keywords. Privately hosted and encrypted content are pretty much immune to this fortunately/unfortunately. nostr:nprofile1q9n8wumn8ghj7enfd36x2u3wdehhxarj9emkjmn99ah8qatzx96r2amr8p5rxdm4dp4kzafew3ehwwpjwd48smnywycrgepndcu8qd3nx36hguryvem8xdr5d56hsmt5xfehzemtxejxkeflvfex7ctyvdshxapaw3e82egprfmhxue69uhhyetvv9ujumn0wd68yanfv4mjucm0d5hszrnhwden5te0dehhxtnvdakz7qg3waehxw309ahx7um5wgh8w6twv5hsz9nhwden5te0wfjkccte9ekk7um5wgh8qatz9uqzpxvf2qzp87m4dkzr0yfvcv47qucdhcdlc66a9mhht8s52mprn7g98p5le2 currently checks a hash database for all images uploaded, and I believe they report matches.
As non-cypherpunk as this all is, I think it's the only real option we have unless Ross Ulbricht's ZKANN idea gets built. We need to demonstrate to anyone watching that we take the problem seriously and take measures to self-regulate. This is similar to the bitcoin KYC/AML argument. If we don't want financial surveillance or legal restrictions on social media, we should help law enforcement actually chase down the people who are the problem rather than presenting ourselves as the scapegoat. See iftas.org for some work being done in the fediverse on this.
It is so exciting to me to see my vision for coracle actually happen. For a variety of reasons coracle is just not quite what I've always been going for.